At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
May 3, 2020

Binding to LDAP with Minimum Access
Most of the documentation out there will tell you to configure a Domain Admin user to perform LDAP authentication. When I am doing a Proof-of-Concept (PoC), and I tell a prospective customer to create me a Domain Admin user, I usually get a sigh and some evil eyes. Sometimes this could be because a different group is required to create that user and sometimes it is a process and has regulatory impact. Either way, I wanted to set the records straight
Minimum User in AD
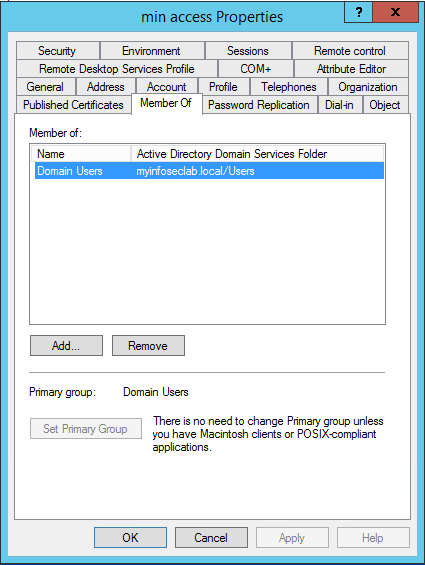
I created a normal user named minaccess . This user, as you can see, is ONLY a member of Domain Users .
I used a user in AD to test the authentication named blevy and yes, this is a real person name Bryan Levy. I populated my fake lab AD with people I know so that I could remember their names. So Bryan, here is you 2 seconds of fame.
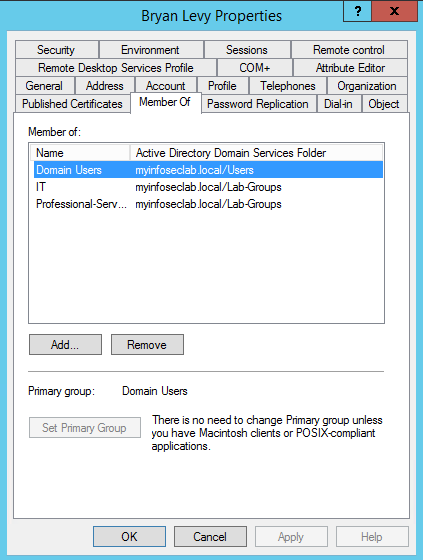
As you can see, he is a member of Domain Users , IT and Professional-Services although his membership is irrelevant for this test. The relevant user access and membership is minaccess above.
FortiGate LDAP Server
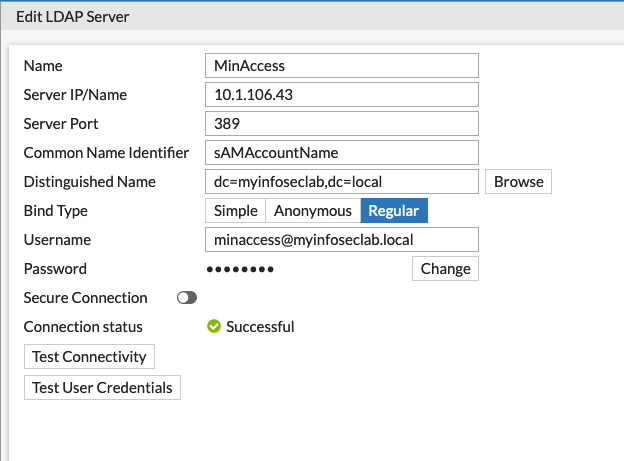
Here we can see the LDAP server configuration. You can see that I am using minaccess@myinfoseclab.local as the user to bind to LDAP. I tested connectivity and it was Successful
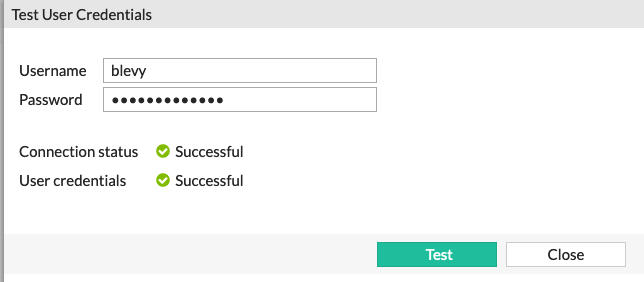
Next, I ran the Test User Credentials and used the blevy account. We see that the user credentials test came back as Successful
I tested the VPN using the minaccess user binding to LDAP and blevy as the user connecting to the VPN.
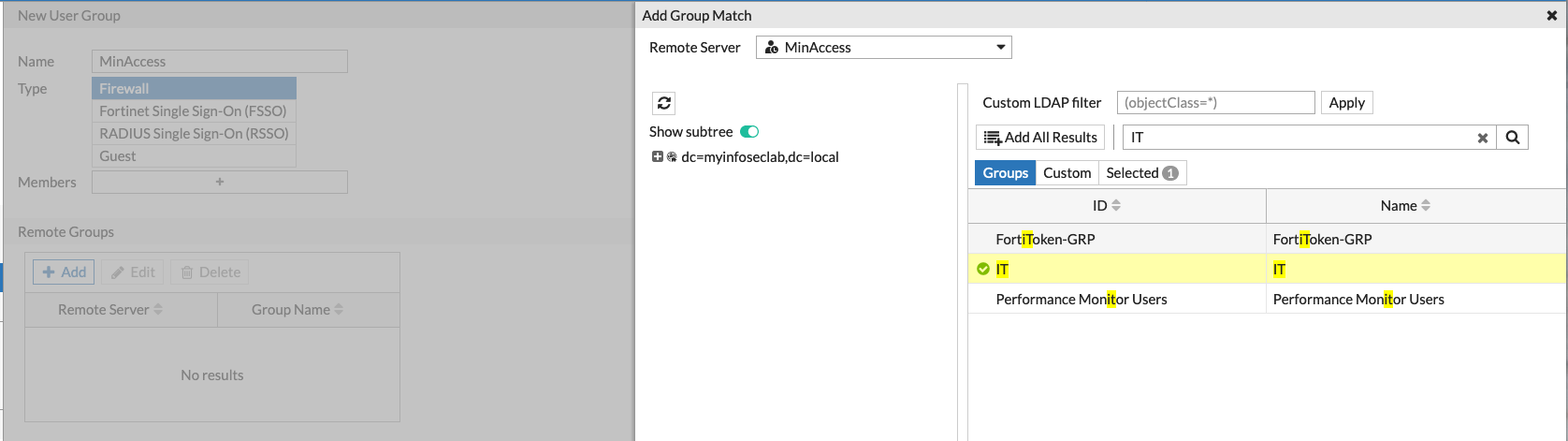
Here you can see that I created a User Group named MinAccess and tied it to the LDAP server I created. I chose the IT group since the user blevy was a member of it.
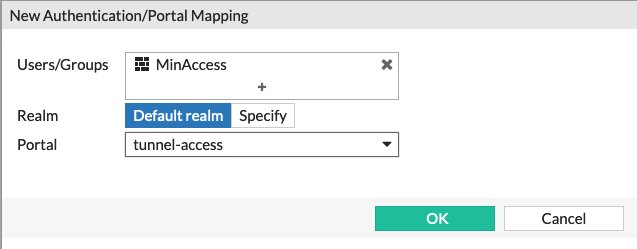
Added the newly created user group to the SSL-VPN Settings section of the FortiGate.
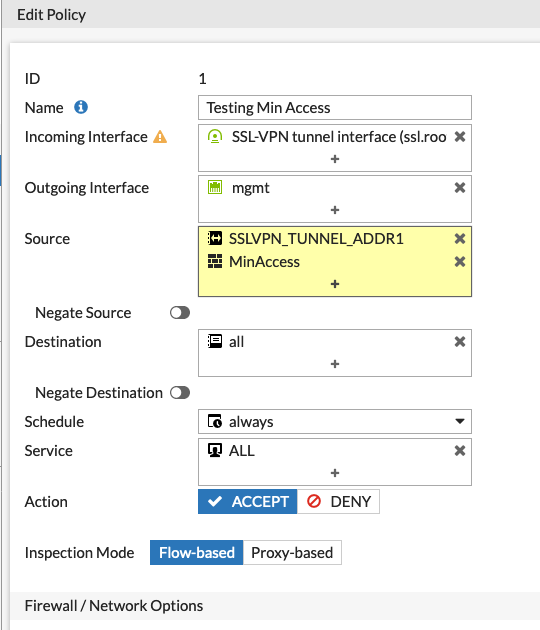
Modified the policy allowing the MinAccess group to the Policy. And tested.
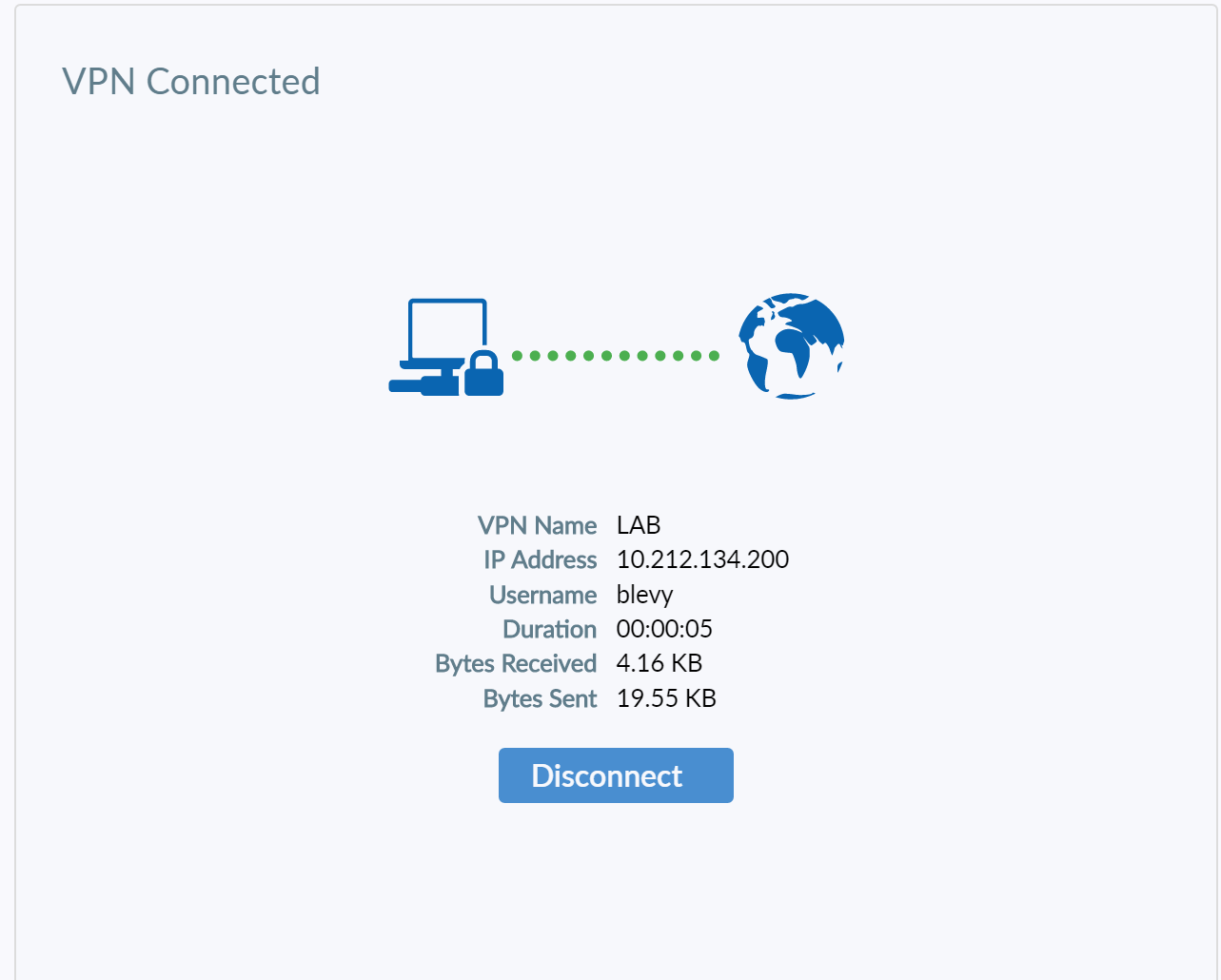
Success !!!!!
Hope this helps
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
