At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
May 26, 2024

Cisco Wildcard Objects in FortiOS
Recently, I was working with a customer that had a lot of Cisco wildcard addresses in access-lists they were using for both firewall rules as well as route-maps. To create these on the FortiOS, you need to do it via the CLI only.
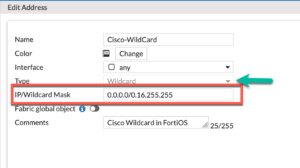
From the cli, type the following command config firewall address this will get you to the addresses section. You will need to create a new entry by typing the keyword edit followed by the name of the object you want to create, in my example Cisco-WildCard.
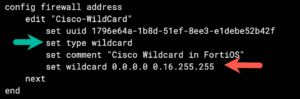
config firewall address
edit Cisco-WildCard
new entry 'Cisco-WildCard' added
set type wildcard
set wildcard 10.0.0.0 0.16.255.255
set comment "Cisco Wildcard in FortiOS"
end
This object can be used in various locations of the FortiGate such as Firewall Policies .
Sometimes it is tricky to understand what you are letting in or blocking based on these wildcard addresses. When I was a big Cisco guy I used some pretty crazy ones. When creating FortiOS access-list for routing, you can enter the Wildcard mask directly into those sections.
I use sipcalc with Homebrew on my macOS.
[CIDR]
Host address - 10.1.0.0
Host address (decimal) - 167837696
Host address (hex) - A010000
Network address - 10.1.0.0
Network mask - 255.255.255.224
Network mask (bits) - 27
Network mask (hex) - FFFFFFE0
Broadcast address - 10.1.0.31
Cisco wildcard - 0.0.0.31
Addresses in network - 32
Network range - 10.1.0.0 - 10.1.0.31
Usable range - 10.1.0.1 - 10.1.0.30
As you can see above, the wild card is 255-%the-masked-bits% (255-224=31)
Hope this helps
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
