Have you ever ordered a bunch of Fortinet gear... Full Story
By Manny Fernandez
May 7, 2024
Converting FortiGate CLI packet debug to PCAP file on macOS
Years ago, when I started using FortiGates, I had a Windows VM where I could run some utilities and so forth. However I have since gone full macOS for the past 12 years. There is a great article on the Fortinet site explaining how to perform a packet capture on FortiOS using a verbosity level of 3 or 6. This gives you the opportunity to copy the output into a file, run a perl script against it and generate a .pcap file for further analsys.
Here is a link to the original document. If you download the file at the bottom of the page fgt2eth.pl.zip
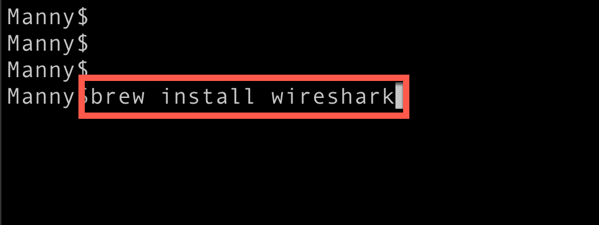
On macOS, you will need to have home brew installed. Once you install Home Brew, run the following command to get the cli version of wireshark
Once this has completed, you can chmod +x the fgt2eth.pl file. I recommend moving the fgt2eth.pl to a folder in your path statement set . On my system, I chose /opt/home brew
Remember to use the -in for the source of the file and -out for the path where you want the file to be stored. If you leave out the -out, it will use the current directory (You can use pwd to display the current directory if not part of the prompt).
fgt2eth.pl -in ~/Desktop/diadebug.txt -out /Users/fernandezm/Desktop/remot e.pcap
In my example, I used the above command.
Hope this helps.
Recent posts
-

-

Had a customer with over 200 static routes on... Full Story
-

This is a work in progress, I will be... Full Story
