Have you ever ordered a bunch of Fortinet gear... Full Story
By Manny Fernandez
August 7, 2020

Dynamic DNS Split-Tunneling for FortiGate VPN
Today I had a partner reach out to me about Cisco’s Dynamic Split Tunneling using AnyConnect. Apparently this is a new feature they released. I did a little research and here is the Fortinet solution. In my opinion, it appears to be more robust than that of Cisco. But that is my opinion.
Use Case:
Customer has a remote access VPN into the corporate environment. They do not want to rely on IPv4 and IPv6 Split Tunneling but rather have an additional component to send traffic directly out to the Internet. Here is the article they sent to me. In the article, they use the example about sending traffic for cisco.com to an external DNS server and other DNS to the internal.
Let’s get started.
First thing we need to do is configured the Spit Tunneling using the legacy way of doing it; using IP addresses and / or subnets.
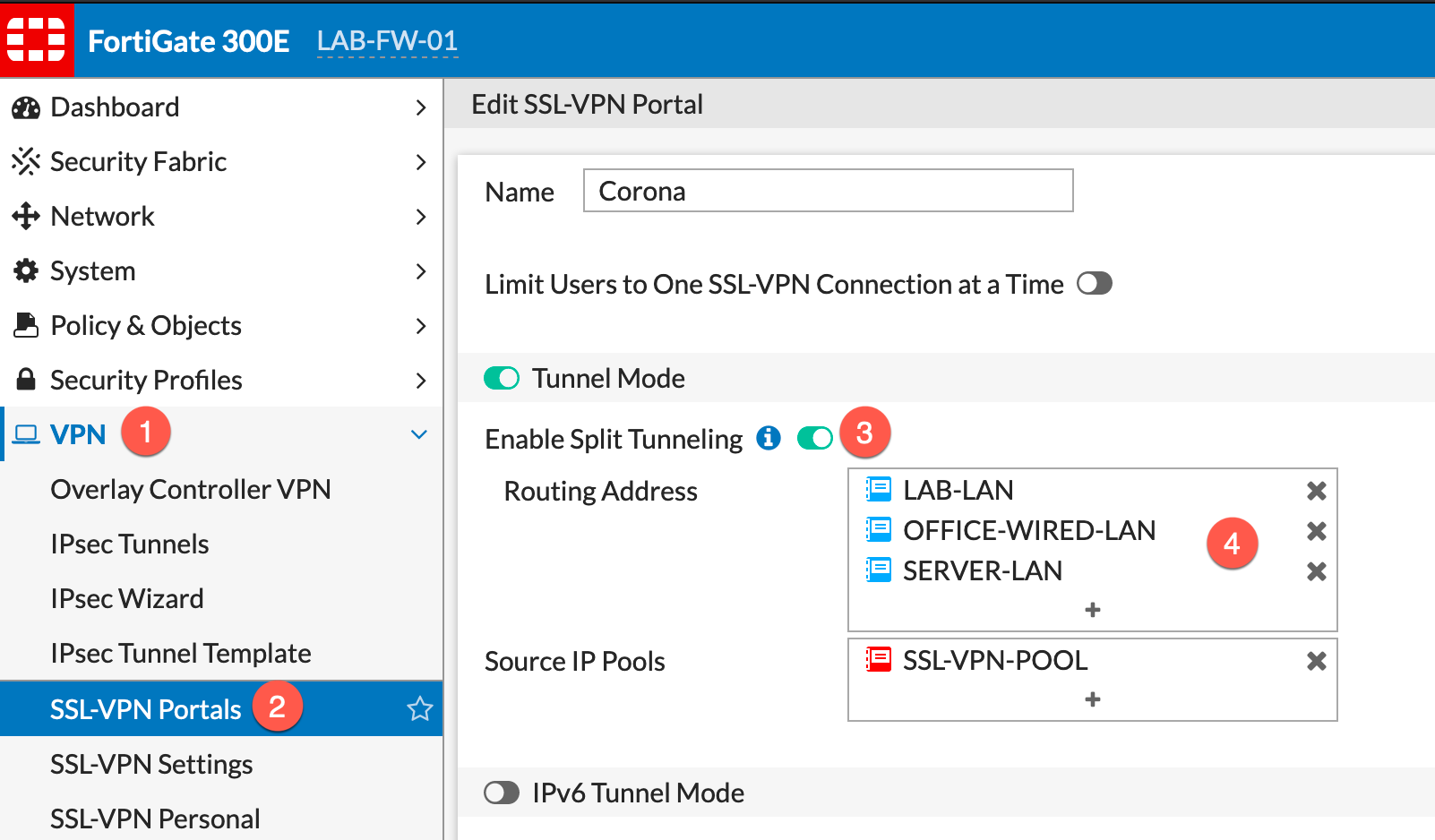
- Go to
VPN - Then choose
SSL-VPN Portalsand edit your portal. - Click the
Enable Split Tunnelingbutton. - Choose your subnets and/or host IPs.
In step 4, you will define what IP addresses and subnets are going to be encrypted and sent to the Fortigate ( Interesting Traffic ).
By the way, this is known as Split Tunneling Enabled.
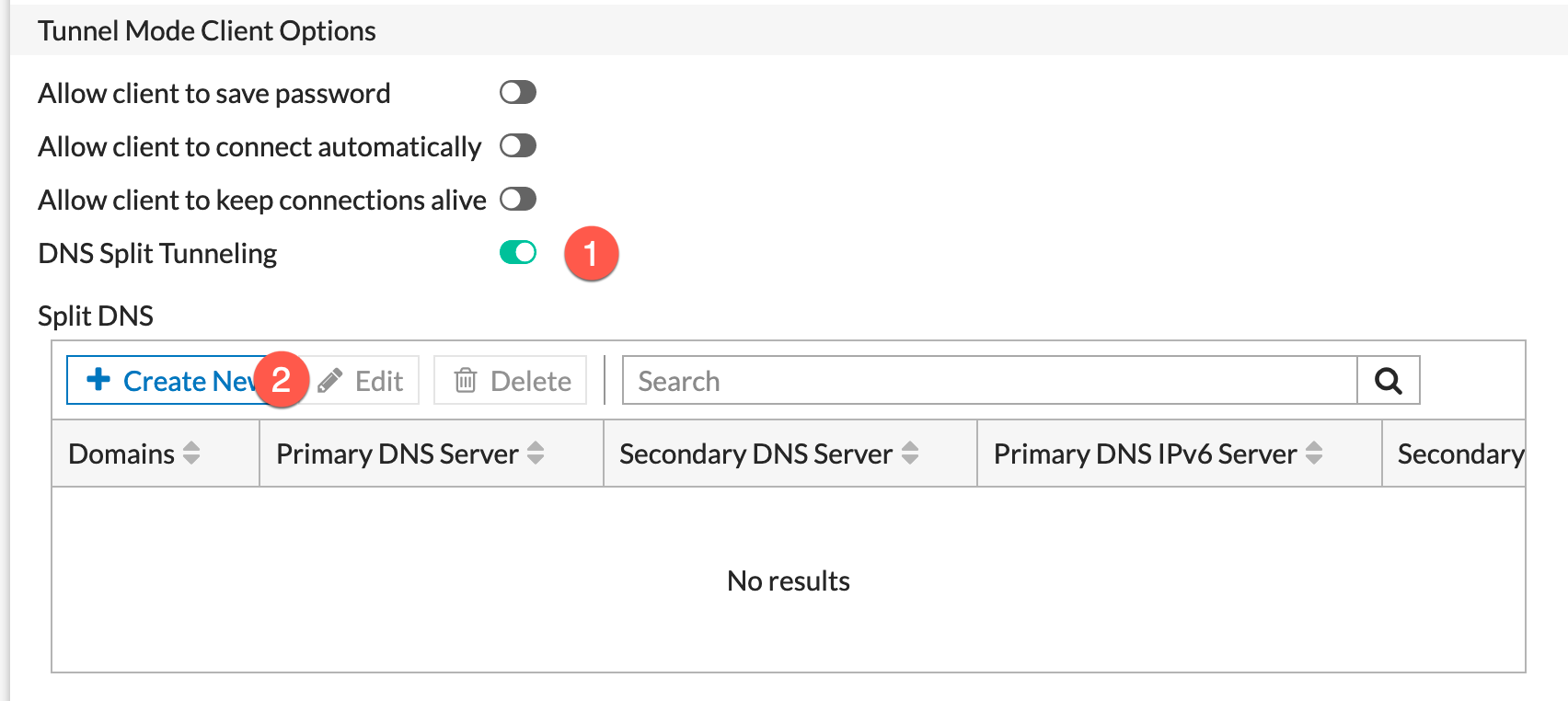
Now you will need to:
- Enable
DNS Split Tunneling - Then we are going to
Create New
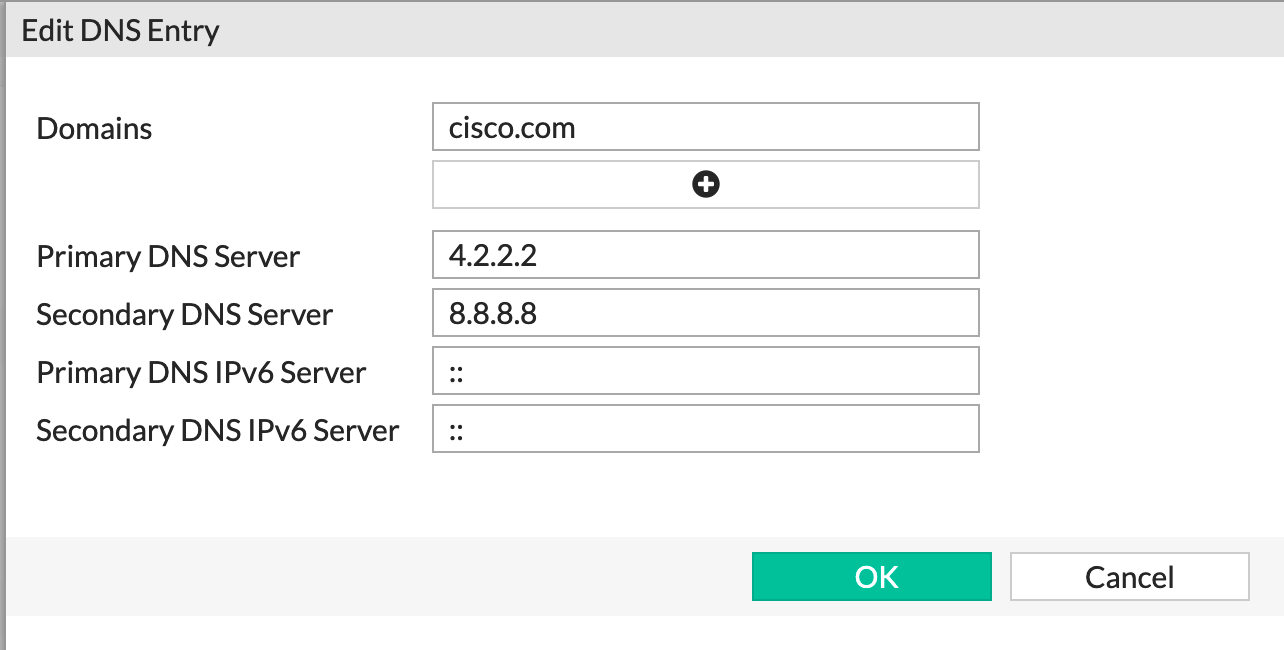
Here we can see that I am sending all DNS queries for cisco.com to 4.2.2.2 and 8.8.8.8
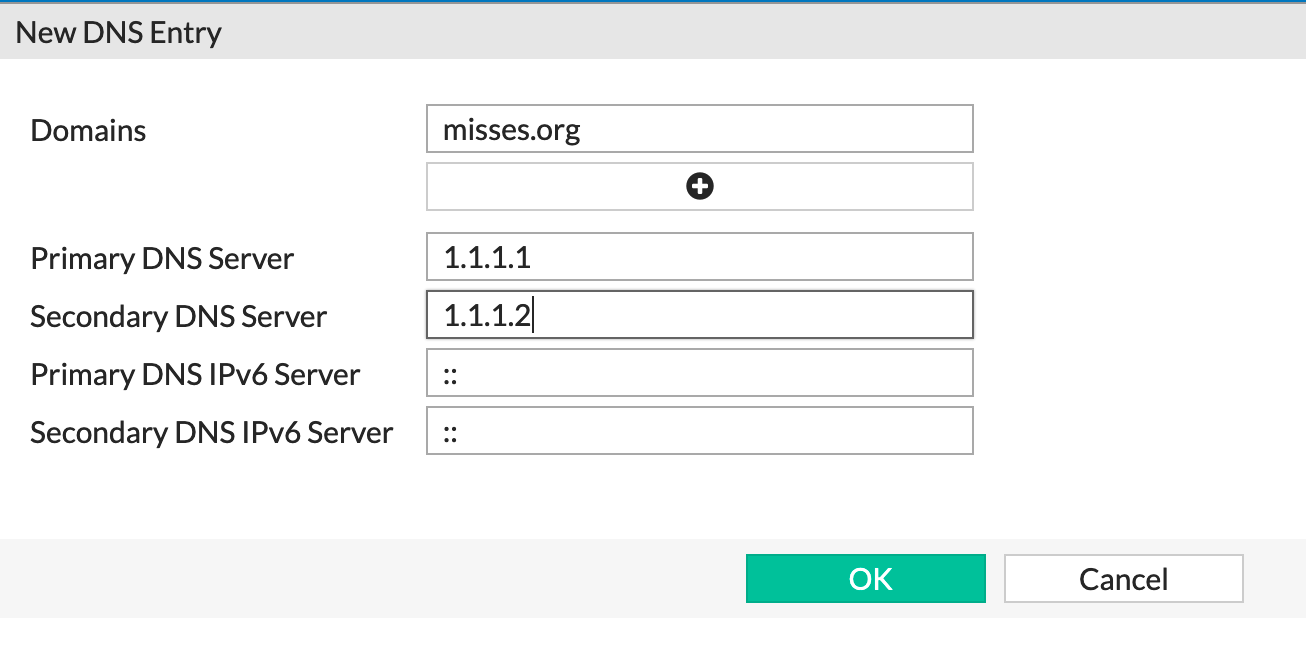
In THIS example, I am sending any DNS queries destined to misses.org to 1.1.1.1 and 1.1.1.2
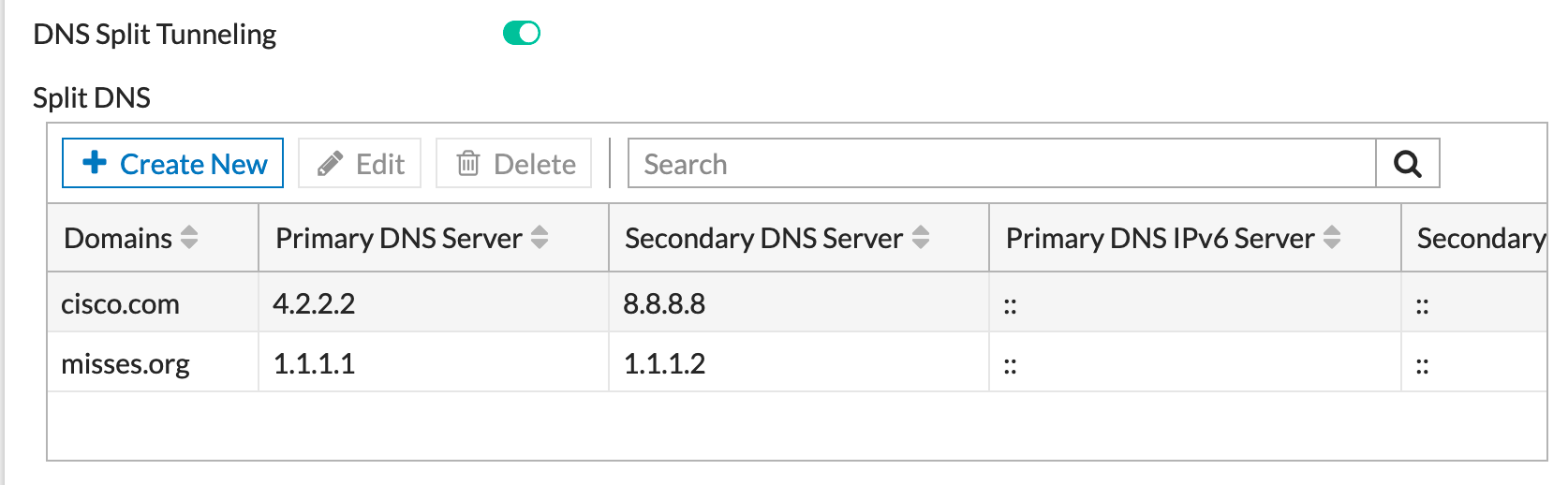
And here we can see that we can add multiple domains and multiple DNS resolvers.
Hope this helps
Recent posts
-

-

Had a customer with over 200 static routes on... Full Story
-

This is a work in progress, I will be... Full Story
