Have you ever ordered a bunch of Fortinet gear... Full Story
By Manny Fernandez
February 20, 2019

Fortitoken with Active Directory on Fortigate
Yesterday I wrote a blogpost about two-factor authentication using Duo, Active Directory, Duo Proxy Auth and Fortigate. I mentioned that FortiToken was easier to deploy and decided I would write a blog post using FortiToken, Active Directory and Fortigate.
Fortigates have a built-in two-factor authentication server and you only need to purchase FortiTokens. FortiTokens come in two-factors (no pun intended); hardware and electronic. The electronic tokens are perpetual so you buy them once and you can reuse them as needed.
What you are going to need:
1. Fortigate Firewall
2. FortiToken Licenses (hardware or software)
3. Active Directory
NOTE: You do not require AD as you can create local users and assign them a token.
Lets get started.
Login into your Fortigate firewall and go to ‘Users & Devices’ then ‘FortiToken‘
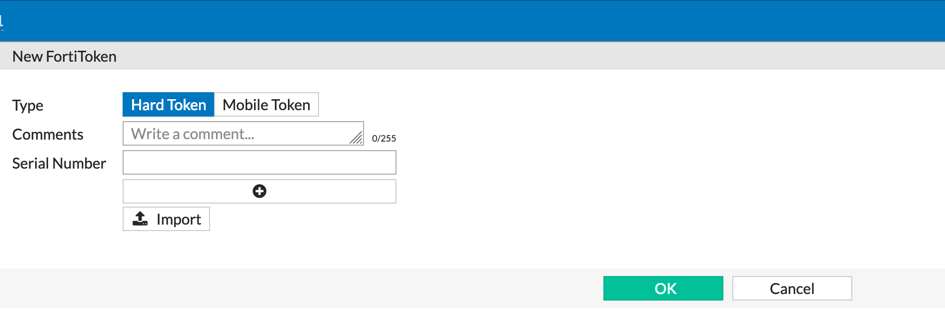
For hardware tokens, you can either import it from a text file or seed file.
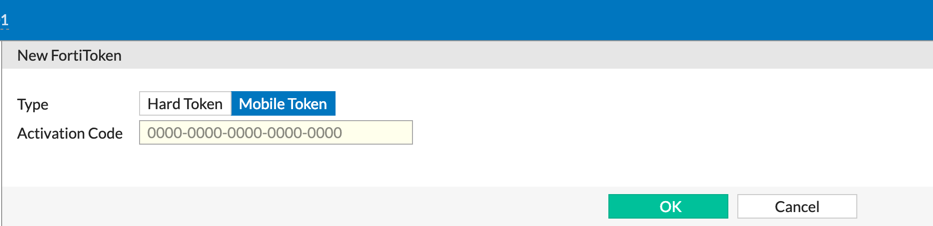
Electronic Tokens are easier. Enter the ‘Activation Code‘ provided by Fortinet via an email and hit ‘OK‘
Once you have the tokens listed, we will add an LDAP server to the configuration. Under the same Sub heading of ‘Users & Devices’ then ‘LDAP Servers’.
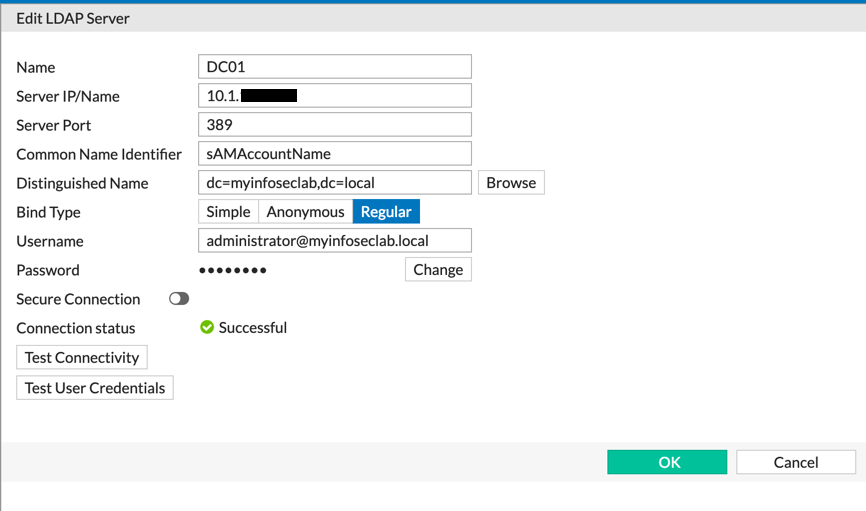
Ensure the ‘Connection Status’ shows up with the green checkmark and says ‘Successful’.
Now we will create a Security Group in Activie Directory
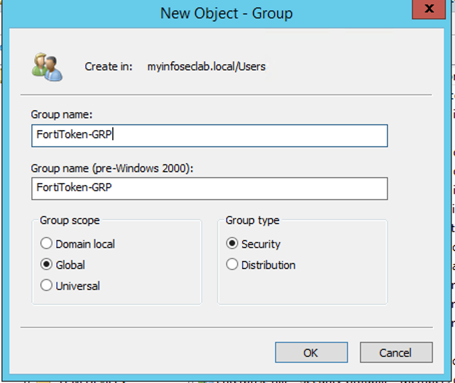
We will also create a test user
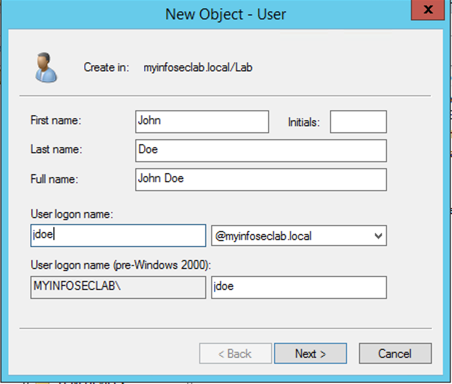
Next, make sure you add the new user to the ‘Security Group’ named ‘FortiToken-GRP’.
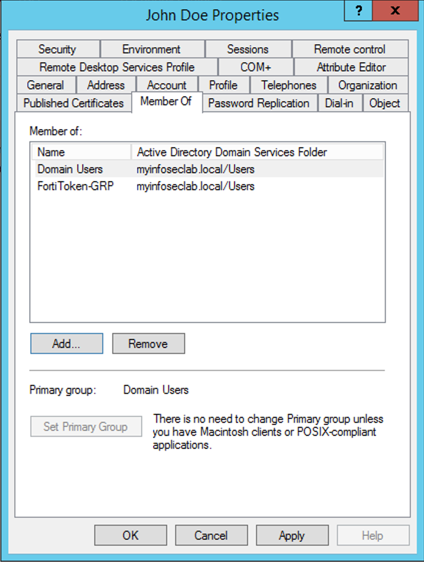
Once this is completed you can move back to the Fortigate. Go back to ‘Users & Devices’ and create a ‘User Groups’.
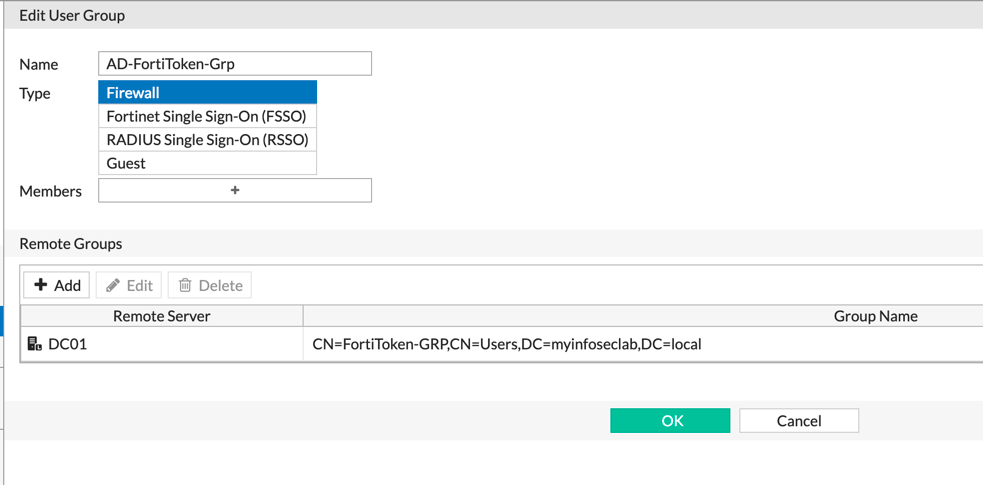
Give the group a name and choose ‘Remote Groups’. Choose the Domain Controler you created earlier, and select the ‘FortiToken-GRP’ group.
Now we are going to create a ‘Remote User’ (e.g. John Doe).
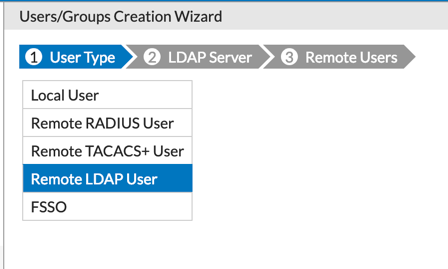
Go to ‘Users & Devices’ and select ‘User Definition’ and choose ‘Remote LDAP User’. Choose the DC you created and browse for the ‘John Doe’ user.
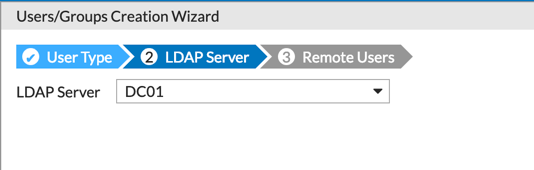
Once the user is created, you will select it and choose ‘Edit’.
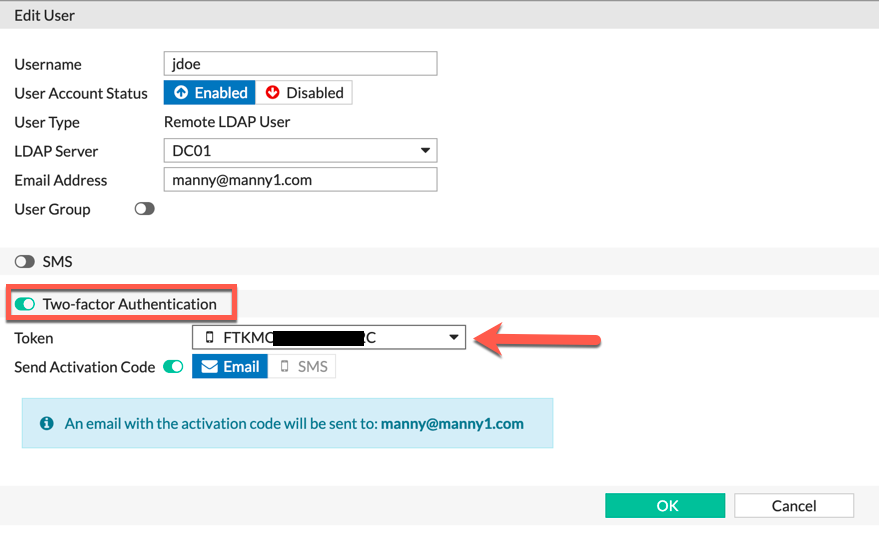
Once you edit the user, click the ‘Two-Factor Authentication’ button. From the drop-down list, choose an available FortiToken and save. You can re-send the activation from this window.
![]()
NOTE: You must have an email address in the appropriate field.
The user needs to go to their AppStore (Apple) or Market Place (Android) to download the FortiToken app.

IOS AppStore
Google Play Store
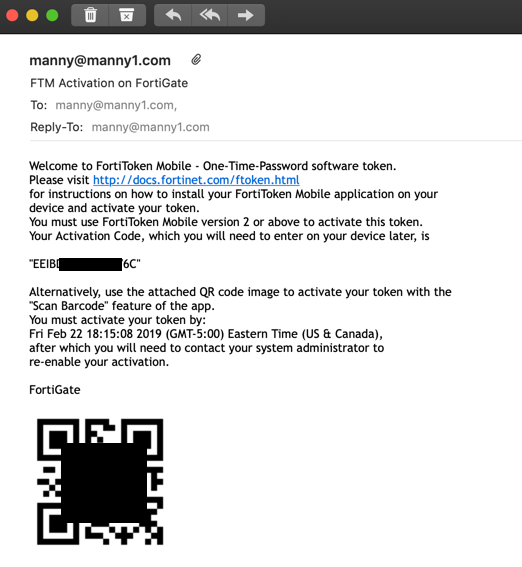
The user will recieve and email with the QR code. The one below has been modified to disable it in the graphic.
As in the other blog post, you will need to make sure the User Group is permitted to use the VPN’s particular portal.
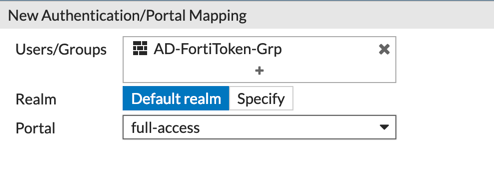
And finally, ensure the Policy is configured correctly
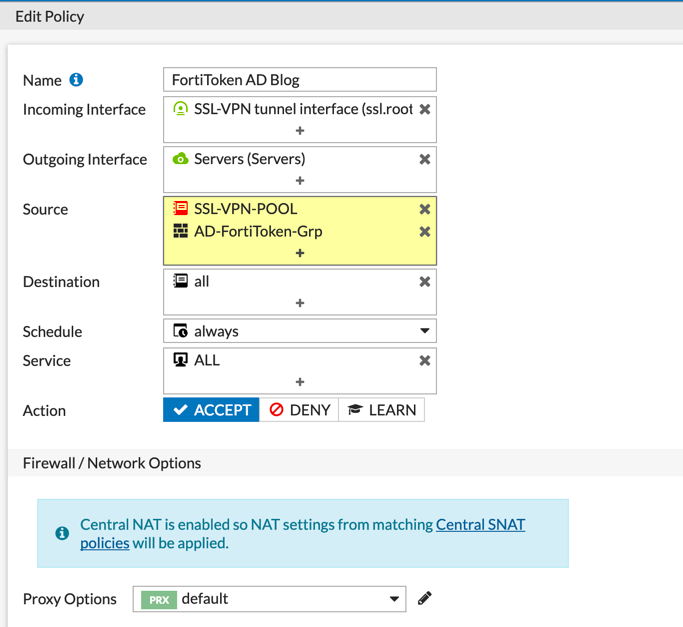
Note: Another Option would be to deploy a FortiAuthenticator. The FortiAuthenticator give you more flexability becuase it gives you the ability to use other authentication methods such as OAuth and SAML. Additionally it allows you to do ‘push notification’ where you will receive a a pop-up on you device.
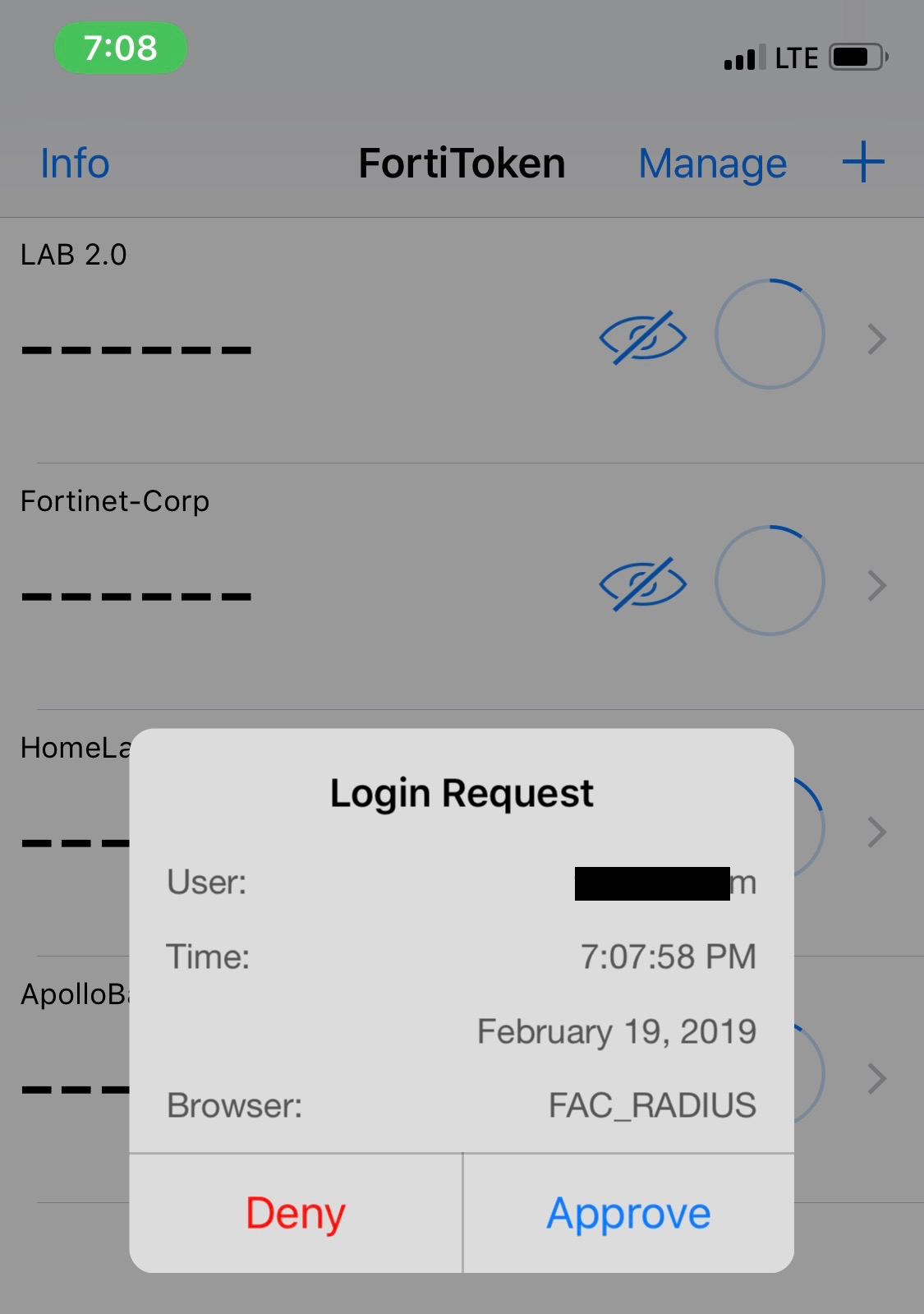
Hope this helps.
Recent posts
-

-

Had a customer with over 200 static routes on... Full Story
-

This is a work in progress, I will be... Full Story
