In FortiOS 7.4, Fortinet enhanced the ability to do... Full Story
By Manny Fernandez
September 24, 2019

Interacting with a decoy in FortiDeceptor
Yesterday, I wrote a post showing how to deploy a Decoy and the Lures . It did not show any of the discovery components of FortiDeceptor and the Incidents.
In my last post, I deployed a Linux decoy and created two lures for SSH and one lure for SAMBA. Here I will simply use the credentials I had created (manny and qwerty).
Previous Decoy and Lures
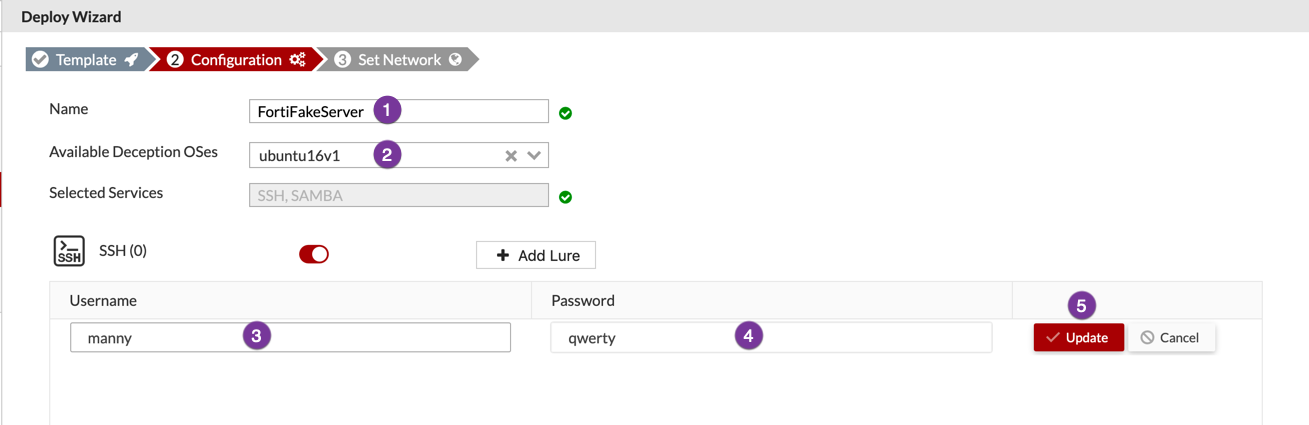
Above we can see a screenshot from the previous post. We can see that we created a username manny and the password for this ssh lure is qwerty
Connecting via SSH
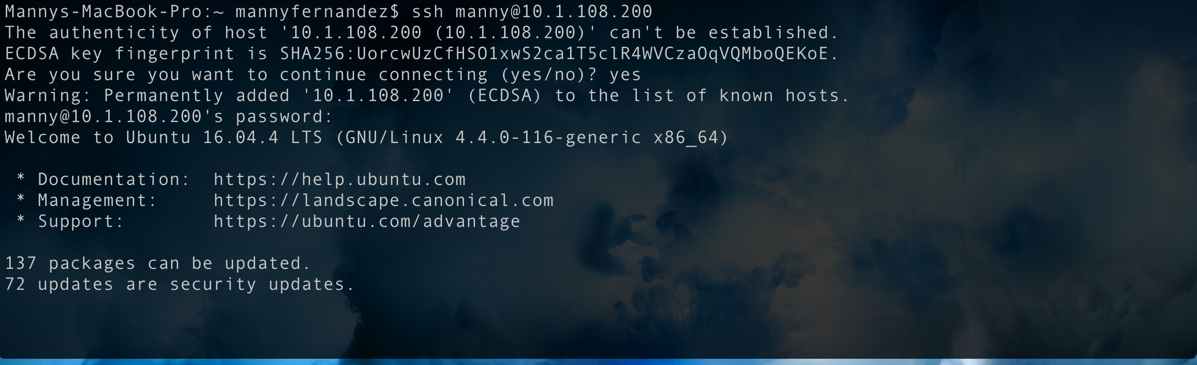
Above, you can see that I ssh'd to 10.1.108.200, the IP of the decoy. I am not going to do anything crazy, just browse the environment.
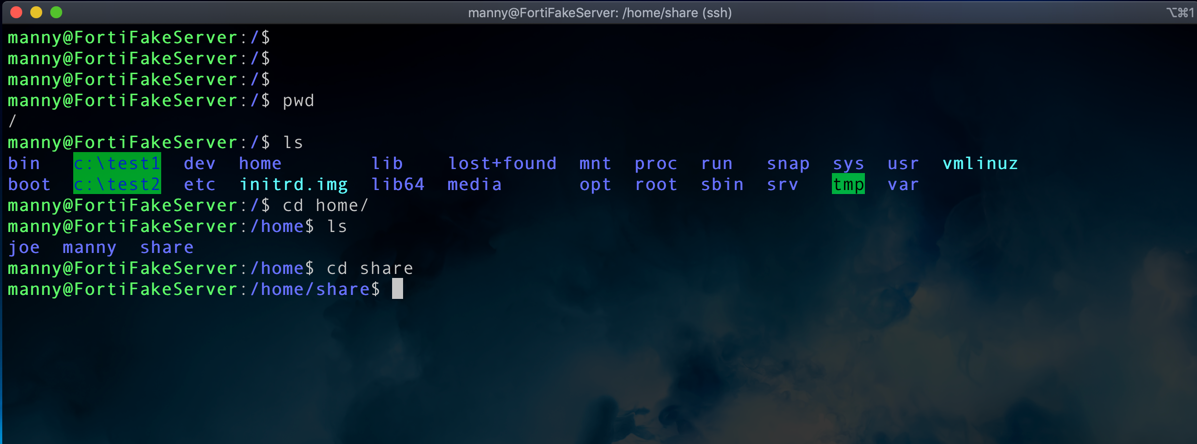
As I start to look at my newly found “booty” ( pirate version, not the modern version), I can see that there is a share directory/folder that looks promising.
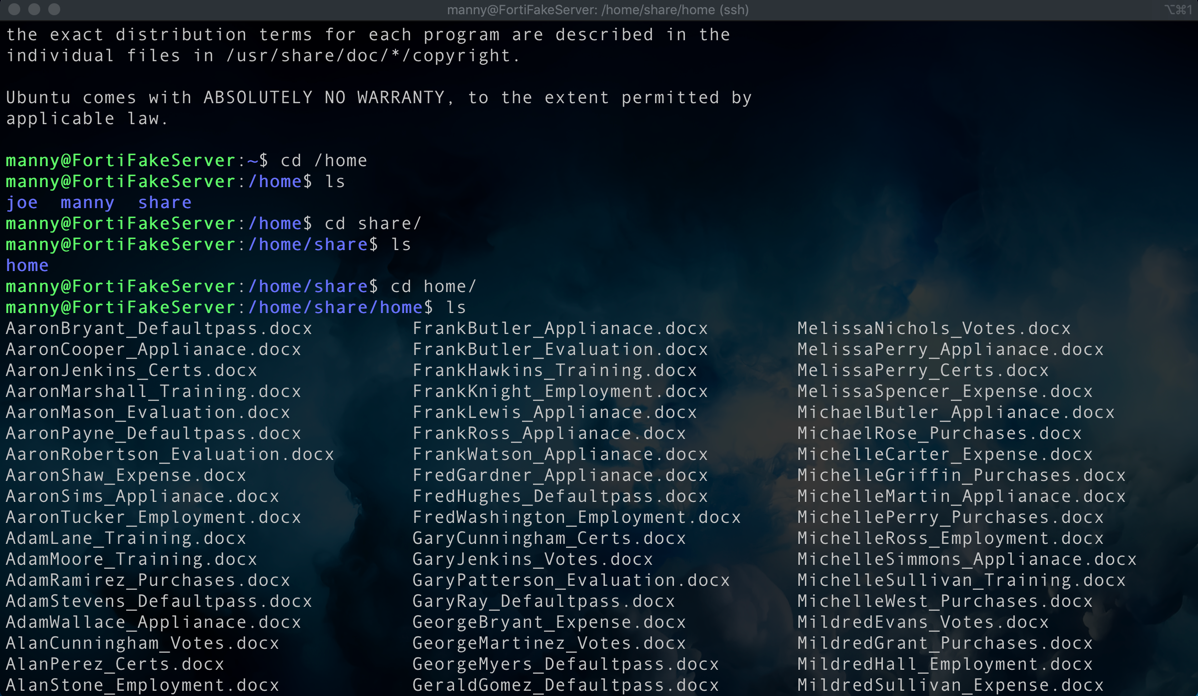
A simple ls shows fake files created under this folder.
What the FortiDeceptor is seeing
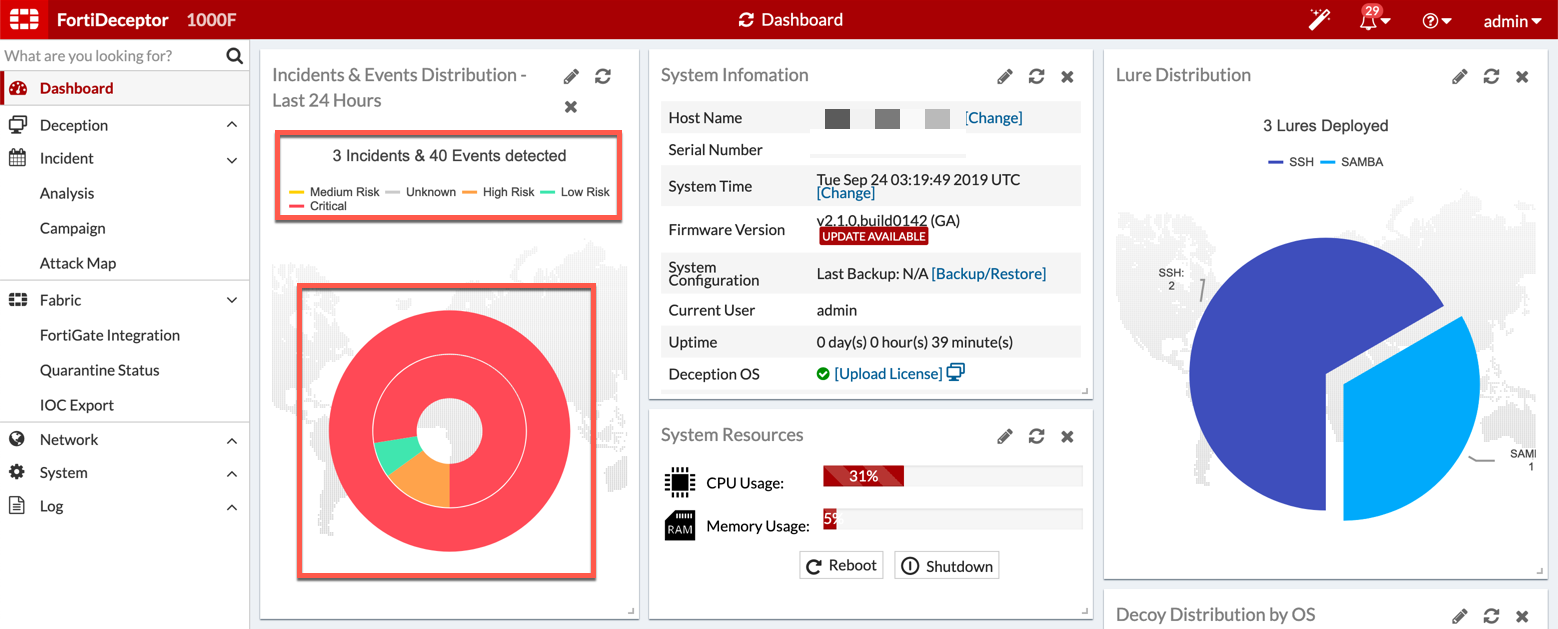
On the dashboard, we can see that in the last 24 hours, we saw three incidents and forty events.
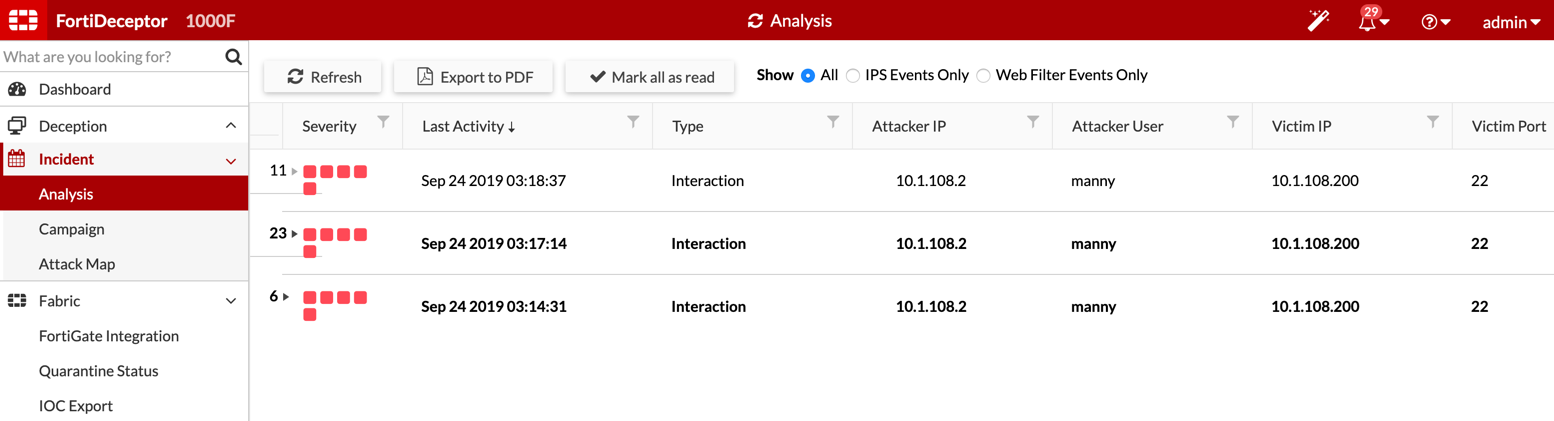
Under the Incident section, choose Analysis. Here you will see the three incidents.
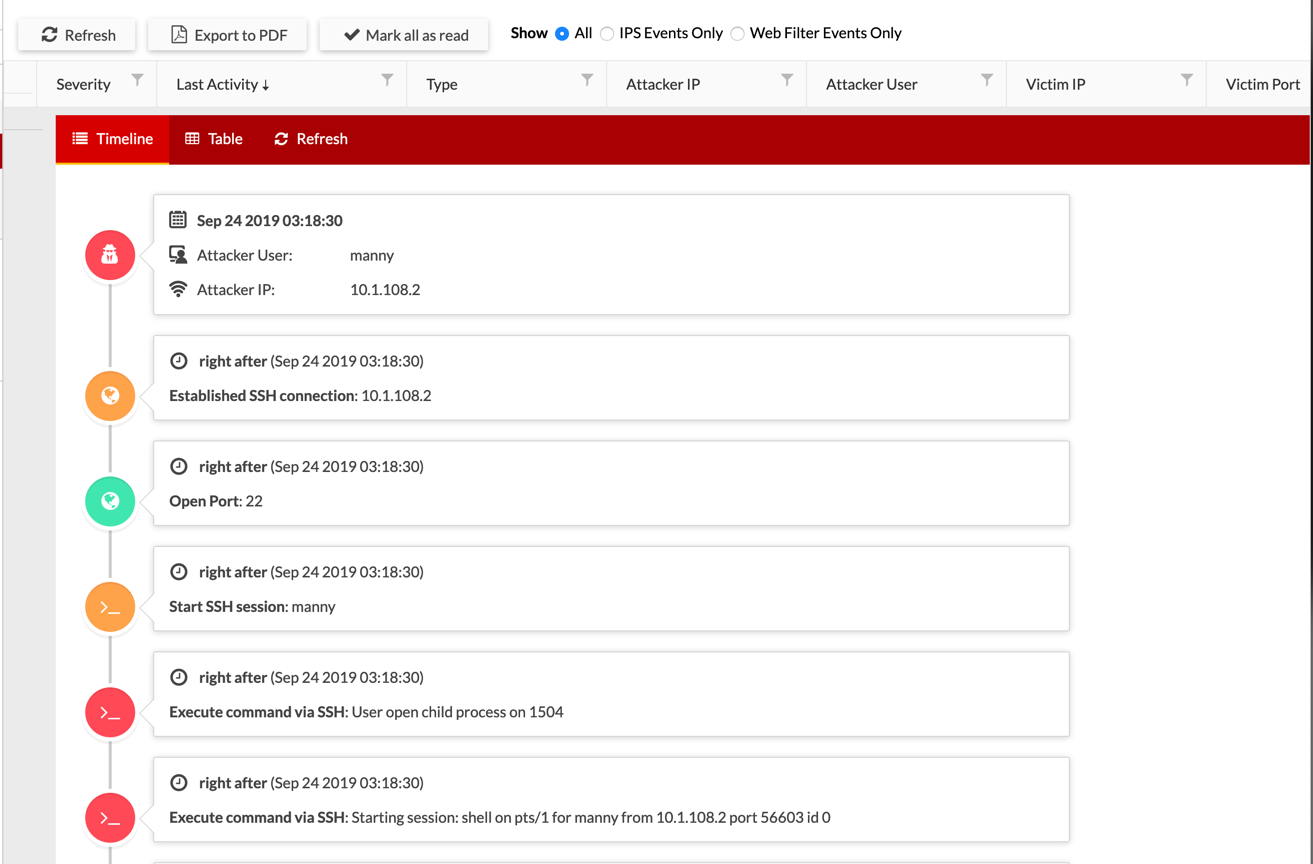
By choosing the small triangle on the side of the incident, it will expand that incident and reveal my (attacker in this case) activity including commands I typed.
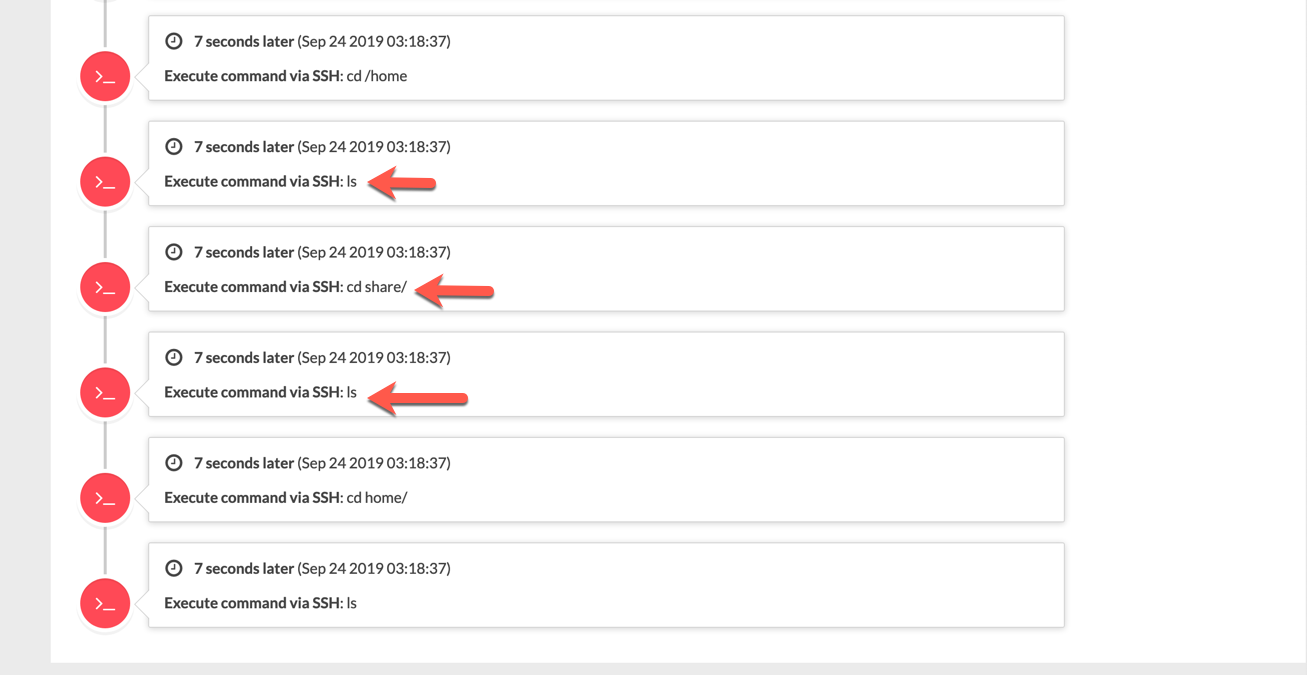
The second screen shot shows actual commands where the first one show the connectivity to the decoy itself.
Under the Incident then Attack Map you have a cute graphic that shows the attacker icon, attacking the decoy icon. (notice the gif, hard to see here).
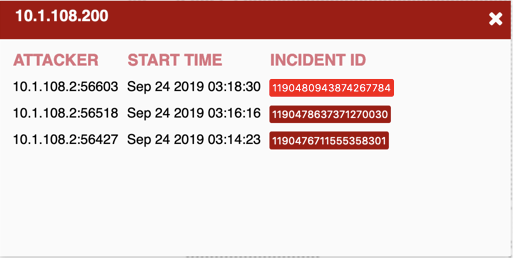
As in most of the Fortinet GUIs, there is a lot of shortcuts that make the interface very intuitive. By clicking on the Decoy in the Attack Map section, you will be able to see these incidents and by clicking on them, it will take you to the Analysis screen I showed above.
Exporting
You can export this incident to a PDF (see below).
Conclusion
The key thing to remember about FortiDeceptor is that there are no False Positives. Anyone interacting with this environment is in fact attacking it. There is the ability of leaving breadcrumbs on legitimate devices in your environment that would lead an attacker to the FortiDeceptor environment.
Recent posts
-

-

Apple shortcuts have been an amazing addition to IOS. ... Full Story
-

Years ago, when I started using FortiGates, I had... Full Story
