At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
February 4, 2018

Negate Source, Destination or Service
I started working on Firewalls back in the early 90’s. I started on Checkpoint Firewall-1 running on AIX. I soon moved over to Windows where we had to disable so many services, it would take longer to prepare for the install than the actual install of the firewall itself. There used to be a local.arp file you needed to edit and add the external interface where the proxy ARP needed to come from’s MAC address and the NAT (Public) IP. As of 2011, there was still a variance of this learking in the bowels of CP. You would “push” the policy and then need to run a batch file to load the local.arp file. At any rate, Checkpoint did/does have some nice features that not everyone had. I did not know this feature existed on the FortiOS. The feature is the ‘negate’ feature.
Use Case: You want to create a policy that allows a guest VLAN to access anywhere EXCEPT your internal network of 10.1.1.0/24. Normally on the Cisco ASA and most other firewalls, it would require two policies, rules or ACE depending on what platform you are running. You would first define the ‘deny’ statement with the destination (10.1.1.0) above the second rule which would permit IP any, any. It would be much more efficient to create one policy that says, “everything except for this network”. Enter ‘negate’.
Here is my test scenario to prove the feature works: VLAN created ‘FORIFON’. I wanted to permit traffic to anywhere except 4.2.2.2.
Step 1
I start off creating a policy that permits the traffic that I want to block but with an action of ‘ACCEPT’. Once that is done, we go up to the top (or SSH using SecureCRT, Putty or something similar) and choose the CLI icon.
![]()
Once you are at the comman line, give the follwing command to get into the configuration mode of the firewall policies.
config firewall policy
Now you can issue the show command and Identify the ID number; remember this is different than the sequence number.
In my example, my ID is 43 so I enter the following command:
edit 43
Once there, I can again isse the show command and it will show me the configuration options for that particular policy ID.
NOTE: If you want to see the possible options you CAN configure, issue the ‘get’ command.
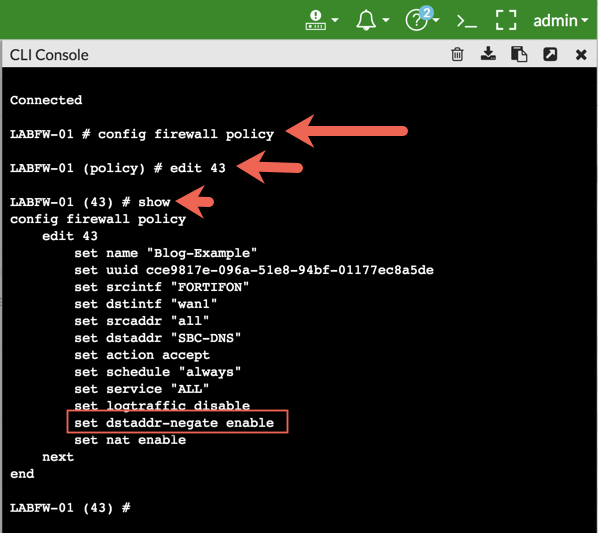
Here you can see that the source interface is going to be the ‘FORTIFON’ VLAN and my destination interface is wan1. We can also see that I am allowing ‘all’ sources (obviously coming from the VLAN FORTIFON) to a destination object named ‘SBC-DNS’ and my action is ‘accept’. For this presentation, the money-shot for this blog post is the:
set dstaddr-negate enable
Remeber, you can also use this same method for source and services.
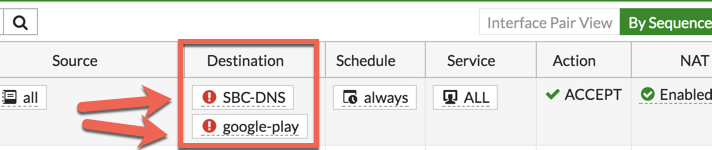
Once this feature is turned on, it will change the visual representation of the policy in the GUI.
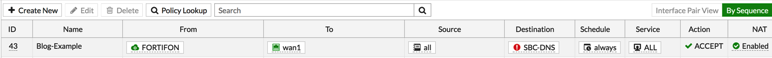
Notice the unusual red exclamation mark next to the object in the destination?
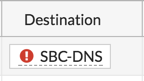
That is what tells you that this object is negated, thus all traffic to anywhere except the %said-object% will be permitted.
I connected another MacBook to the FORTIFON VLAN and obtain an IP address. I attempted to ping 8.8.8.8 and was successful, however when I attempted to ping 4.2.2.2, it fails.
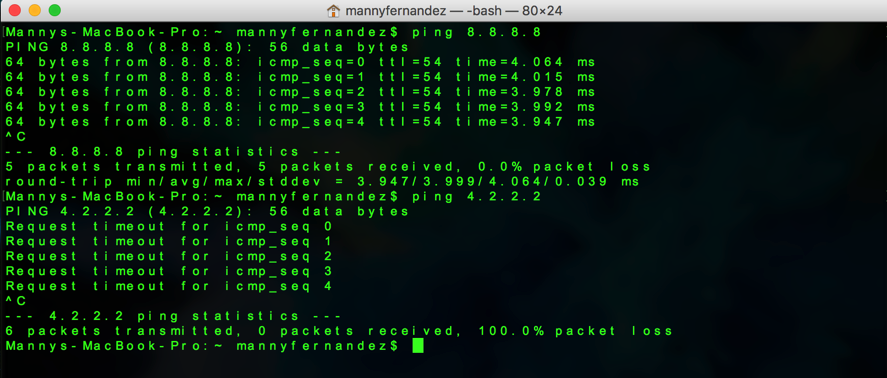
Here we can see the output of me pinging out to 8.8.8.8, however you can see that when I attempt the same thing to 4.2.2.2, it fails.
Additionally, as you add destinations to this negated policy, all of those destination will have an ‘OR’ affect on the policy. In my example, I added an additional destination and the policy will now show:
I hope this was helpful to you.
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
