In FortiOS 7.4, Fortinet enhanced the ability to do... Full Story
By Manny Fernandez
January 17, 2020
Policy Advanced Options in FortiOS 6.2.3
FortiOS 6.2.3 Introduced some interesting new features. One of those features is the Policy Advanced Options in which some interesting new options and one of my favorites that finally made it into the GUI.
1. – FortiOS 6.2.3
First of all, you will need to be running FortiOS 6.2.3.
2.- Enabling the Policy Advanced Options
You will need to go to system then Feature Visibility

Tick the button on the Policy Advanced Options

3. – TCP Sessions without SYN
Sometimes the firewall needs to handle long sessions, such as large data transfers or database backups, which can remain open at the endpoints but the session can be deleted from the firewall because of inactivity higher than 3600 sec (default inactivity timer). If a packet belonging to a deleted session reaches the firewall, it will be dropped. For this kind of scenario, disabling SYN checking in the FortiOS on a packet that belongs to an open session on the endpoints, could help avoiding such disruptions to network traffic flows, when the session becomes active again. (REF: Fortinet KB FD40929 ). This is also true for Asymmetric Routing.
config system settings set tcp-session-without-syn enable end
This is in addition to the Policy Advanced Options
The Results
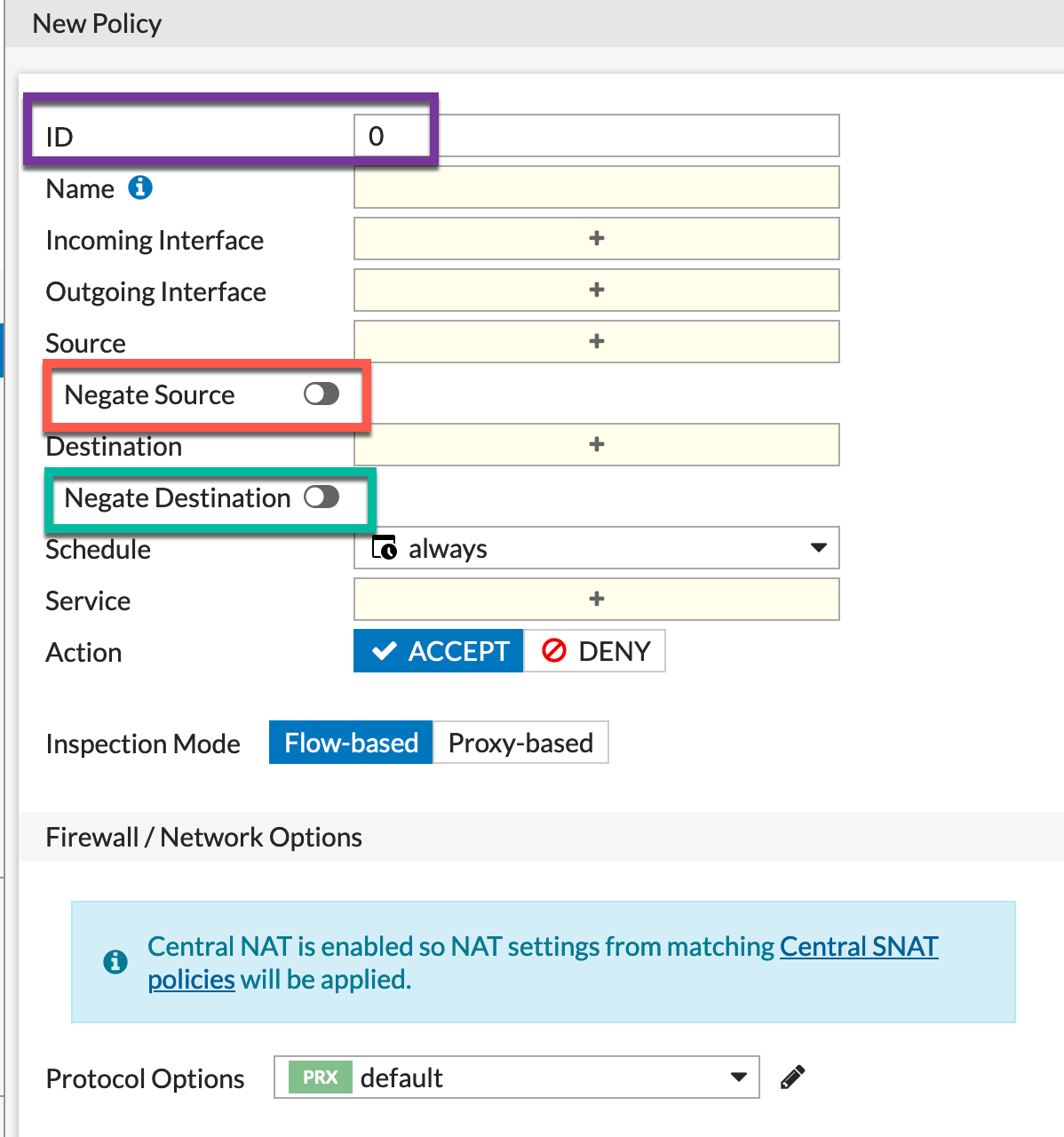
First thing you will see different is the ID. This feature allows you to assign the Policy ID which was not an option before. The default of 0 is representative of next available number. This is great. In the past, if you had a policy with a Policy ID of 3 and you deleted it. Next you created a new policy, it would be assigned and ID of 4.
The next two things you see is the Negate Source and Negate Destination. This is something I used back in my Checkpoint days. Although the feature has been in FortiOS for some time, it was NOT available in the GUI. Ironically, in the 6.2.0 Release Notes, there was a picture of it but it was not in the code. In development, sometimes features get moved and pushed down to a different release. I am happy though, that it was included here.
4.- What Negate Does
When you create a policy such as the one below, it essentially tells the firewall that anything EXCEPT address object DC-01 will match this policy. The use case for this would be that you want to permit all internal devices except for the DMZ network, you could create a policy and use Negate Destination . One thing missing though is the Negate Service which is still available in the CLI.
LAB-FW-01 (76) # set service-negate enable Enable negated service match. disable Disable negated service match.
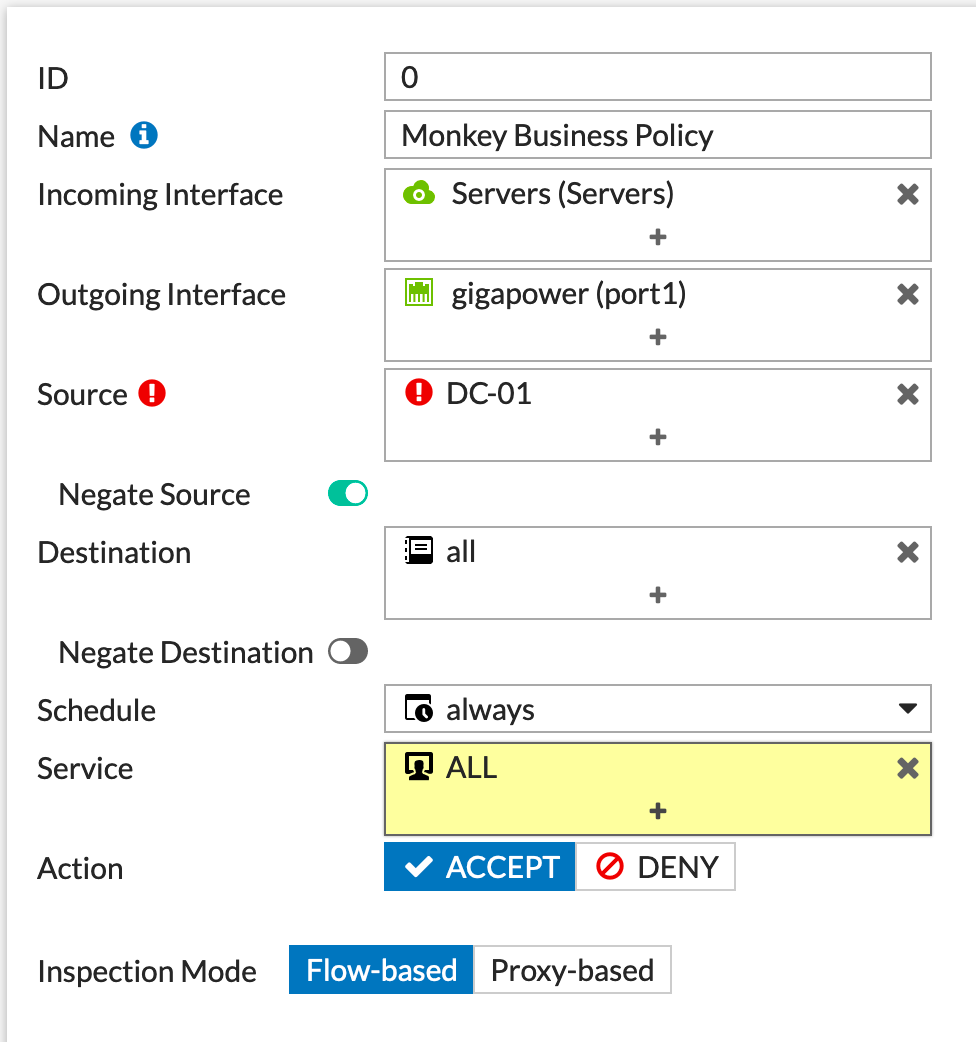
Hopefully service-negate will be in 6.2.4.
5. – Other Advanced Options
The other things that will get enabled in the GUI when you enable Policy Advanced Options is the WCCP , Exempt from Captive Portal and the TCP option we configured in section 3.
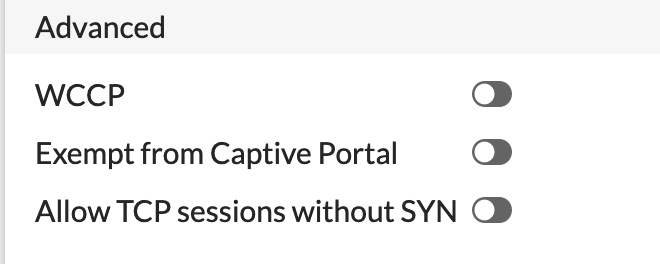
WCCP – Enable/disable forwarding traffic matching this policy to a configured WCCP server.
Exempt from Captive Portal – Enable to exempt some users from the captive portal
Allow TCP sessions without SYN – See above
Hope this helps.
Recent posts
-

-

Apple shortcuts have been an amazing addition to IOS. ... Full Story
-

Years ago, when I started using FortiGates, I had... Full Story
