At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
November 6, 2019

Running a FortiTest with FortiTester
Earlier, I wrote an article on upgrading the FortiTester. At the time, I did not have any SFPs for 10GB ports on the FortiTester. For the test I need to run, I need copper connections. The customer only has 200Mbps at each location, so the 1GB Copper ports would do the job. I reached out to a friend of mine, Adonis Sardinas and he was able to lend me (2) 1Gb copper SFPs. So here we go.
My Scenario
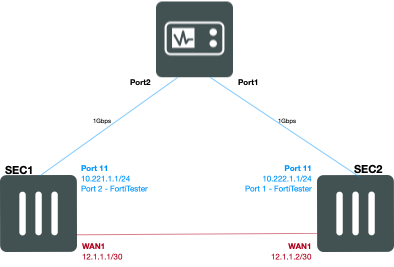
As you can see in Figure 1, My Network has a VPN between WAN1 of SEC1 and WAN1 of SEC2. These are FortiGate 140Es. I have local subnets attached to port11 of both FortiGates. The use case is to see how much data we can get across the VPN before the FortiGates choke.
SEC1 Interface 11 - 10.221.1.1/24 (Connected to FortiTester Port2) WAN1 - 12.1.1.1/30 SEC2 Interface 11 - 10.222.1.1/24 (Connected to FortiTester Port1) WAN1 - 12.1.1.2/30
VPN Configuration
In this example, I am creating a standard IPSec (IKEv1) VPN between the two SEC firewalls. For Phase II selectors I used quad 0's or 0.0.0.0/0.
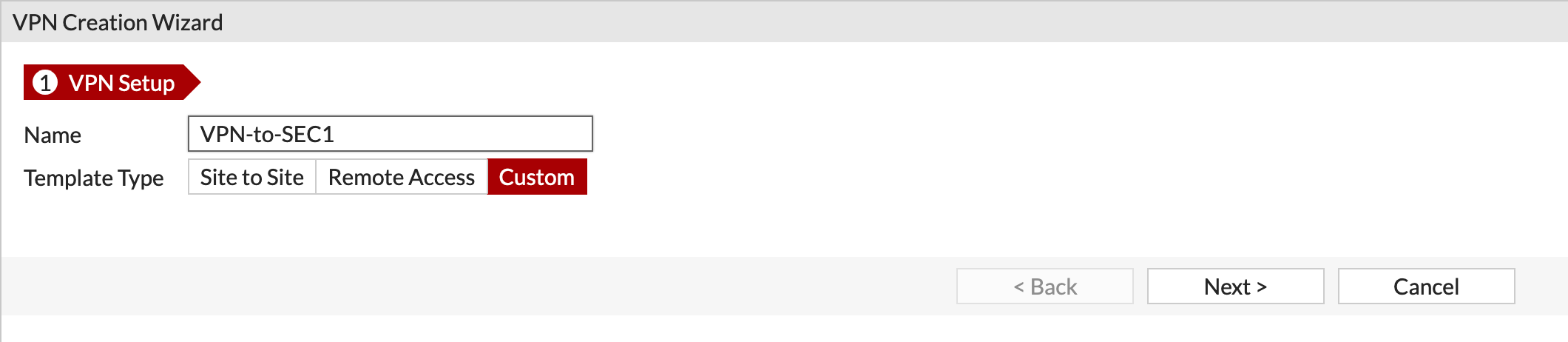
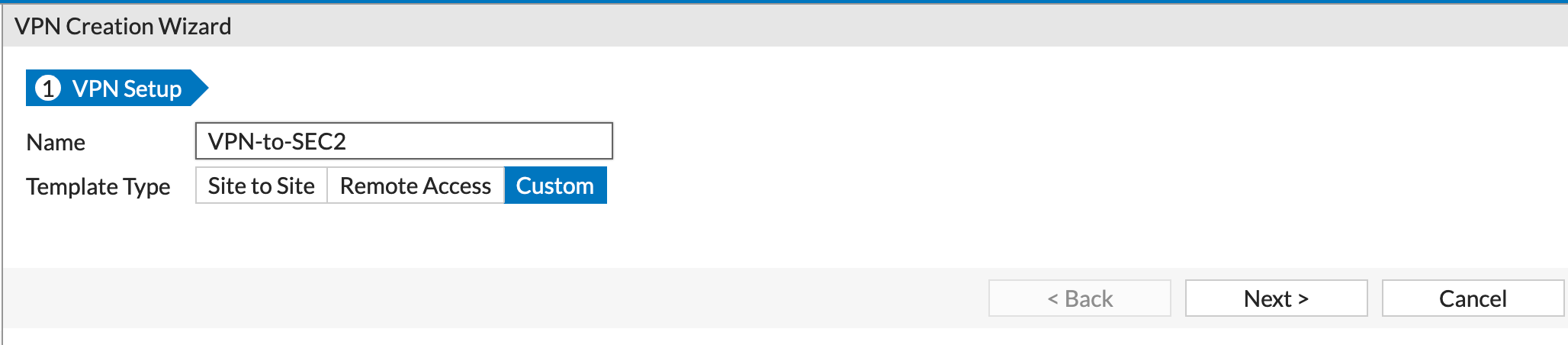
We started off by creating a VPN using the Wizard. As you can see, I like to use the Custom type as it allows me to choose my own options.
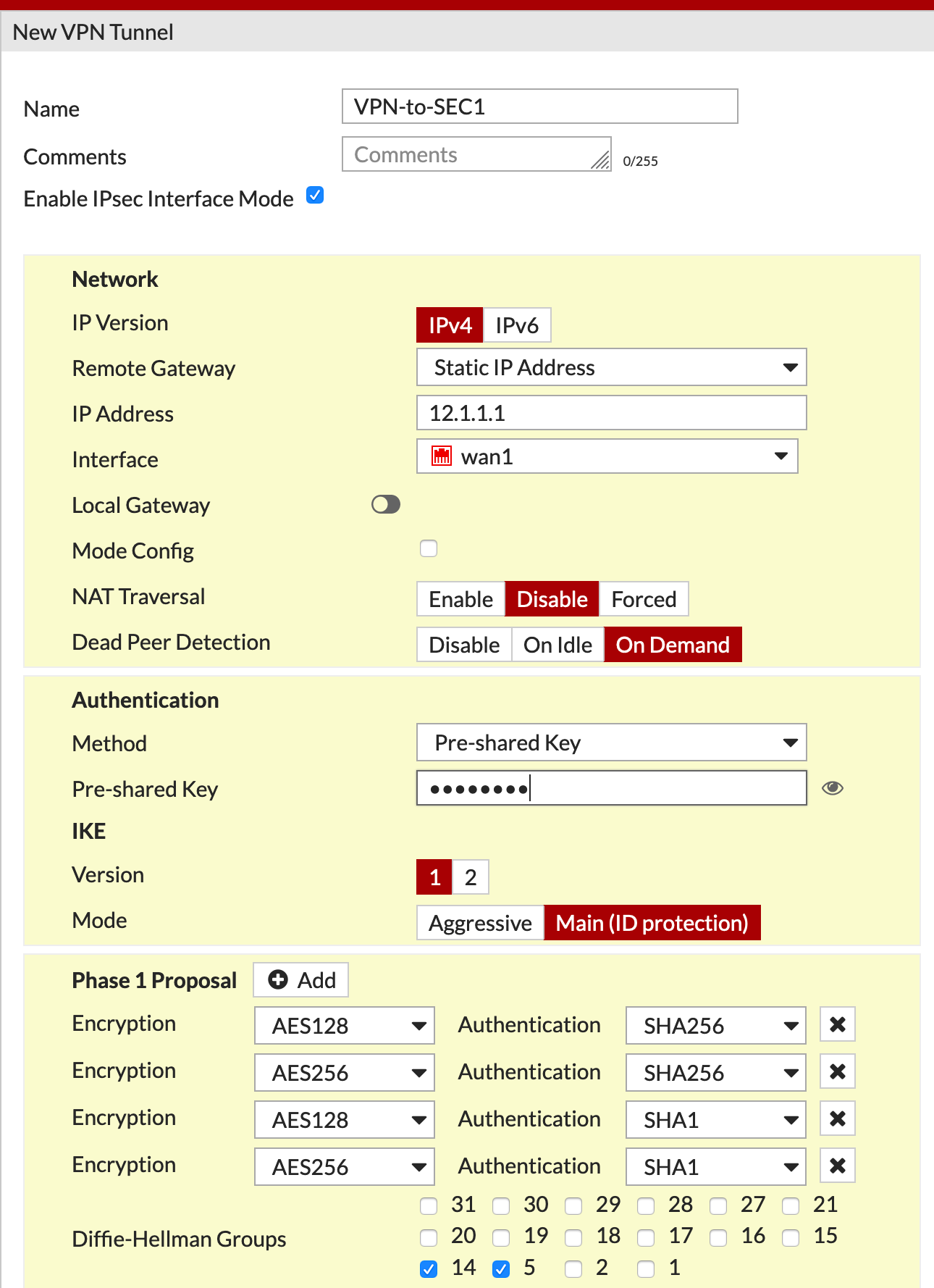
I named the VPN something descriptive VPN-to-SEC1 which is easy to identify. As you can see, I added the remote peer IP 12.1.1.1 in my case and the Interface I am going to use WAN1 in my case. (Yes the interface was down at the time of the screenshot).
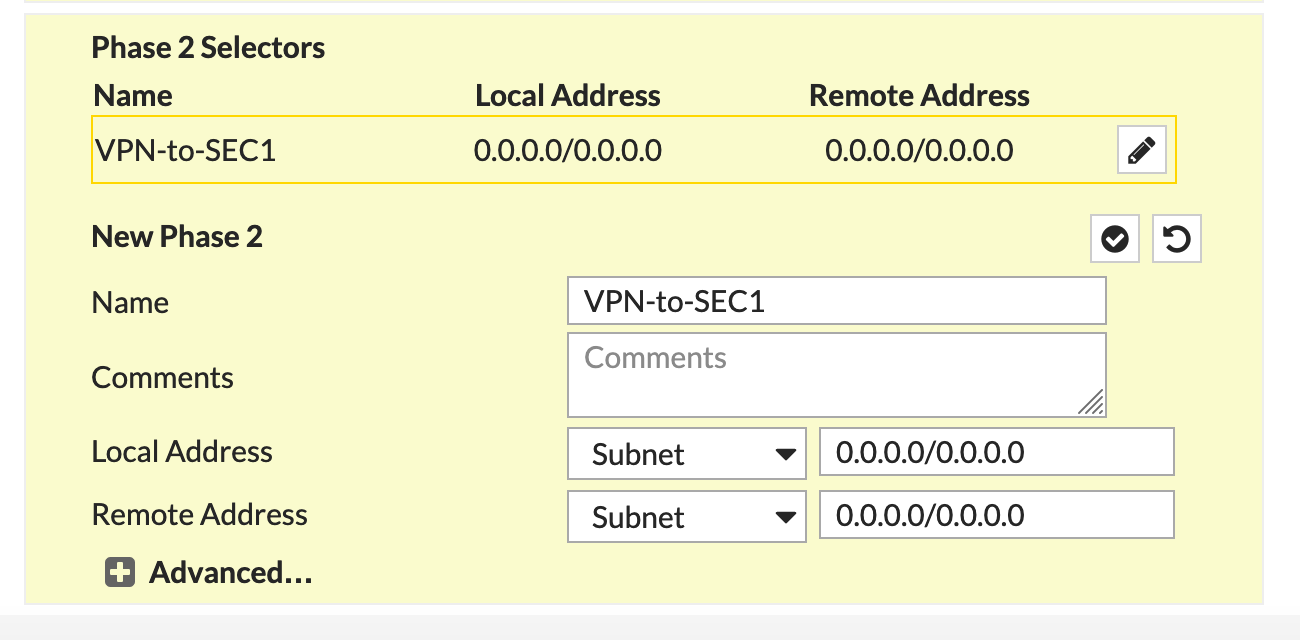
As I mentioned before, the Phase II was all 0.
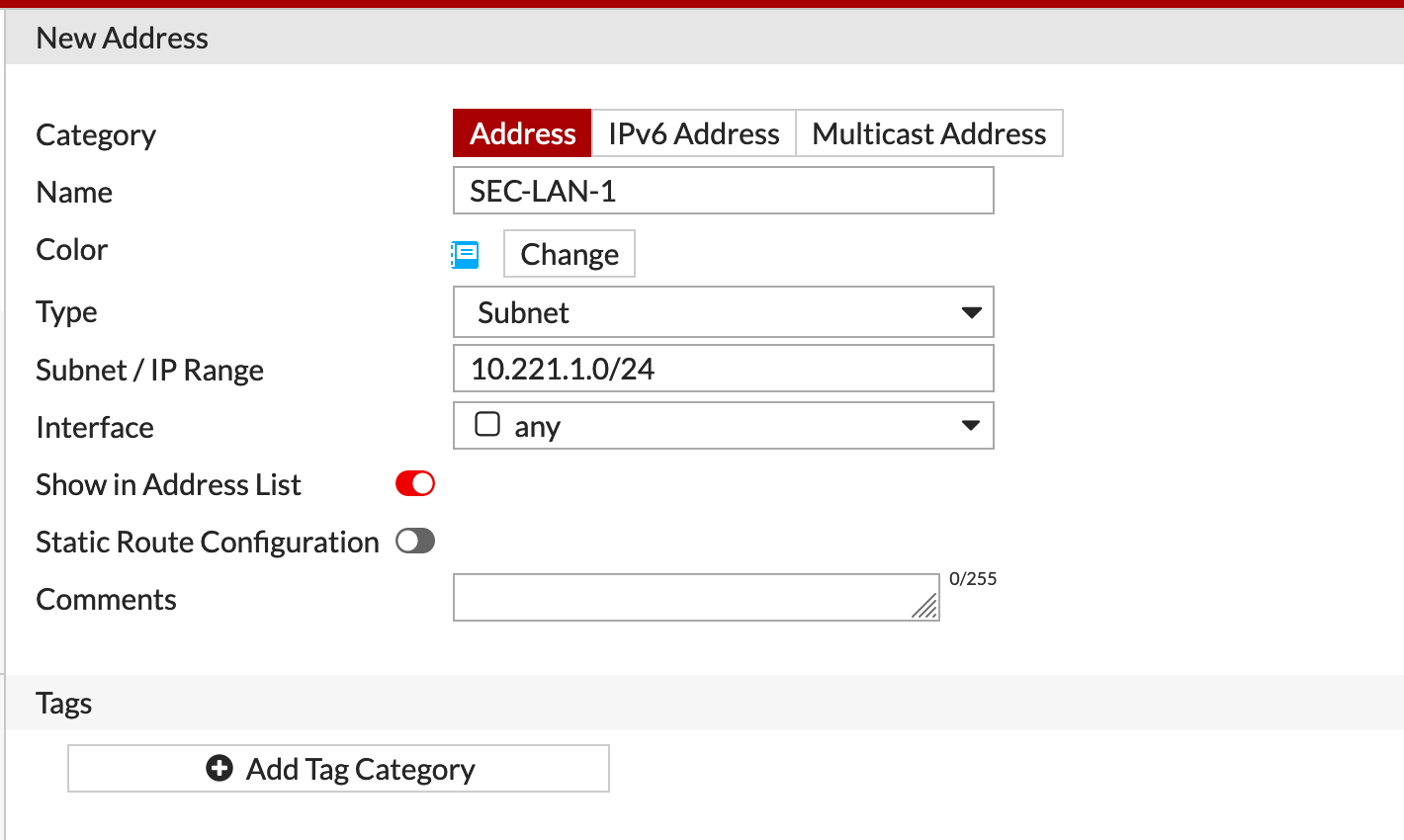
I created a Firewall Address object for SEC-LAN-1 and SEC-LAN-2 which was repeated on both firewalls since I will use both the objects in my IPv4 Policies.
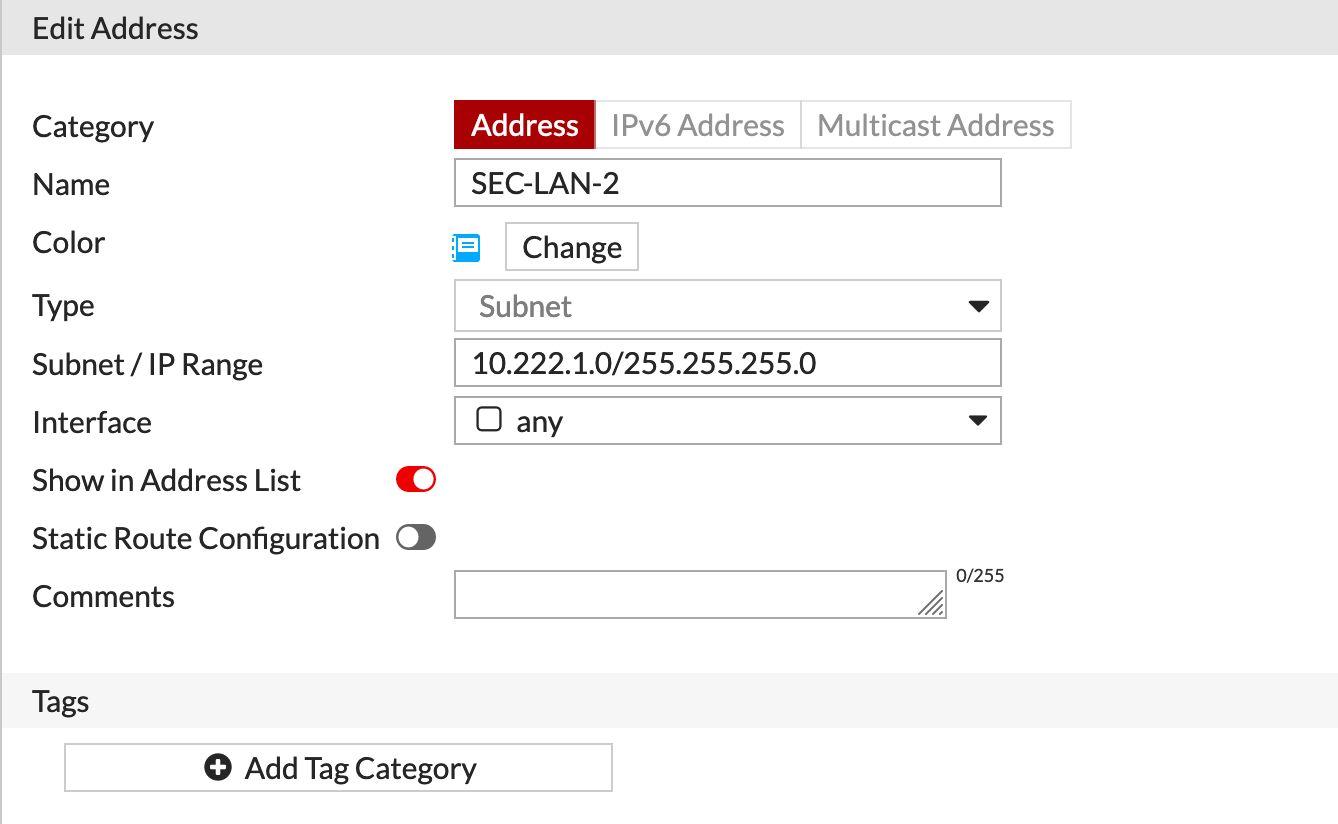
Again, this is the Local side for this particular firewall.
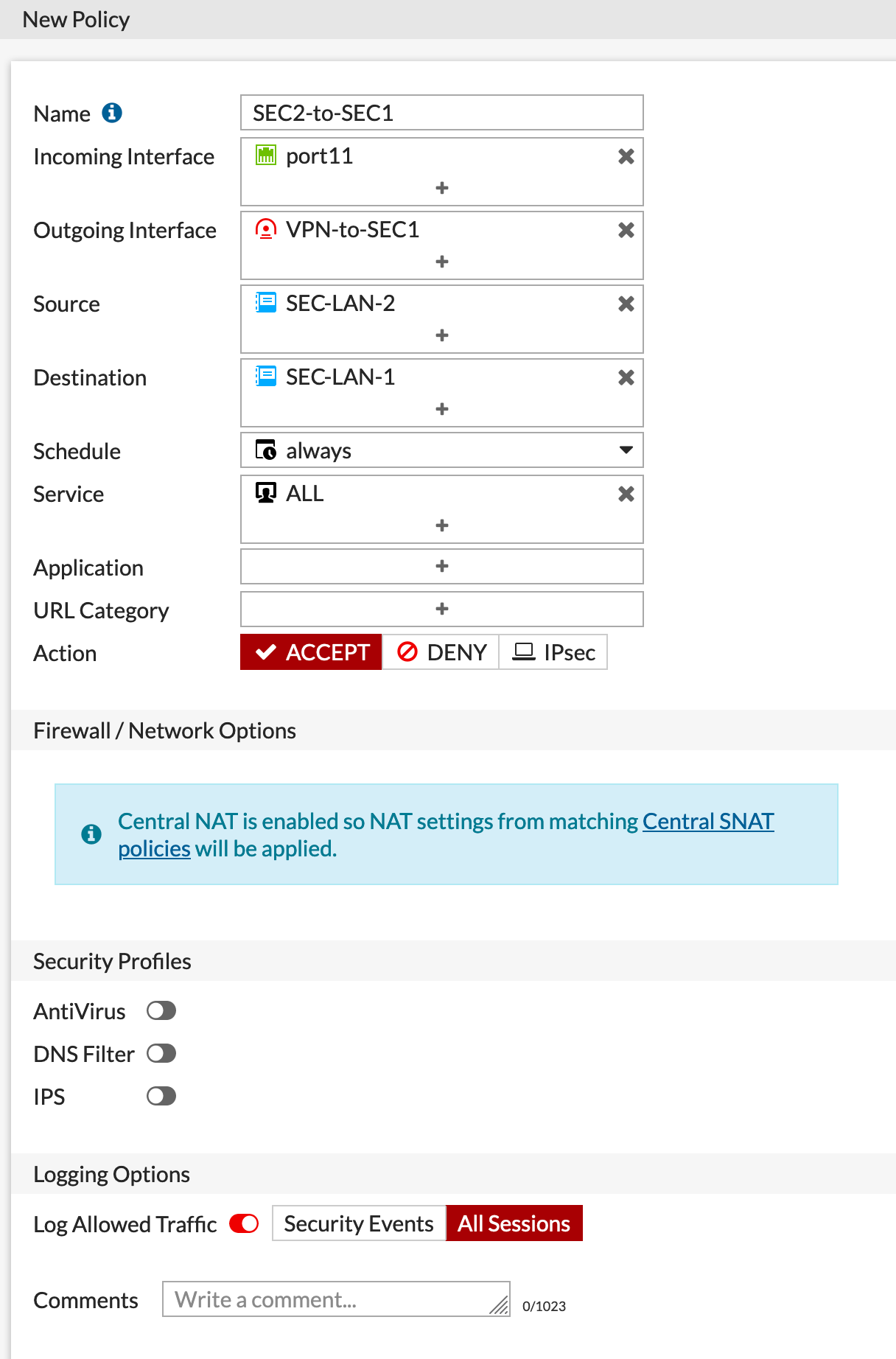
I created an IPv4 Policy sourcing it from interface port11 and destination is the VPN and then we permitted all traffic.
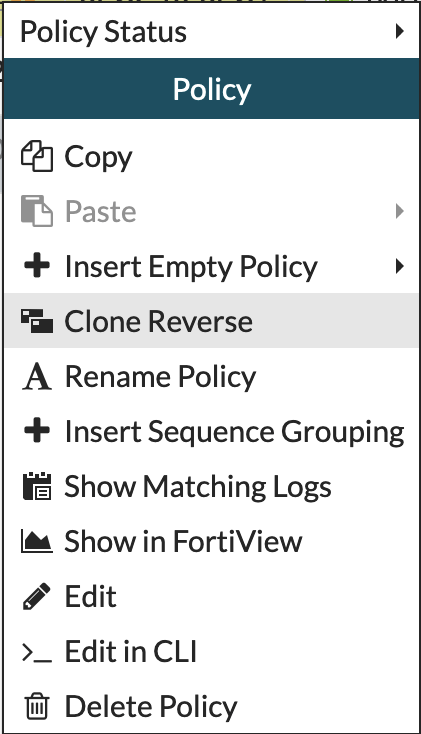
After I created the first IPv4 policy, I right-clicked the policy and chose Clone Reverse which does exactly that.
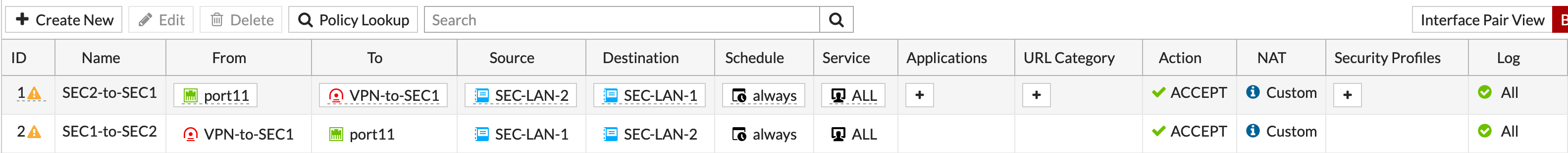
Now you can see that I have bi-directional policies allowing traffic to and from the two sites.
No for the revers. In this configuration, we are doing everything in revers since it was the remote site in the first example, now that site is the local site.
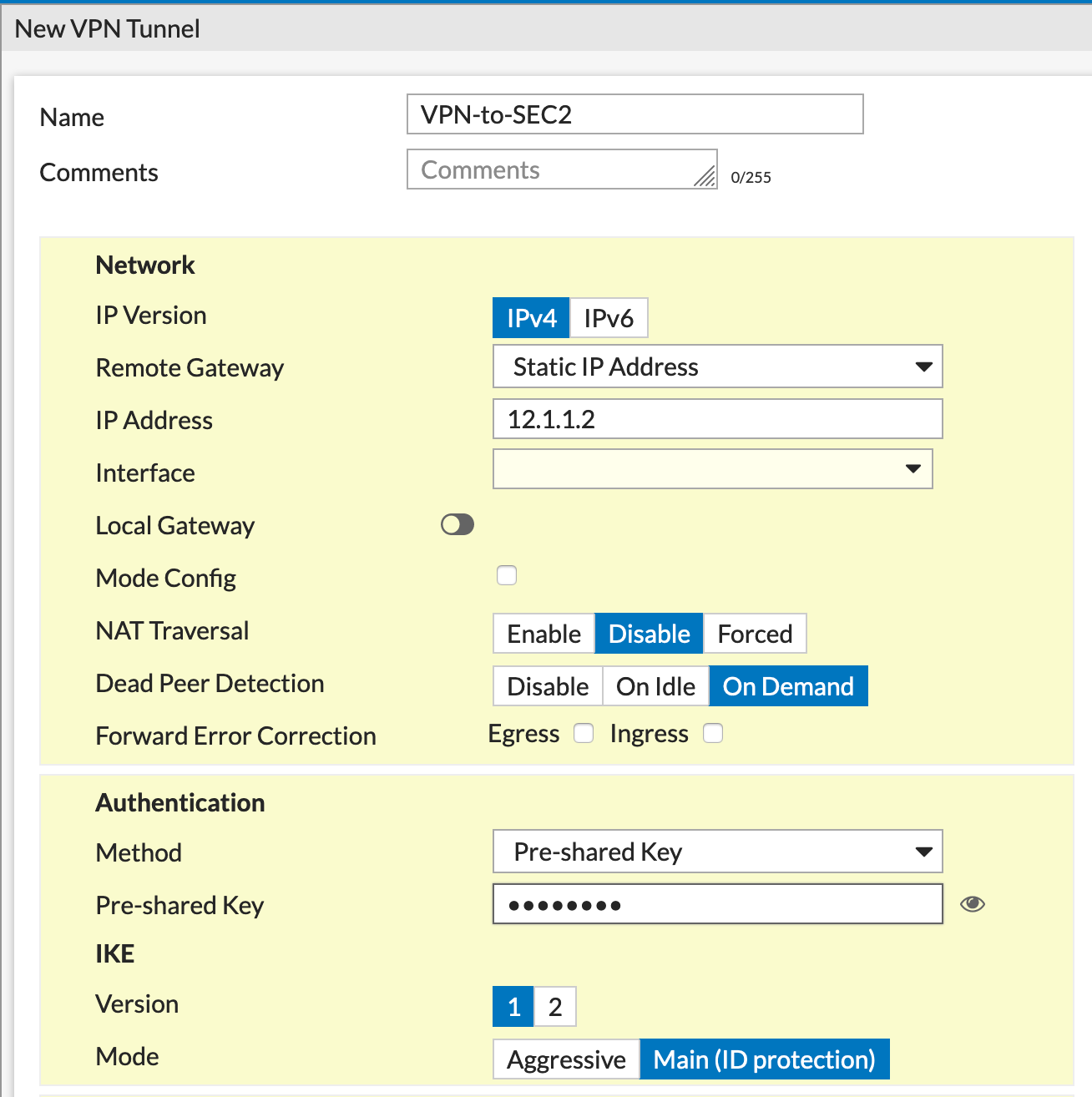
Here we see we are pointing to 12.1.1.2 as the remote peer.
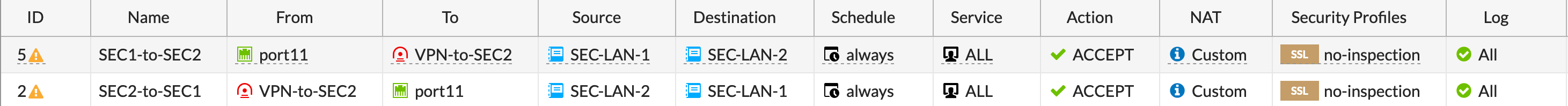
We can see the same bi-directional policies as in the first firewall.
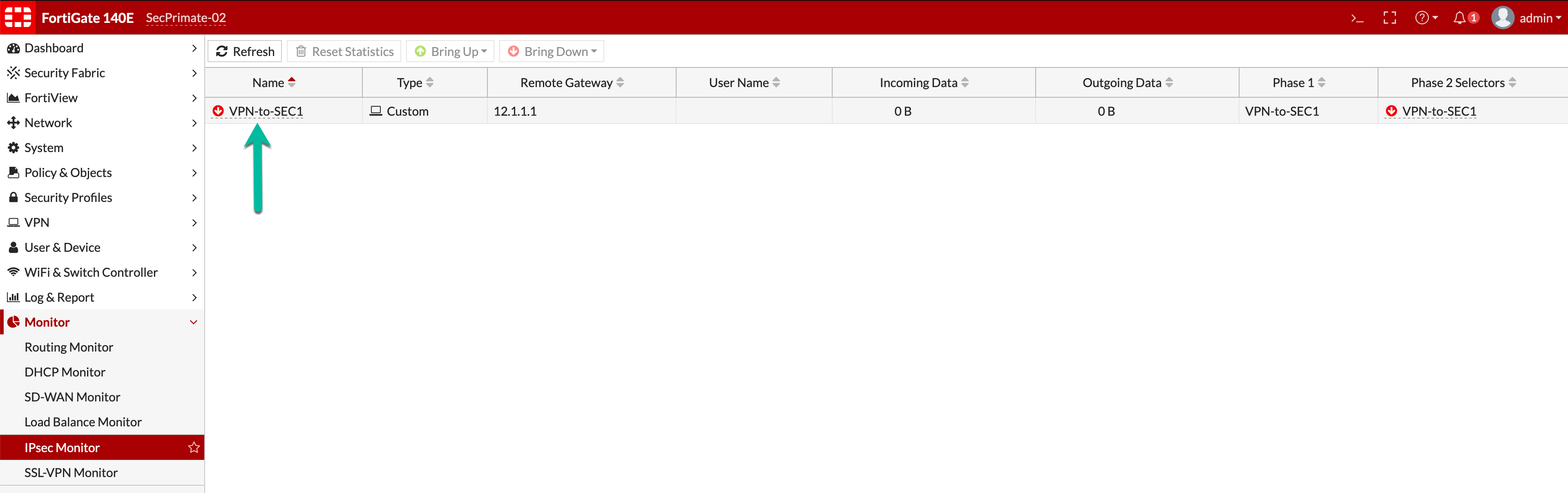
Time to bring the tunnel up. We can see the green arrow pointing to a Red VPN indicator showing the VPN is down. We clicked the Bring Up button on the top and then tunnel came up.
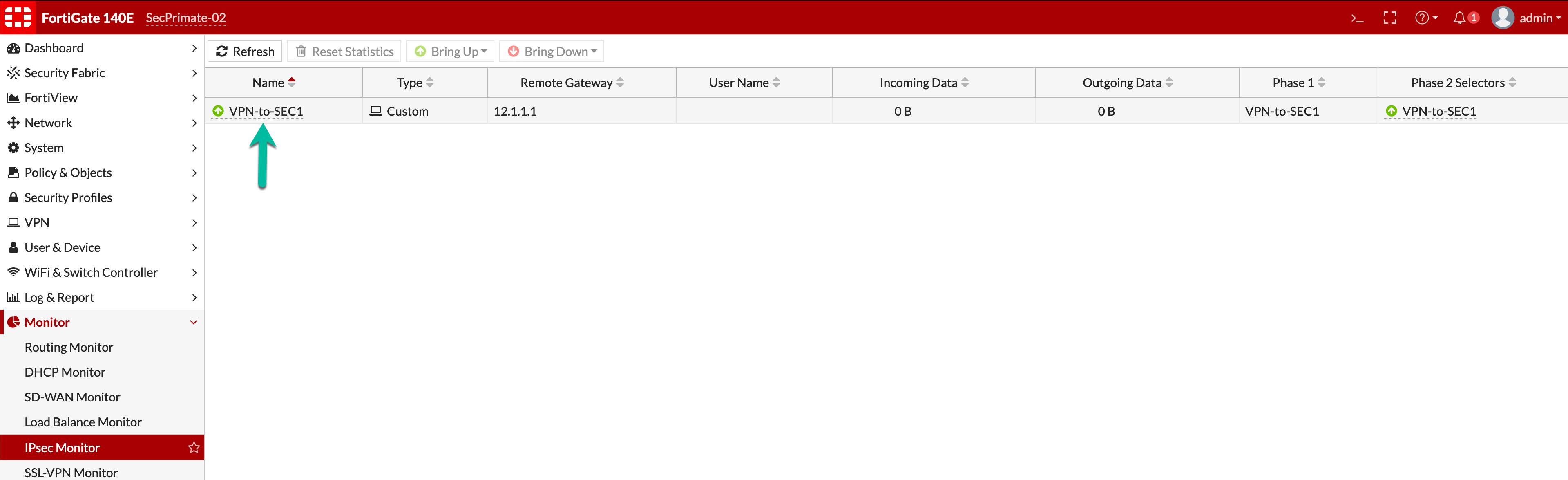
Now we see the Green indicator showing the tunnel is up.
NOTE: Don’t Forget your routes.
FortiTester Configuration
Now that the tunnel is up, we can configure the FortiTester for its test.
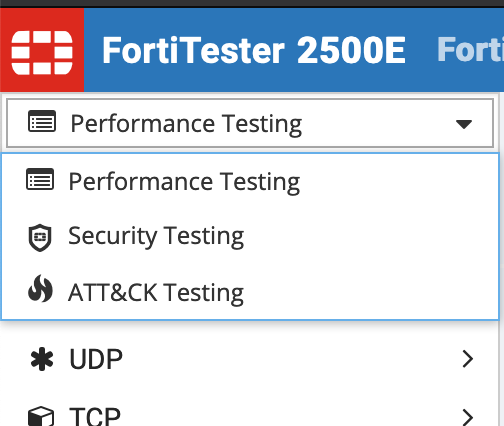
The FortiTester has three different types of tests it can run.
Performance Testing – This is self-explanatory. We will push packets through the connections to identify the maximum throughput a device can handle.
Security Testing – DDoS, Attack-Reply and other IPS type tests.
ATT&CK Testing – Simulate the post compromise behavior of a cyber adversary on an enterprise network.
This article will focus on Performance
Creating a Case
The first step is building a Case in FortiTester. This defines the criteria for the test.
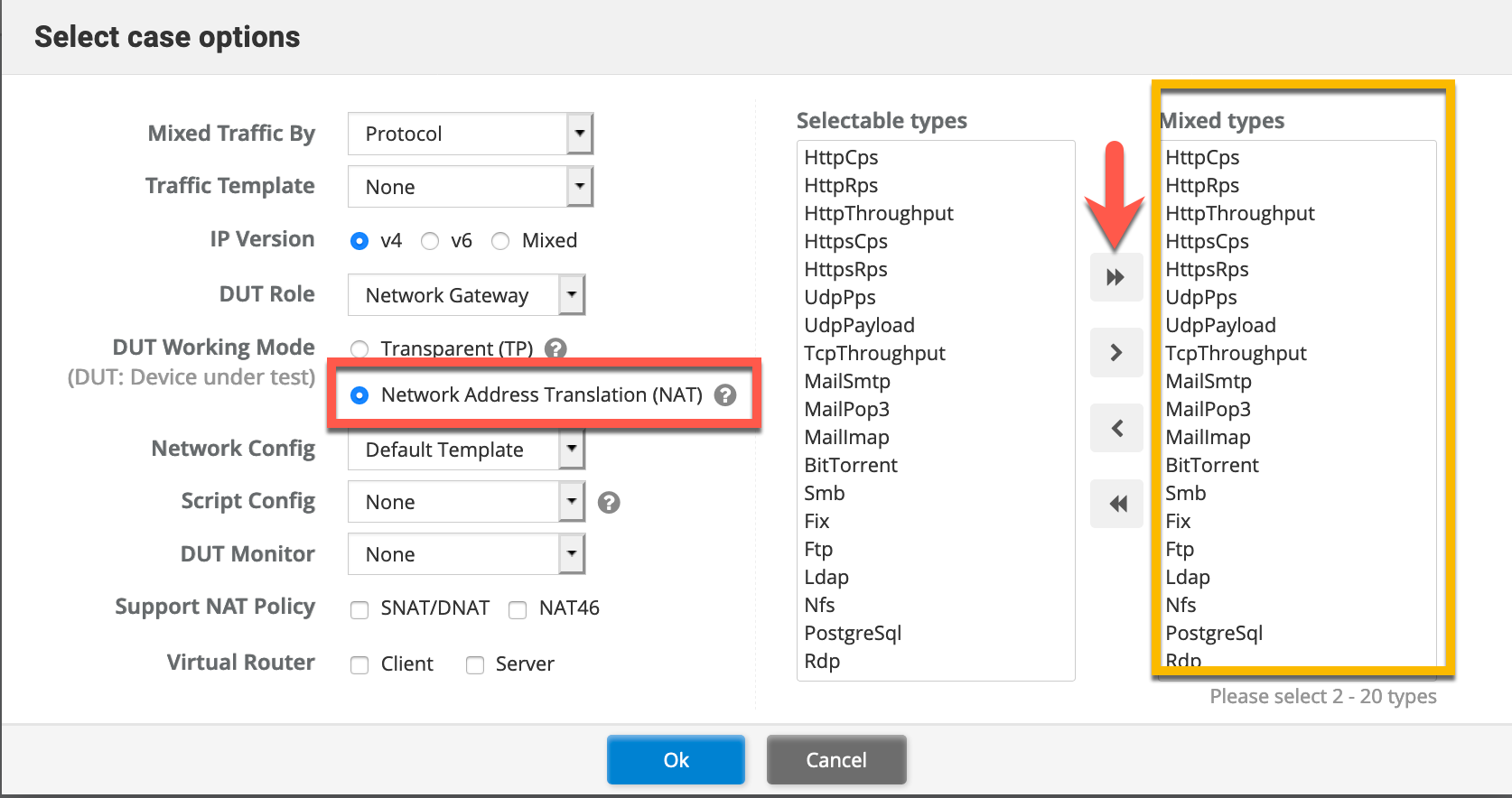
Here we define the DUT Working mode. In my case since I have two separate networks, I am using NAT mode. Additionally, I CAN choose what type of traffic I want to add to this case. In my case, I just added everything.
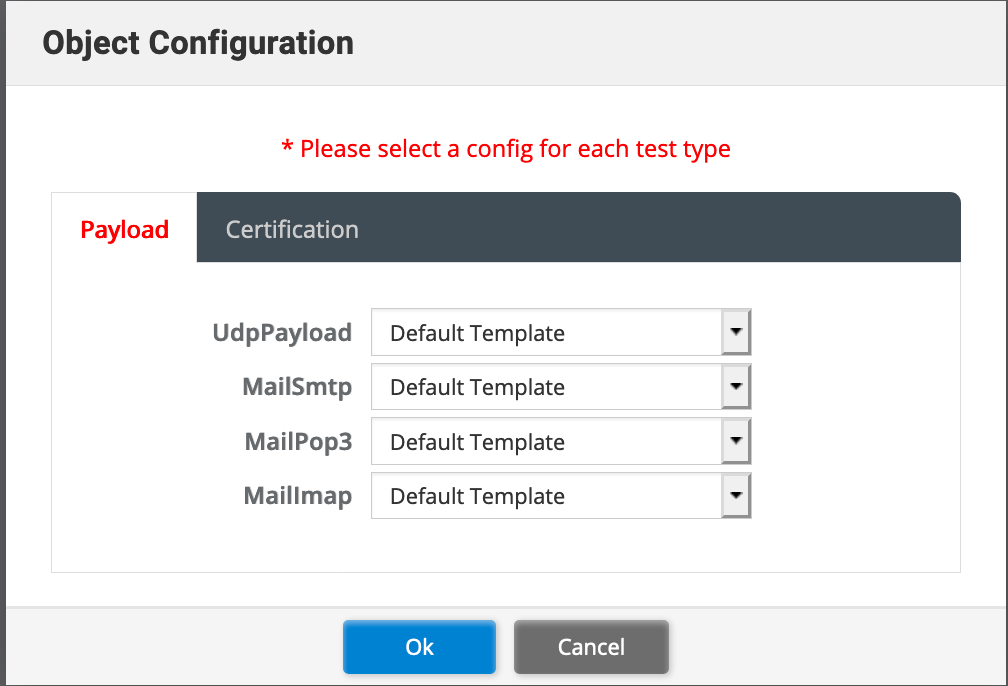
In this phase, you CAN load payloads via PCAPS and Certificates to use during the test. In my case I kept the defaults.
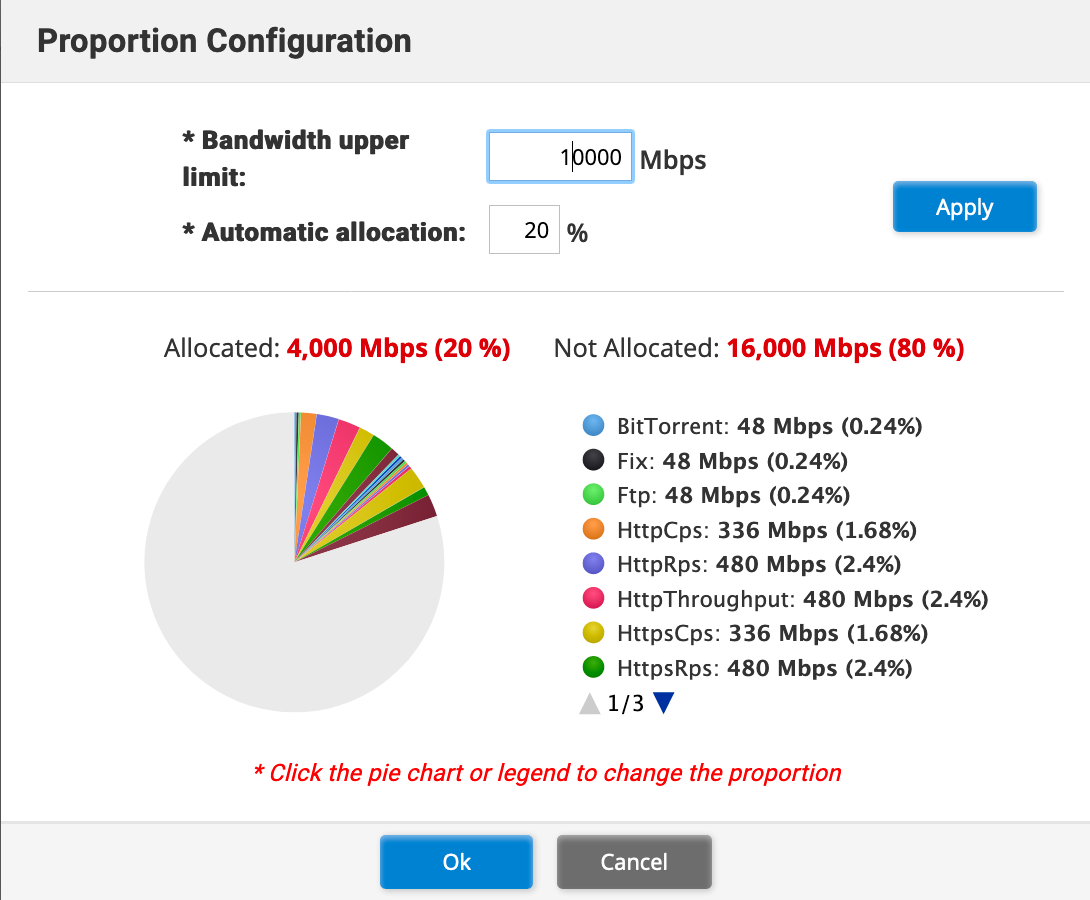
This shows you the % of traffic and the breakdown.
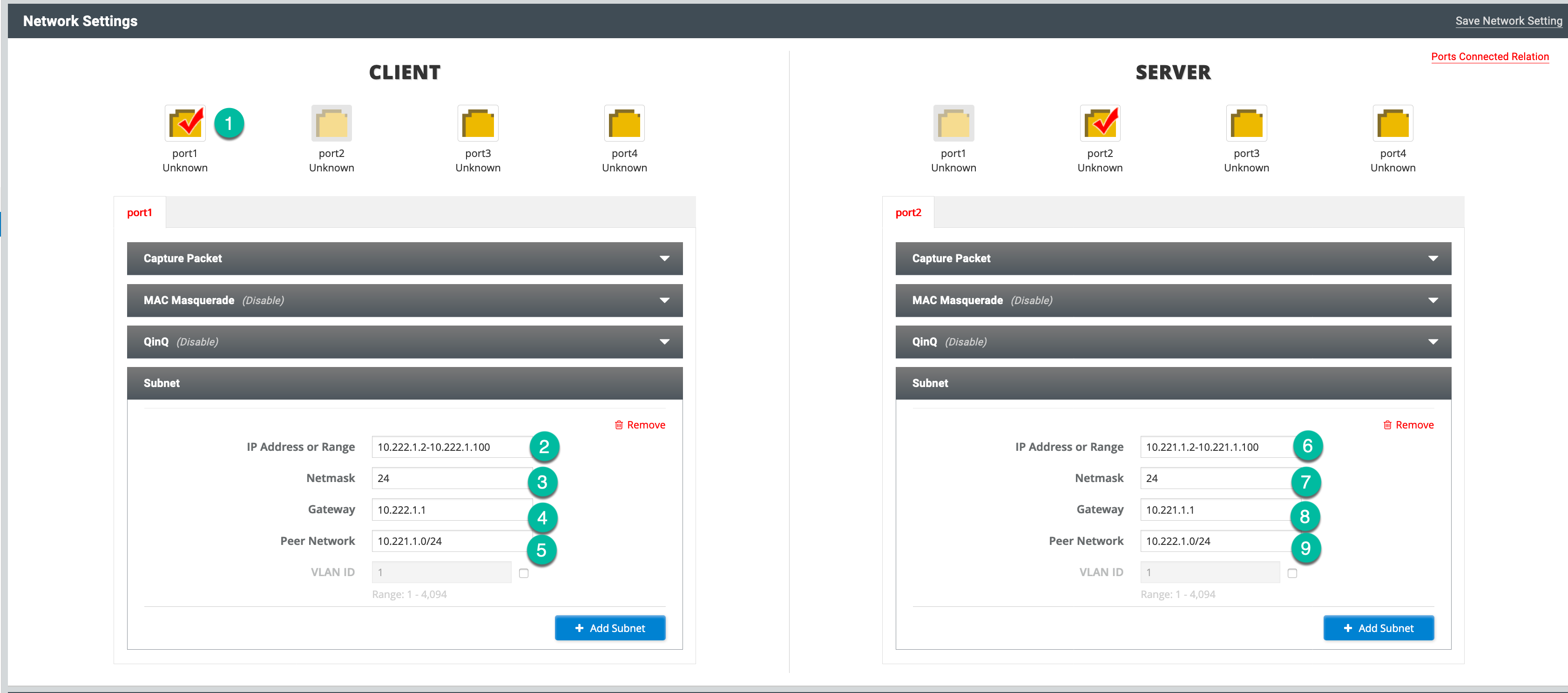
I will go through the options:
- You will need to choose the interface that is connected to the particular host. In my case Port1 of the FortiTester was connected to SEC2 firewall (I know my OCD is killing me right now).
- This defines a range of addresses on the Fortigate that is attached to port1 of the FortiTester.
- The CIDR notation for the subnet.
- The default gateway for the FortiTester to send traffic.
- This is the remote subnet on the other FortiGate
- The IP Range (similar to item 2 but in reverse).
- CIDR
- Gateway for the other side
- And Finally the remote network of the device connected to Port1 of the FortiTester.
Don’t forget to choose the Interface for the remote side, in my case port2
Running the Test
Once you have finished making the configurations from the previous steps, you can hit Start
Results
The FortiTester will export a PDF report showing the exact types of traffic and the amount. However for sake of brevity (its over 2K pages), I did not include it. However I will show you screenshots of the traffic I was pushing across the VPN circuit.
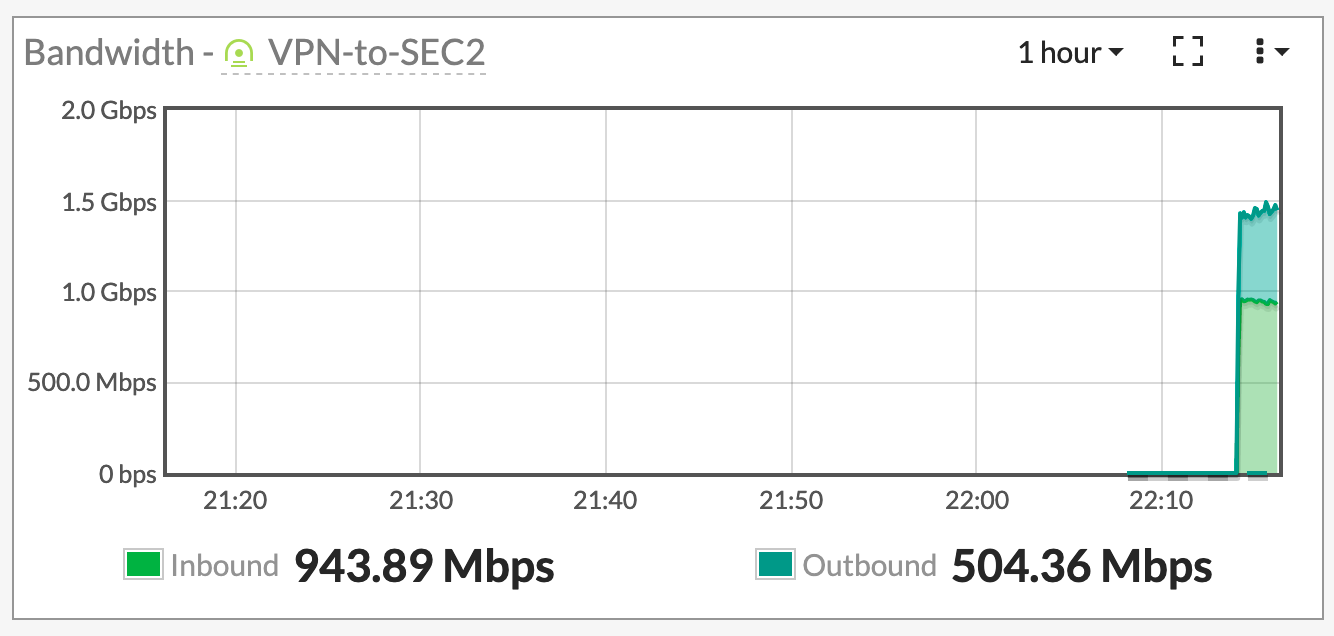
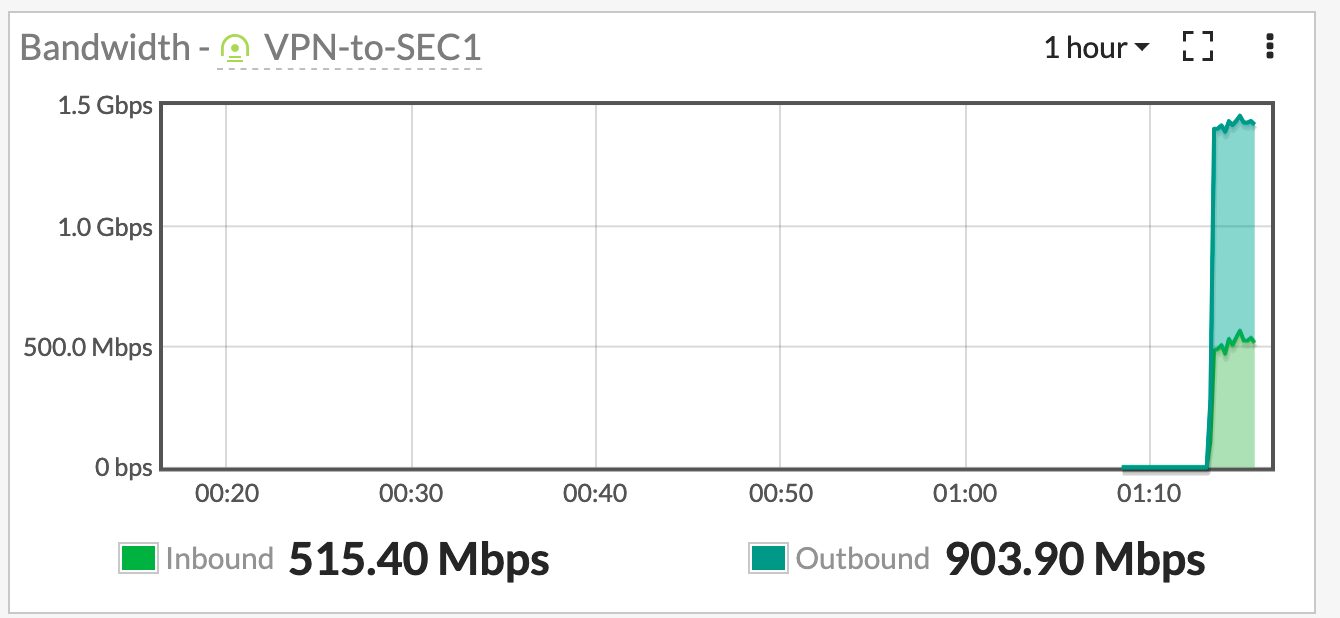
Hope this helps
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
