In FortiOS 7.4, Fortinet enhanced the ability to do... Full Story
By Manny Fernandez
January 1, 2020
Troubleshooting BGP on Fortigate Firewalls
In my previous article regarding Wrong Way I did a lot of BGP troubleshooting and thought I would write an article here to bring in 2020.
Note: All IP addresses are fake and have been modified or redacted.
Basics
Border Gateway Protocol or BGP is a routing protocol that was designed to be used on the Internet but over time has found its way into the Enterprise space. It is not the fastest protocol, and that is by design. Imagine an Internet connection for an ISP that is bouncing up and down every few seconds. I know I would hate it. Originally based on RFC 1267 in 1991 it has gone through its iterations. Currently RFC 4271.
BGP is based on TCP (Transmission Control Protocol). It uses port 179 to communicate. Since it is based on TCP, in order for it to communicate with its neighbor (the other side of a BGP connection), there needs to be a three-way handshake (SYN, SYN/ACK, ACK). Those familiar with BGP in Cisco will understand BGP on the Fortigate or any standards based solution. I always say “Bold is Bold” It does not matter if you are doing BOLD in Word, Pages, Libre Office, or Google Docs. I always tell folks to learn the concepts because platform come and go….. Except for FortiOS of course 🙂
BGP Initiation Flow
The diagram below is a basic data flow. I will explain each of the sections below.
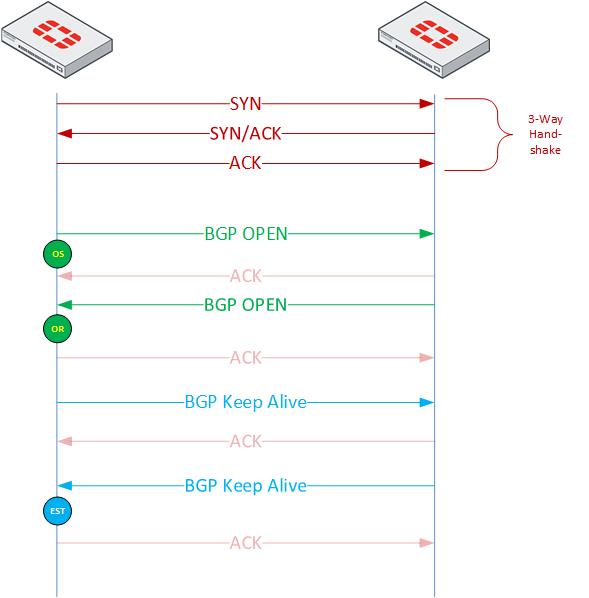
3-Way Handshake – The initial 3-Way Handshake is your standard 3-Way hand shake. You will see the initial packet (SYN) sourced on a high port destined to TCP 179.
BGP Open – (Send or Receive) In the BGP Open packet, the device will send:
- BGP version (4 or 6)
- Its ASN
- Hold Time
- BGP Identifier (Router ID)
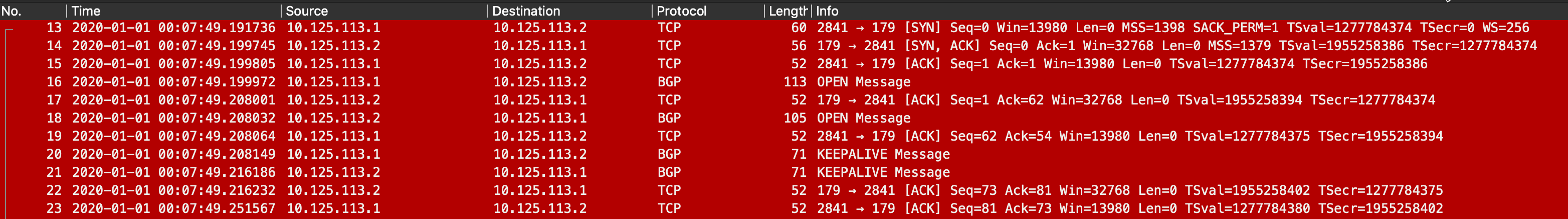
You can follow the pcap against the flow diagram above it. You can see the TCP 179 SYN packet and all the corresponding connections.
Fortinet Specific Commands
Summary Output
Your first step in troubleshooting is to see what the status is of the neighbor. One of the easies commands to run is:
get router info bgp summary
This command give you useful information for your troubleshooting steps.
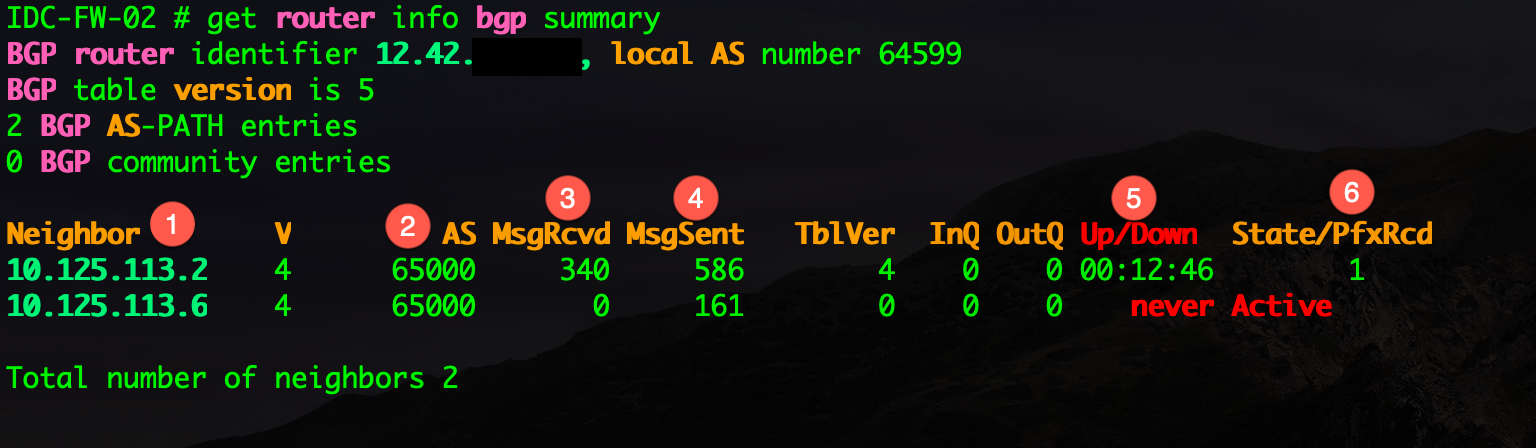
- Shows you the neighbor
- Shows you the remote ASN (Autonomous System Number).
- Shows the number of messages you have received.
- Shows the messages you have send to this neighbor
- Shows the uptime for the BGP session.
- Shows the number of prefix (routes) you have received.
Routes You Are Advertising
Now if you want to see what routes you are advertising to your neighbor run the following command
get router info bgp neighbors 10.125.113.2 advertised-routes
The above command will tell you what routes YOU are sending to the remote firewall/router.
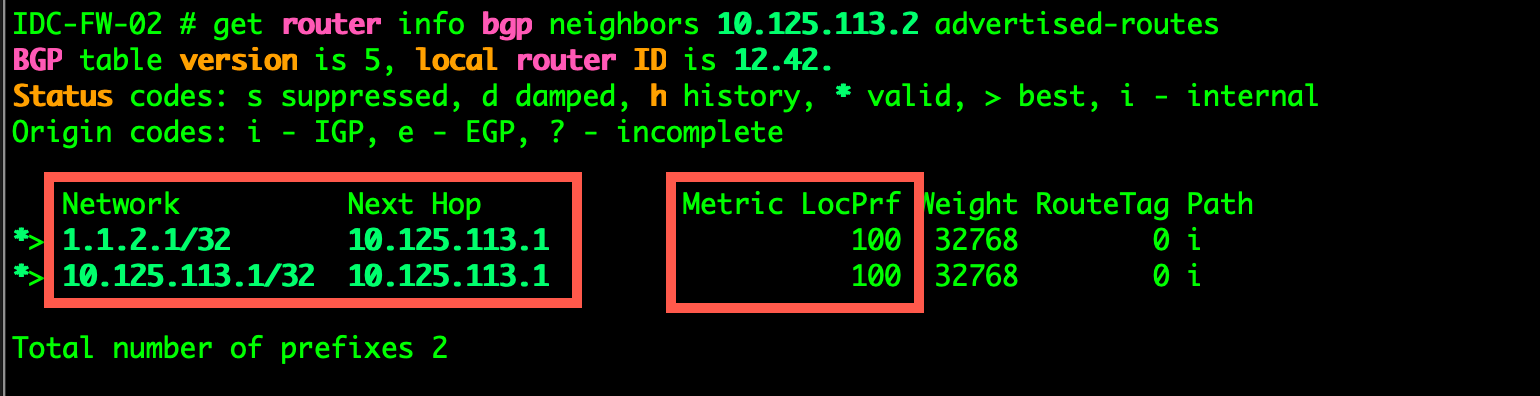
Here you can see the two networks we are advertising. The 1.1.2.1 is a loopback interface I created to test.
Routes You Are Receiving
Now to see what routes the remote device is sending you. You will be able to see it based on neighbor IP address.
get router info bgp neighbors 10.125.113.2 received-routes
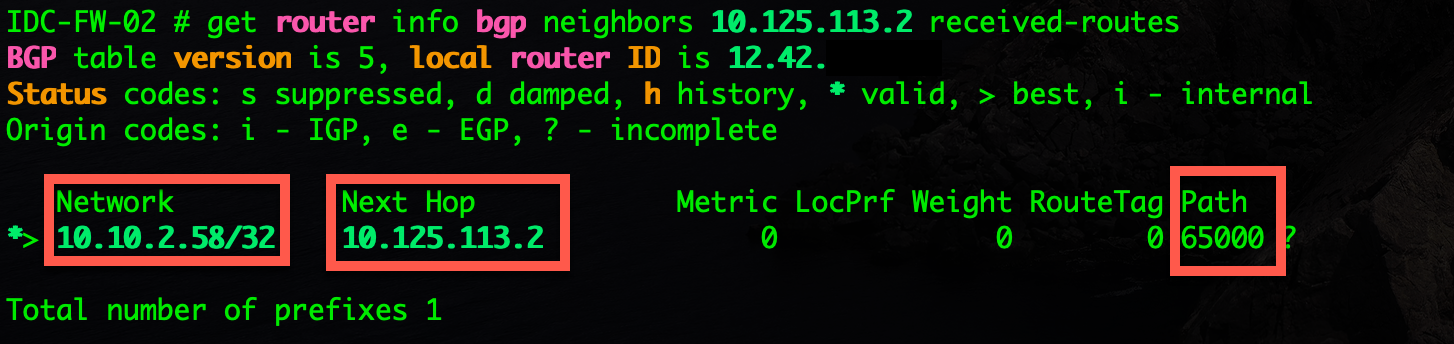
Here we can see that the remote (Neighbor 10.125.113.2) is sending us one host 10.10.2.58 and is setting itself as the next hop.
Prefix Lists
To filter routes either sending or receiving, the easiest way is to useprefix-lists
config router prefix-list
edit "Inbound-from-ASA"
config rule
edit 1
set prefix 10.10.2.58 255.255.255.255
unset ge
unset le
next
edit 2
set prefix 1.1.2.2 255.255.255.255
unset ge
unset le
next
end
next
edit "Outbound-to-ASA-P"
config rule
edit 1
set prefix 10.125.113.0 255.255.255.252
unset ge
unset le
next
end
Above you can see I have two prefix-lists created. I have one to filter out the routes being sent to me and the second is so I can filter what gets sent to them.
How to Use Prefix-List
Once you have created the prefix-lists you can now apply them to your config.
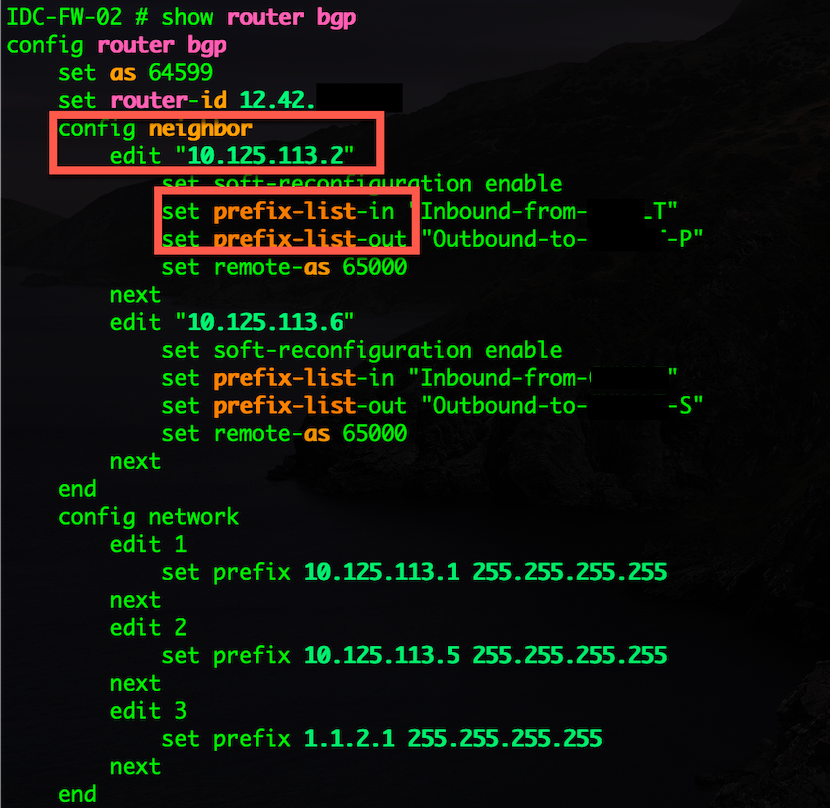
As you can see above, I am assigning the respective prefix list to either IN or OUT
Showing BGP Routes
To display the BGP routes in your routing table
get router info routing-table bgp
This will show you ALL BGP routes your Fortigate has learned.
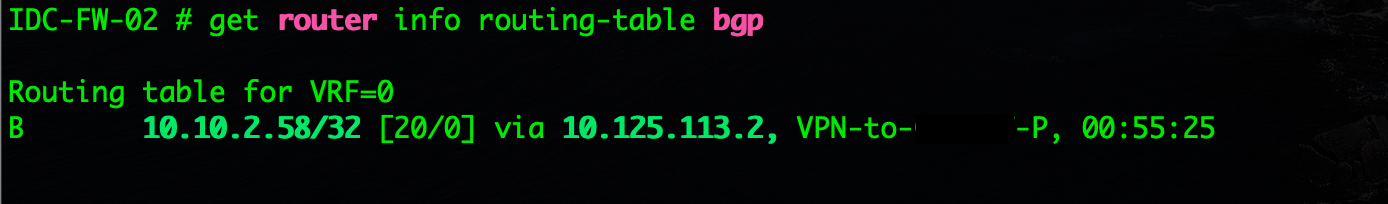
As you can see above, I am learning the 10.10.2.58 and you can see the B at the left which represents BGP.
Flow Filtering
If you want to see the traffic via the command line, you can run the following filtering commands and then turn on the debug.
diag debug flow filter addr 10.125.113.2 diag debug flow filter dport 179 diag debug flow trace start 999 diag debug en
Sniffer Commands from the CLI
diag sniffer packet any "host 10.125.113.2 and port 179" 4 0 a
This will capture packets from 10.125.113.2 that are using TCP 179.
Hope this helps
Recent posts
-

-

Apple shortcuts have been an amazing addition to IOS. ... Full Story
-

Years ago, when I started using FortiGates, I had... Full Story
