At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
February 2, 2020

Packet Capture on FortiSwitch
While I was troubleshooting my bridging lab article, I stumbled onto a great feature in the FortiSwitch. I was instantly stoked since packet capture is my favorite thing to do. I have a motto, “When in doubt, sniff it out“, anyone who knows me and has worked with me has heard me say it. I found that you can do packet captures on the FortiSwitch.
Here we go:
Connecting to the Switch
You can either ssh using anything from PuTTy to SecureCRT or even from the command line of macOS or Linux with ssh admin@x.x.x.x where x.x.x.x is the management IP of the switch. Also modify the username if admin is not being used.
Once connected, you will need to run the following:
config switch interface
Next you will need to choose the port you want to capture packets from, in my example, it was port8
edit port8
Next we are going to enable the sampling on this port
set packet-sampler enabled
Next we need to configure the sample-rate
set packet-sample-rate 1
And then you will want to run the
diag sniffer packet sp8 #8 because that is my sample, but replace 8 with whatever port you are using.
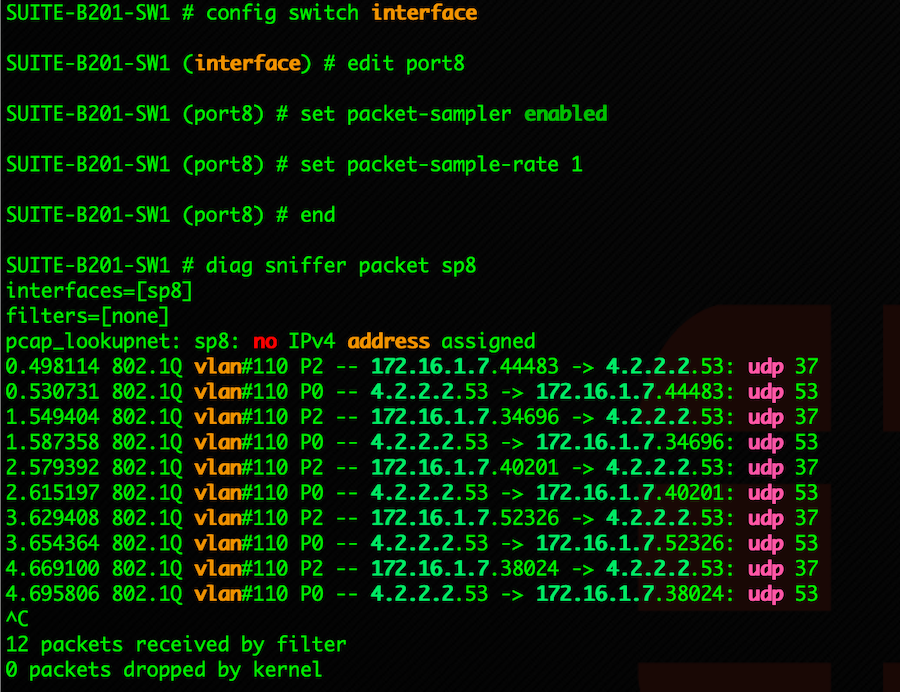
Above, you can see the output of the diag sniffer packet sp8 without anything else. This is usually enough to diagnose a problem. In this case, I was trying to identify if an IP Phone was requesting a DHCP address. I was able to see this, and then saw said phone doing DNS queries to 4.2.2.2 and subsequent responses from the same.
However, you may need to export this into a PCAP, and once again there is a way. Similar to the Fortigate and the diag sniffer command, you can add the "" 6 0 a and you will be able to export this with a copy/paste and run against the perl script that converts to a PCAP file.

There you have it. Its a beautiful thing.
Hope this helps
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
