At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
May 6, 2020

Connect to both Fortigates in an HA Cluster Separately
When you configure a FortiGate in HA, normally, there is no way connect to the second box unless you ssh to the master and then connect via it to the secondary. The only way to connect to the secondary box was using the following command:
execute ha manage 0 %admin-account%
There is another option named Reserved Management Interface . Using this option, you can connect to each of the devices independently. The use case for this would be to poll SNMP on each of the devices.
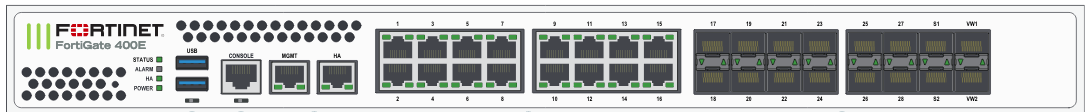
In my example, I am using a 400E. The 400E has a single HA interface so I am going to use port16 as the secondary HA and port15 as the management interface.
On the Master Firewall
Interface Configuration
You will need to configure the port with the correct IP address it will use for the management
config system interface
edit "port15"
set vdom "root"
set ip 10.10.10.140 255.255.255.0
set allowaccess ping https ssh http fgfm
set type physical
set dedicated-to management
set role lan
set snmp-index 2
next
end
In the above snippet, we are configuring this firewall with the .140 IP address. The secondary will be .141.
HA Configuration
Now we need to configure the HA portion on the master firewall.
config system ha
set group-name "HA-GROUP"
set mode a-p
set password ENC <removed>
set hbdev "ha" 50 "port16" 100
set override disable
set monitor "port3" "port1" (Represent inside and outside)
set session-pickup enable
set priority 180
config ha-mgmt-interfaces
edit 1
set interface "port15"
set gateway 10.10.10.1
next
end
end
I always set the master by using a priority of 180 since the default is 120
Routing Table
We can see that this ha configuration has the gateway of 10.10.10.1 under the ha-mgmt-interfaces section. This acts as a VRF of sorts. This is a separate routing instance for the new management interfaces.
On the Secondary Firewall
Interface Configuration
On the secondary FortiGate, you can drop this configlette into the CLI. This will configure the management interface for the secondary FortiGate. This interface will NOT sync with the master.
config system interface
edit "port15"
set vdom "root"
set ip 10.10.10.141 255.255.255.0
set allowaccess ping https ssh http fgfm
set type physical
set dedicated-to management
set role lan
set snmp-index 2
next
end
HA Configuration
Next we will configure the HA portion on the secondary FortiGate.
config system ha
set group-name "HA-GROUP"
set mode a-p
set password ENC <removed>
set hbdev "ha" 50 "port16" 100
set override disable
set monitor "port3" "port1" (Represent inside and outside)
set session-pickup enable
set priority 120
config ha-mgmt-interfaces
edit 1
set interface "port15"
set gateway 10.10.10.1
next
end
end
GUI
In the GUI, you can also configure this interface. Since I normally use the CLI to do the HA configuration, I do not use the GUI as much but it IS available.
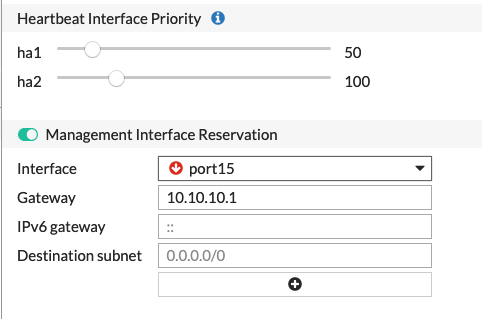
Simply enable the Management Interface Reservation but clicking the button and making sure it goes green.
Choose the interface and then enter the Gateway
You will need to manually configure each Management Interface IP address separately either through the GUI or the CLI.
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
