At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
May 22, 2020

EMS for Internal and External FortiClients
When deploying EMS in your environment, you want to make sure the users can communicate back to EMS when connected internally as well as externally. Is seems that there is some confusion so I decided to write this article on how I have deployed this.
EMS
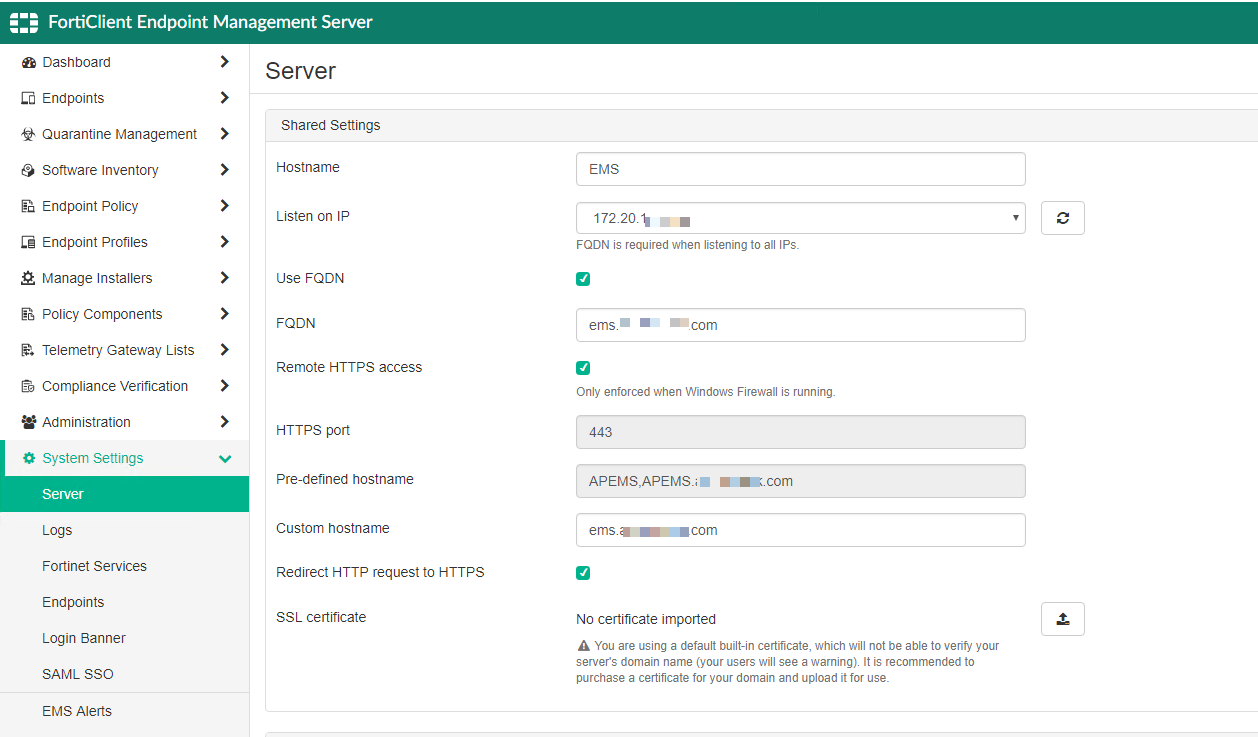
Here we can see the hostname and the Listen on IP with the IP address of your server.
Check the Use FQDN radio button and then enter the FQDN (Fully Qualified Domain Name) e.g. ems.domain-name.com.
You will want to enable the Remote HTTPS access and enter the necessary port.
On the Pre-defined hostname you will see the actual hostname, as well as the FQDN.
Enter the FQDN in the Custom Hostname section.
You can add a certificate and I recommend it. In this example, there is none.
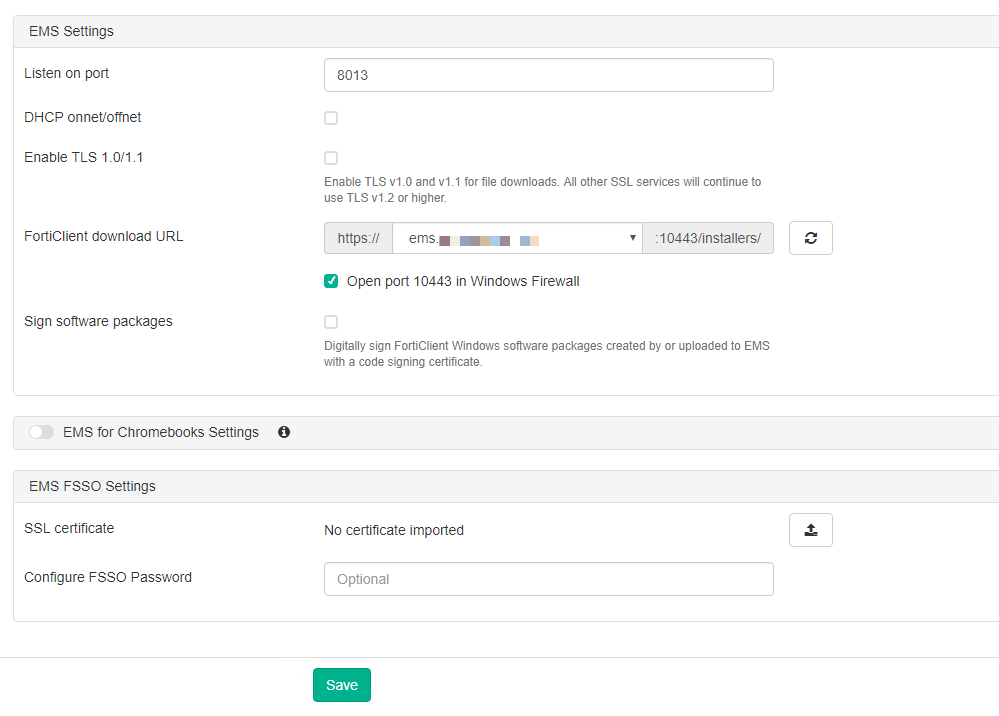
Once you fill out the information on the top screenshot, you should have the FQDN listed in the drop down. You will want to make sure that you click the Open port 10443 in Windows Firewall.
DNS
Now for the second part, DNS. You will need to have an A record for your external as well as your internal. This can be tricky if you have different internal domain name vs external such as my environment:
Internal - myinfoseclab.local External - myinfoseclab.com
In my case, I created an internal zone file for the .com internally which resolved to the internal IP address of the EMS server. And then externally, it will resolve to the VIP.
FortiGate
Then you will need to create a VIP and the policies. Here is my policy
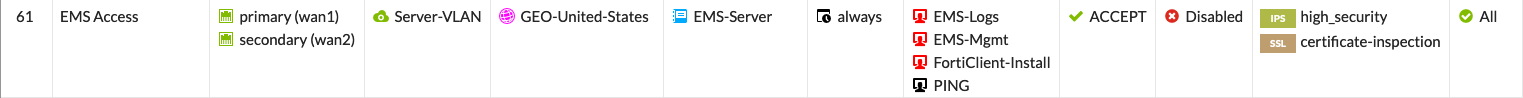
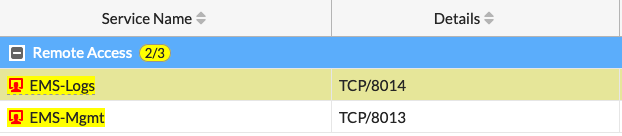
Here we can see that WAN1 and WAN2 as the incoming interface, and the outgoing interface. I have created a geo object for US addresses, going to my internal EMS with the custom service ports.
Hope this helps
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
