In FortiOS 7.4, Fortinet enhanced the ability to do... Full Story
By Manny Fernandez
August 30, 2022

Extracting Your Private Key from a .pfx certificate
I had a customer that installed a wildcard certificate on an Exchange server. Later they wanted to use the same wildcard on another server, which is the purpose of the wildcard certificate, and he did not have the private key for the certificate. Normally, you need three things to use a wildcard certificate: certificate file, the key file (Unencrypted) and the password used.
In this example, I am going to use a fictitious certificate.
First things first. I went to the Exchange Server where they had the certificate installed. They had created the CSR on this server, thus the private key was ALSO on this server. Went to the Start button and type Certificate and used the Windows native certificate utility. Once there, I found the certificate in question and right-clicked on it and chose to export. You will want to choose the export with private key as the option and ensure to choose .pfx as the type.
You will now need OpenSSL available by default on macOS and Linux. For Windows, you will need to download and install it.
Once you have the certificate file in PFX and OpenSSL, you are ready to go:
The first thing we are going to do is extract the encrypted key file from the pfx certificate. You are going to need the password that was created when the original CSR was being created.
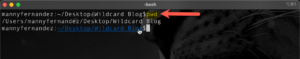
But before that, you want to make sure you are in the correct folder. You can give the pwd in macOS or Linux which stands for Print Working Directory (when people called then directories and not folders).
As you can see, I have my newly exported .pfx file.
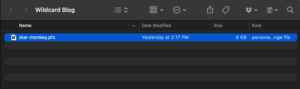
In my example, I named it star-monkey.pfx (you can name it whatever you want but I like having the star or * in the name so I know its a wildcard certificate).
Extracting the Encrypted Private Key
Now, we are going to run our first OpenSSL command.
openssl pkcs12 -in star-monkey.pfx -nocerts -out monkey-encrypted.key
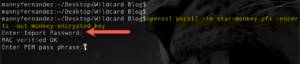
As you can see in the screenshot, it will ask you for the password. You are looking for the MAC verified OK output.
This output file will be encrypted and not really useful in most cases.
![]()
For validation, run the ls command (or dir in Windows)
Extracting the Certificate Portion of the Key
The next command will extract the certificate portion from the .pfx file, once again, you will need the password.

As you can see, we are once again looking for the MAC verified OK output as we did in the previous command.
Decrypting the Encrypted Key file from the .pfx certificate
Finally, we will run the following command to decrypt the encrypted private key.
openssl rsa -in monkey-encrypted.key -out monkey.key
This will ask you for the original password as well as the password you used to export it from Windows in the above step.
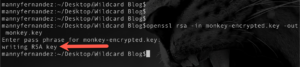
Now you can successfully import this certificate, key and password into nay server or firewall.
Hope this helps.
Recent posts
-

-

Apple shortcuts have been an amazing addition to IOS. ... Full Story
-

Years ago, when I started using FortiGates, I had... Full Story
