In FortiOS 7.4, Fortinet enhanced the ability to do... Full Story
By Manny Fernandez
February 22, 2021

FortiGate AD Polling with Windows Server 2003
Today, I was helping a customer set up Active Directory polling from a FortiGate firewall using the External Connector which is included in 6.2 and above. With this feature, you are able to poll active directory users directory from a Windows Domain Server. However this was failing and customer could not figure out why it was not working. It took a little bit to figure out but here is what I found.
I will start by telling you what I found. The customer was running Windows Server 2003. I know, that is crazy, but it is what the customer was running.
After setting up the external connector we were getting the following:
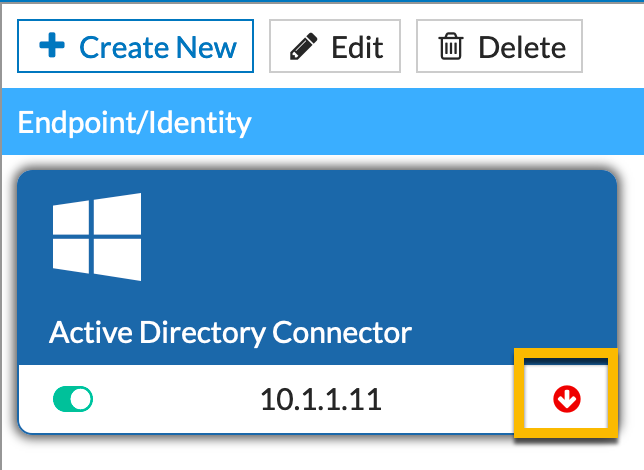
We validated that the LDAP Server under the User & Authentication
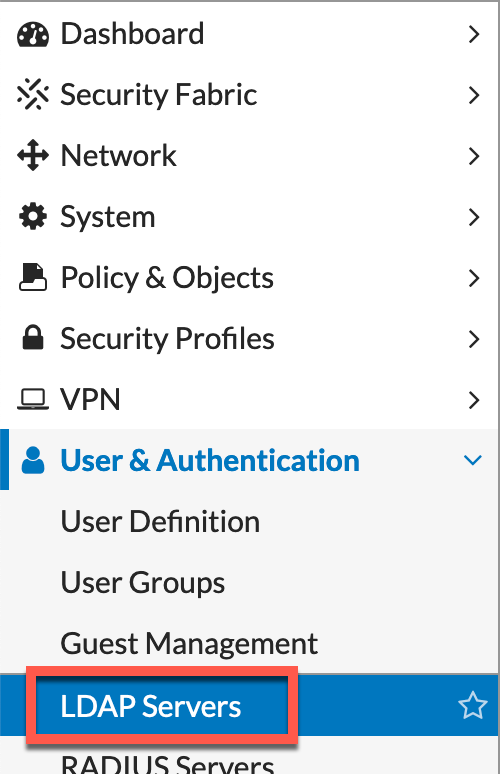
To begin, we started with some basic dia debug commands to see what was going on.
diag debug application fssod -1
The output was as follows:
[client_pkt_process:794] Received heartbeat
[handle_reply:491] wrong format of data status. len 8 <> 4.
[handle_reply:491] wrong format of data status. len 8 <> 4.
[handle_reply:491] wrong format of data status. len 8 <> 4.
[handle_reply:491] wrong format of data status. len 8 <> 4.
[handle_reply:491] wrong format of data status. len 8 <> 4.
[handle_reply:491] wrong format of data status. len 8 <> 4.
Next step was to get a packet capture from the FortiGate to see what was going on.
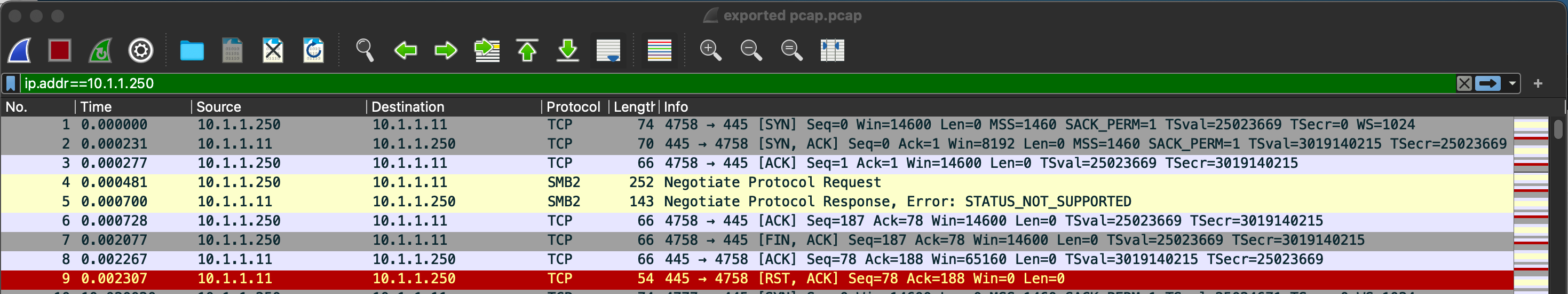
As you can see in the screenshot above, we can see packets 4 & 5 are the SMBv2 connection the FortiGate is trying with. We can see the STATUS_NOT_SUPPORTED. This is what gave me a huge clue.
I then went back to the FortiGate CLI and ran an additional debug command
diag debug application smbcd -1
Here is the output
PULM-FW-01 # smbcd: smbcd_process_request:981 got cmd id: 6
smbcd: smbcd_process_request:994 got rpc log field.
smbcd: smbcd_process_request:1006 got rpc username: administrator@<REMOVED>.local
smbcd: smbcd_process_request:1012 got rpc password: XXXXXXXX
smbcd: smbcd_process_request:1016 got rpc port: 0
smbcd: smbcd_process_request:1022 got rpc logsrc: security
smbcd: smbcd_process_request:1000 got rpc server: 10.1.1.11
smbcd: smbcd_process_request:1049 got VFID, 0
smbcd: smbcd_process_request:1182 got rpc eventlog read command
smbcd: rpccli_eventlog_open:121 /code/FortiOS/fortinet/daemon/smbcd/smbcd_eventlog.c-121: connect err(NT_STATUS_NOT_SUPPORTED)
smbcd: rpc_cmd_eventlog_read:930 open rpc err(10.1.1.11:administrator@<REMOVED>.local:0) from security log!, Please check correct server name, user name, password, port and log
source
This did it for me. I wanted to see what version of SMB the server was running.
I RDP’d to the server and launched the Powershell console. I tried running the Get command from the powershell but since it was an older Windows Server, it did not work
Get-SmbConnection
So I went to Google and found the following command
sc.exe
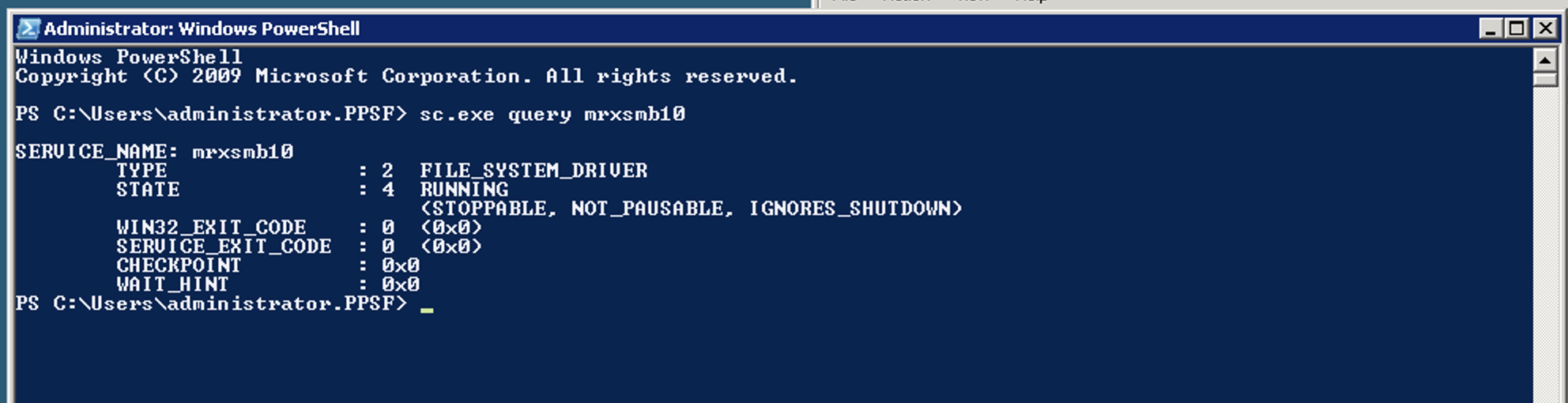
As you can see in the screenshot, we can see that we are running SMBv1 (mrxsmb01). When querying for v2, it fails.
This is how v1 and v2 looks
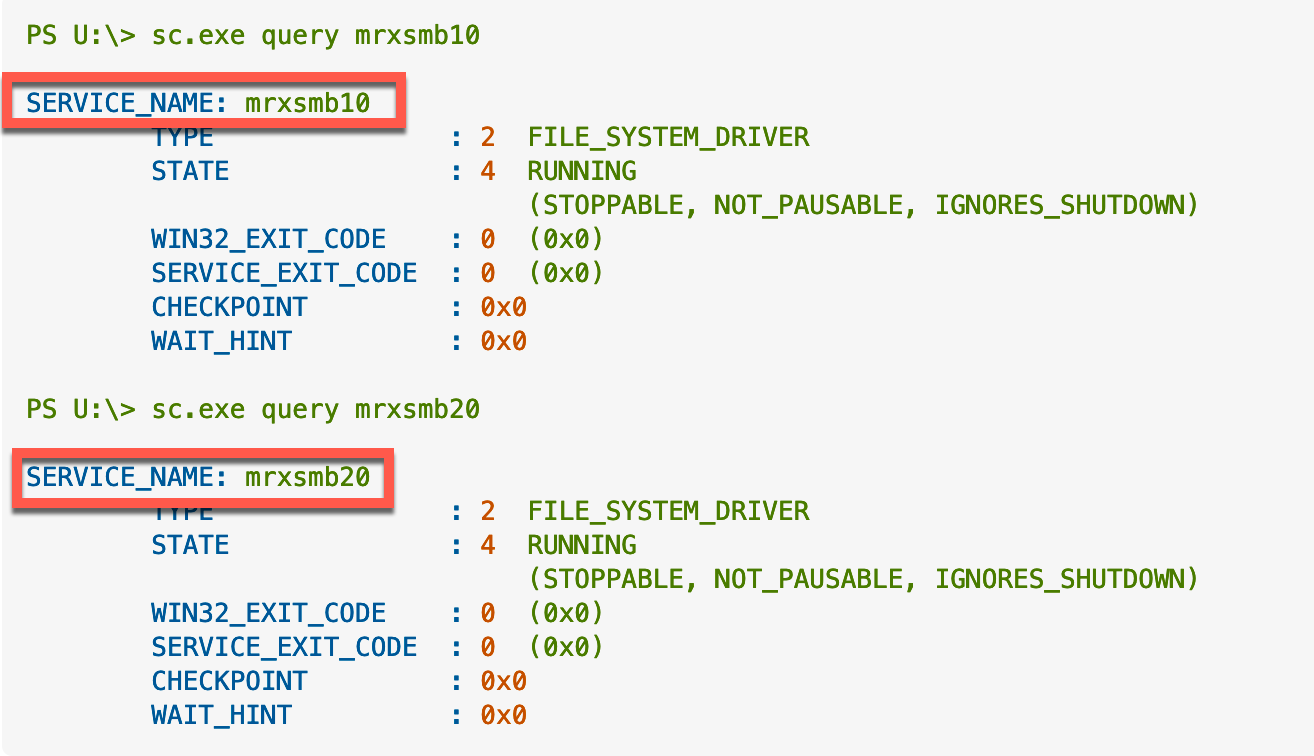
After upgrading the DC to 2019, the problem went away.
Hope this helps.
Recent posts
-

-

Apple shortcuts have been an amazing addition to IOS. ... Full Story
-

Years ago, when I started using FortiGates, I had... Full Story
