In FortiOS 7.4, Fortinet enhanced the ability to do... Full Story
By Manny Fernandez
March 12, 2018

Fortigate ‘HA’ configuration explained
Last month I wrote a blog post about HA on the ASA. Today, I am writting one on Fortigate HA. When you configure HA on the Fortigate, it is required to have the same hardware, and FortiOS version. Before we begin configuring HA, rename the boxes with descriptive names referring to Primary and Secondary (whatever works for you). Register and apply licenses to both FortiGates before adding them to the cluster. This includes FortiCloud activation and FortiClient licensing, and entering a license key if you purchased more than 10 Virtual Domains (VDOMS)
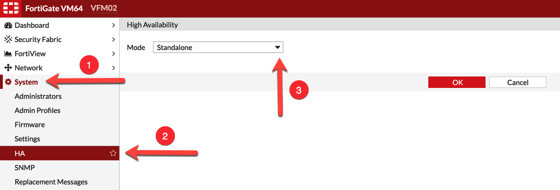
To configure HA on the Fortigate, go to SYSTEM —> HA Then select the mode. Your options are Standalone (the default), Active/Active and Active/Passive.
NOTE: I do not suggest Active/Active since you do not want to be in a scenario where you have 70% load on one box and 70% load on the other. Once you lose a box, you will have 40% unaccounted for.
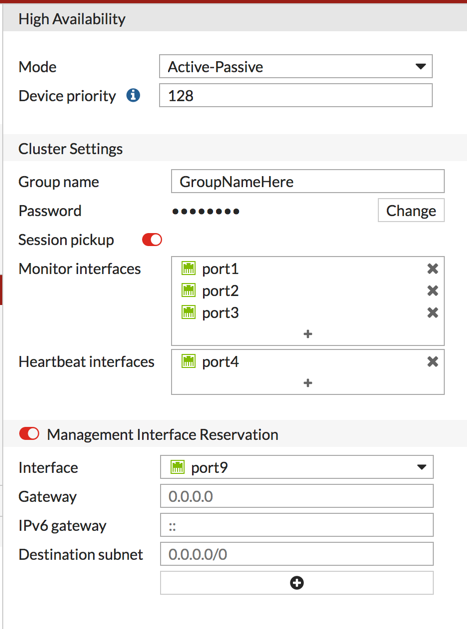
Device Priority – This setting will tell the cluster which device will be the Master and which will be the slave. The higher the priority the higher probability of becoming ‘master’. Default is 128

Group Name – Use the group name to identify the cluster. The maximum length of the group name is 32 characters. The group name must be the same for all cluster units before the cluster units can form a cluster. After a cluster is operating, you can change the group name. The group name change is synchronized to all cluster units. The group name appears on the FortiGate dashboard of a functioning cluster as the Cluster Name.
Password – Use the password to identify the cluster. You should always change the password when configuring a cluster. The password must be the same for all FortiGate units before they can form a cluster. When the cluster is operating you can change the password, if required. Two clusters on the same network cannot have the same password.
Session Pickup – If Enable Session Pick-up is not selected, the Fortigates do not maintain an HA session table and most TCP sessions do not resume after a failover. After a device or link failover all sessions are briefly interrupted and must be re-established at the application level after the cluster renegotiates. This can be a huge problem for traffic that is connection oriented and has little resilience (e.g. Citrix ICA connection).
Monitor Interface – These are the interfaces that they Fortigate will montitor for failure. I recommend getting the cluster configured first and THEN add the monitored interface to the config.
Heartbeat Interface – For clusters of two FortiGate units, as much as possible, heartbeat interfaces should be directly connected using patch cables (without involving other network equipment such as switches). If switches have to be used they should not be used for other network traffic that could flood the switches and cause heartbeat delays.
For clusters of three or four FortiGate units, use switches to connect heartbeat interfaces. The corresponding heartbeat interface of each FortiGate unit in the cluster must be connected to the same switch. For improved redundancy use a different switch for each heartbeat interface. In that way if the switch connecting one of the heartbeat interfaces fails or is unplugged, heartbeat traffic can continue on the other heartbeat interfaces and switch.
Terminology Used
Cluster
A group of FortiGate units that act as a single virtual FortiGate unit to maintain connectivity even if one of the FortiGate units in the cluster fails.
Cluster unit
A FortiGate unit operating in a FortiGate HA cluster.
Device failover
Device failover is a basic requirement of any highly available system. Device failover means that if a device fails, a replacement device automatically takes the place of the failed device and continues operating in the same manner as the failed device.
Failover
A FortiGate unit taking over processing network traffic in place of another unit in the cluster that suffered a device failure or a link failure.
Failure
A hardware or software problem that causes a FortiGate unit or a monitored interface to stop processing network traffic.
FGCP
The FortiGate clustering protocol (FGCP) that specifies how the FortiGate units in a cluster communicate to keep the cluster operating.
Full mesh HA
Full mesh HA is a method of removing single points of failure on a network that includes an HA cluster. FortiGate models that support redundant interfaces can be used to create a cluster configuration called full mesh HA. Full mesh HA includes redundant connections between all network components. If any single component or any single connection fails, traffic switches to the redundant component or connection.
HA virtual MAC address
When operating in HA mode, all of the interfaces of the primary unit acquire the same HA virtual MAC address. All communications with the cluster must use this MAC address. The HA virtual MAC address is set according to the group ID.
Heartbeat
Also called FGCP heartbeat or HA heartbeat. The heartbeat constantly communicates HA status and
synchronization information to make sure that the cluster is operating properly.
Heartbeat device
An Ethernet network interface in a cluster that is used by the FGCP for heartbeat communications among cluster units.
Heartbeat failover
If an interface functioning as the heartbeat device fails, the heartbeat is transferred to another interface also configured as an HA heartbeat device.
Hello state
In the hello state a cluster unit has powered on in HA mode, is using HA heartbeat interfaces to send hello packets, and is listening on its heartbeat interfaces for hello packets from other FortiGate units. Hello state may appear in HA log messages.
High availability
The ability that a cluster has to maintain a connection when there is a device or link failure by having another unit in the cluster take over the connection, without any loss of connectivity. To achieve high availability, all FortiGate units in the cluster share session and configuration information.
Interface monitoring
You can configure interface monitoring (also called port monitoring) to monitor FortiGate interfaces to verify that the monitored interfaces are functioning properly and connected to their networks. If a monitored interface fails or is disconnected from its network the interface leaves the cluster and a link failover occurs. For more information about interface monitoring, see Link failover (port monitoring or interface monitoring).
Link failover
Link failover means that if a monitored interface fails, the cluster reorganizes to re-establish a link to the network that the monitored interface was connected to and to continue operating with minimal or no disruption of network traffic.
Load balancing
Also known as active-active HA. All units in the cluster process network traffic. The FGCP employs a technique similar to unicast load balancing. The primary unit interfaces are assigned virtual MAC addresses which are associated on the network with the cluster IP addresses. The primary unit is the only cluster unit to receive packets sent to the cluster. The primary unit can process packets itself, or propagate them to subordinate units according to a load balancing schedule. Communication between the cluster units uses the actual cluster unit MAC addresses.
Monitored interface
An interface that is monitored by a cluster to make sure that it is connected and operating correctly. The cluster monitors the connectivity of this interface for all cluster units. If a monitored interface fails or becomes disconnected from its network, the cluster will compensate.
Primary unit
Also called the primary cluster unit, this cluster unit controls how the cluster operates. The primary unit sends hello packets to all cluster units to synchronize session information, synchronize the cluster configuration, and to synchronize the cluster routing table. The hello packets also confirm for the subordinate units that the primary unit is still functioning. The primary unit also tracks the status of all subordinate units. When you start a management connection to a cluster, you connect to the primary unit. In an active-passive cluster, the primary unit processes all network traffic. If a subordinate unit fails, the primary unit updates the cluster configuration database. In an active-active cluster, the primary unit receives all network traffic and re-directs this traffic to subordinate
units. If a subordinate unit fails, the primary unit updates the cluster status and redistributes load balanced traffic to other subordinate units in the cluster. The FortiGate firmware uses the term master to refer to the primary unit.
Session failover
Session failover means that a cluster maintains active network sessions after a device or link failover. FortiGate HA does not support session failover by default. To enable session failover you must change the HA configuration to select Enable Session Pick-up.
Session pickup
If you enable session pickup for a cluster, if the primary unit fails or a subordinate unit in an active-active cluster fails, all communication sessions with the cluster are maintained or picked up by the cluster after the cluster negotiates to select a new primary unit.
If session pickup is not a requirement of your HA installation, you can disable this option to save processing resources and reduce the network bandwidth used by HA session synchronization. In many cases interrupted sessions will resume on their own after a failover even if session pickup is not enabled. You can also enable session pickup delay to reduce the number of sessions that are synchronized by session pickup.
Standby state
A subordinate unit in an active-passive HA cluster operates in the standby state. In a virtual cluster, a subordinate virtual domain also operates in the standby state. The standby state is actually a hot-standby state because the subordinate unit or subordinate virtual domain is not processing traffic but is monitoring the primary unit session table to take the place of the primary unit or primary virtual domain if a failure occurs. In an active-active cluster all cluster units operate in a work state. When standby state appears in HA log messages this usually means that a cluster unit has become a subordinate unit in an active-passive cluster or that a virtual domain has become a subordinate virtual domain.
State synchronization
The part of the FGCP that maintains connections after failover.
Subordinate unit
Also called the subordinate cluster unit, each cluster contains one or more cluster units that are not functioning as the primary unit. Subordinate units are always waiting to become the primary unit. If a subordinate unit does not receive hello packets from the primary unit, it attempts to become the primary unit. In an active-active cluster, subordinate units keep track of cluster connections, keep their configurations and routing tables synchronized with the primary unit, and process network traffic assigned to them by the primary unit. In an active-passive cluster, subordinate units do not process network traffic. However, active-passive subordinate units do keep track of cluster connections and do keep their configurations and routing tables synchronized with the primary unit.
The FortiGate firmware uses the terms slave and subsidiary unit to refer to a subordinate unit.
Virtual clustering
Virtual clustering is an extension of the FGCP for FortiGate units operating with multiple VDOMS enabled. Virtual clustering operates in active-passive mode to provide failover protection between two instances of a VDOM operating on two different cluster units. You can also operate virtual clustering in active-active mode to use HA load balancing to load balance sessions between cluster units. Alternatively, by distributing VDOM processing between the two cluster units you can also configure virtual clustering to provide load balancing by distributing sessions for different VDOMs to each cluster unit.
Work state
The primary unit in an active-passive HA cluster, a primary virtual domain in a virtual cluster, and all cluster units in an active-active cluster operate in the work state. A cluster unit operating in the work state processes traffic, monitors the status of the other cluster units, and tracks the session table of the cluster. When work state appears in HA log messages this usually means that a cluster unit has become the primary unit or that a virtual domain has become a primary virtual domain.
Leave a comment
Recent posts
-

-

Apple shortcuts have been an amazing addition to IOS. ... Full Story
-

Years ago, when I started using FortiGates, I had... Full Story

I’m not that much of a internet reader to be honest but your sites really nice, keep it up! Ill go ahead and bookmark your site to come back later. Cheers
Hello infosecmonkey.com admin, Thanks for the comprehensive post!