At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
February 10, 2022

Geo-Blocking with Local In Policy
Sometimes when you set up a standard policy to geo block some countries, you will still see attacks from certain IP addresses from the very same countries you blocked. This is due to certain allowed access to the FortiGate itself (e.g. IPsec, HTTPS (for admin and Remote Access VPN), BGP, etc.
First thing you will want to do is create an Address object with the public IP of the firewall. You may need to have multiple policies and Address objects to correspond to multiple WAN links.
Next you will need to create GEO objects for each country you want to block. I created an article and have a script that will allow you to import all countries without having to manually enter them.
Create an Address Group and add the countries you want to block. I named my group Blocked-Countries
Next we will create the Local-In Policy
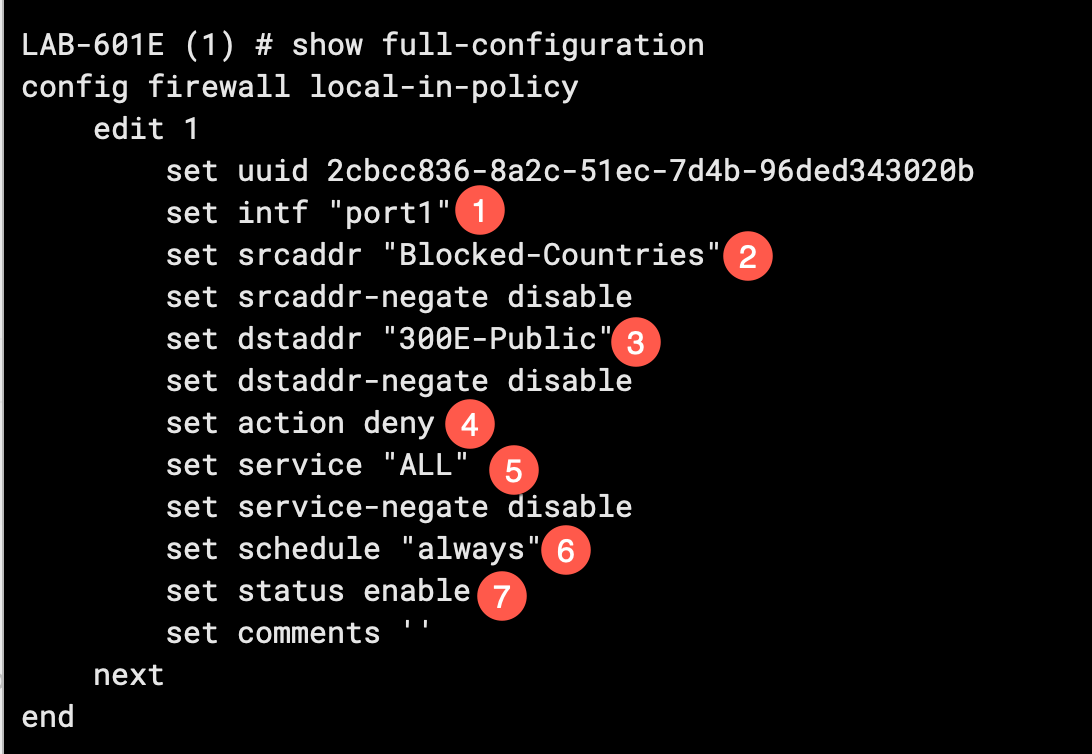
- You will need to enter your port (e.g. WAN1, WAN2, port1, etc)
- Enter the Source address
srcaddrfrom the address group we created earlier. - Here you will need to enter the
addressobject of the firewall’s public IP address. - Next set the action to
Deny - You need to then set the
servicetoALLto cover all ports. You can be specific if you want but for the purposes of blocking countries, you probably want to blockALL. - You want to ensure that this policy is scheduled to
always - Finally, set the status to
enable
You should be good to go.
Hope this helps.
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
