At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
January 23, 2018

SIP Application Layer Gateway – Cisco and Fortinet
SIP ALG is a feature where the firewall will inspect the SIP packets as they egresses the firewall
Purpose of SIP ALG
Fortinet/Cisco
1) Modification of IP addresses in the application payload when NAT is used.
2) Dynamic opening of data ports (“pinholes”) as required to allow audio traffic. Otherwise, firewall policies need to statically open a wide range of ports.
3) Inspection and logging of VoIP traffic (using ALG/Proxy instead of session-helper).
The best way to know if this is causing a problem is to perform a packet capture. You should be able to see if the phone is trying to register with its RFC 1918 address and NOT the NAT’d IP of the ASA/Fortigate.
Fortinet
config system session-helper show
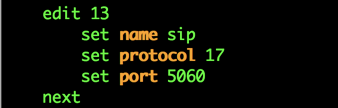
edit 13 set name sip set protocol 17 set port 5060
To remove it:
delete 13 end
In the Cisco world, it is a bit easier. By doing a:
sh run | b policy-map
You will be able to see if SIP inspection is enabled or not
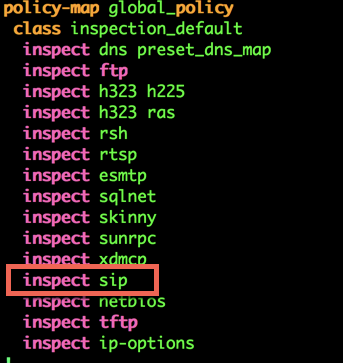
To disable SIP inspection on the ASA based on this example:
fw/sec/act(config)# policy-map global_policy fw/sec/act(config-pmap)# class inspection_default fw/sec/act(config-pmap-c)# no inspect sip
Here is the packet lifecycle on a Fortigate
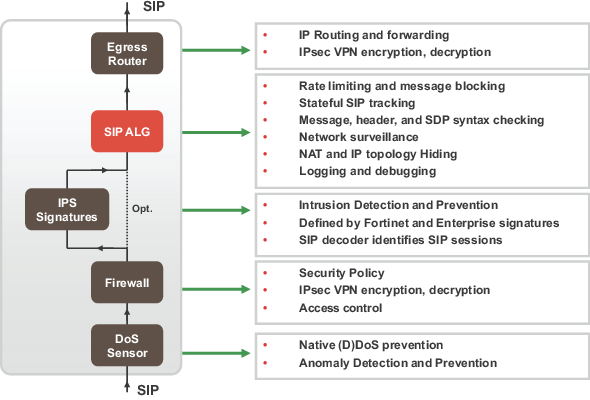
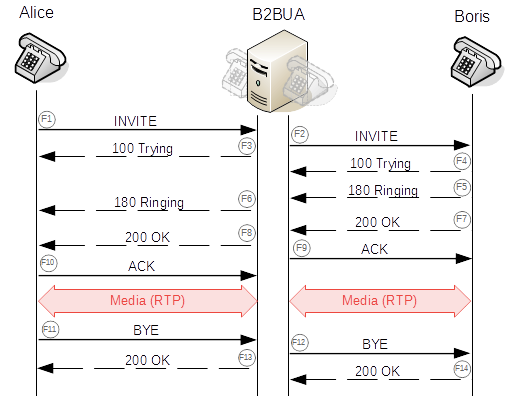
Here is a good overview of the packets involved in a SIP communication
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
