Have you ever ordered a bunch of Fortinet gear... Full Story
By Manny Fernandez
November 15, 2019
Site-to-Site VPN with Checkpoint Stand-Alone
A colleague wanted to test VPNs to multiple platforms. I set up a Checkpoint 1450, PAN 200, and an ASA 5515. This box is running the following:
Configuring The Internet
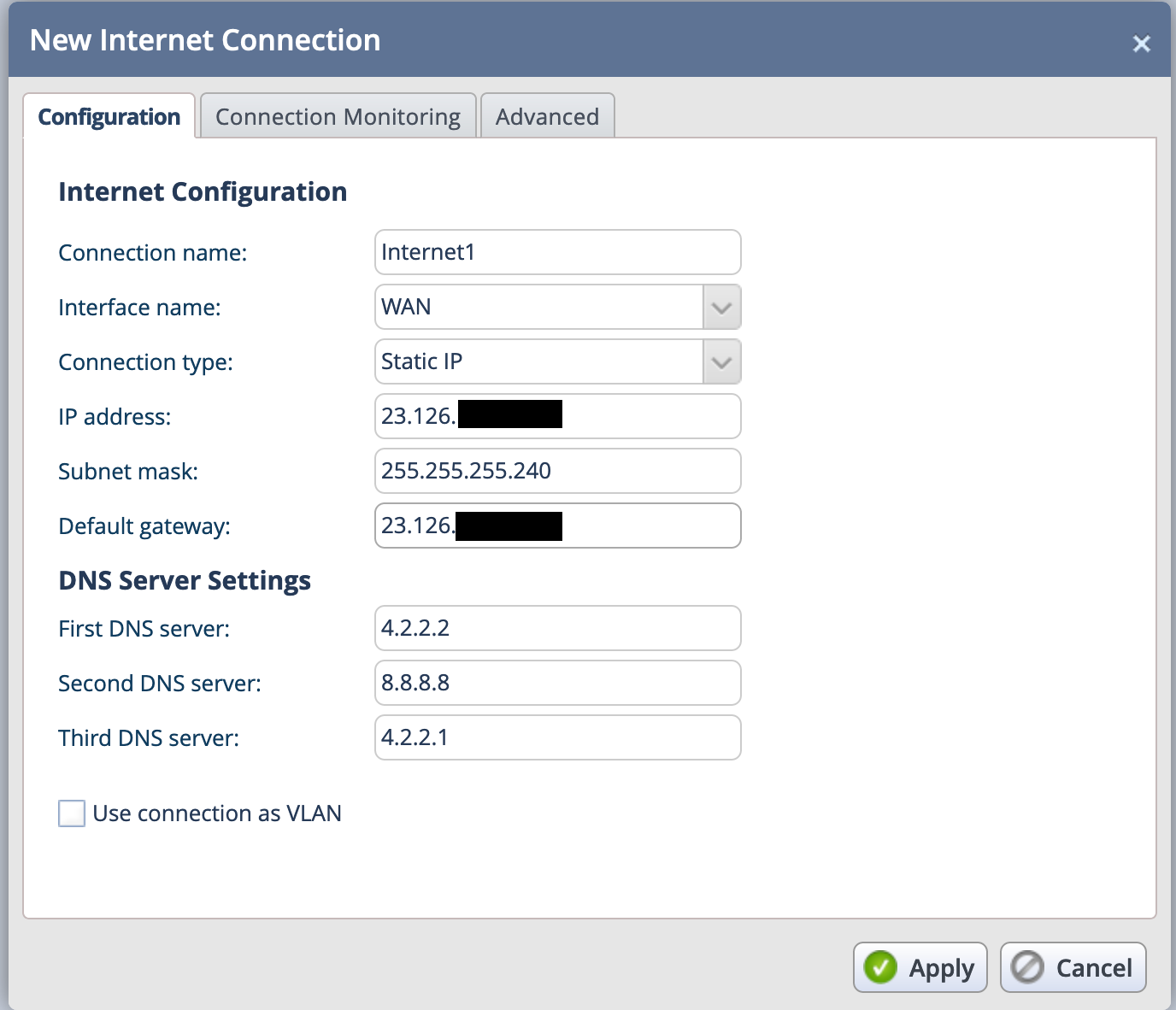
To begin, I needed to configure the Internet side of the Checkpoint Firewall.
Troubleshooting Connection
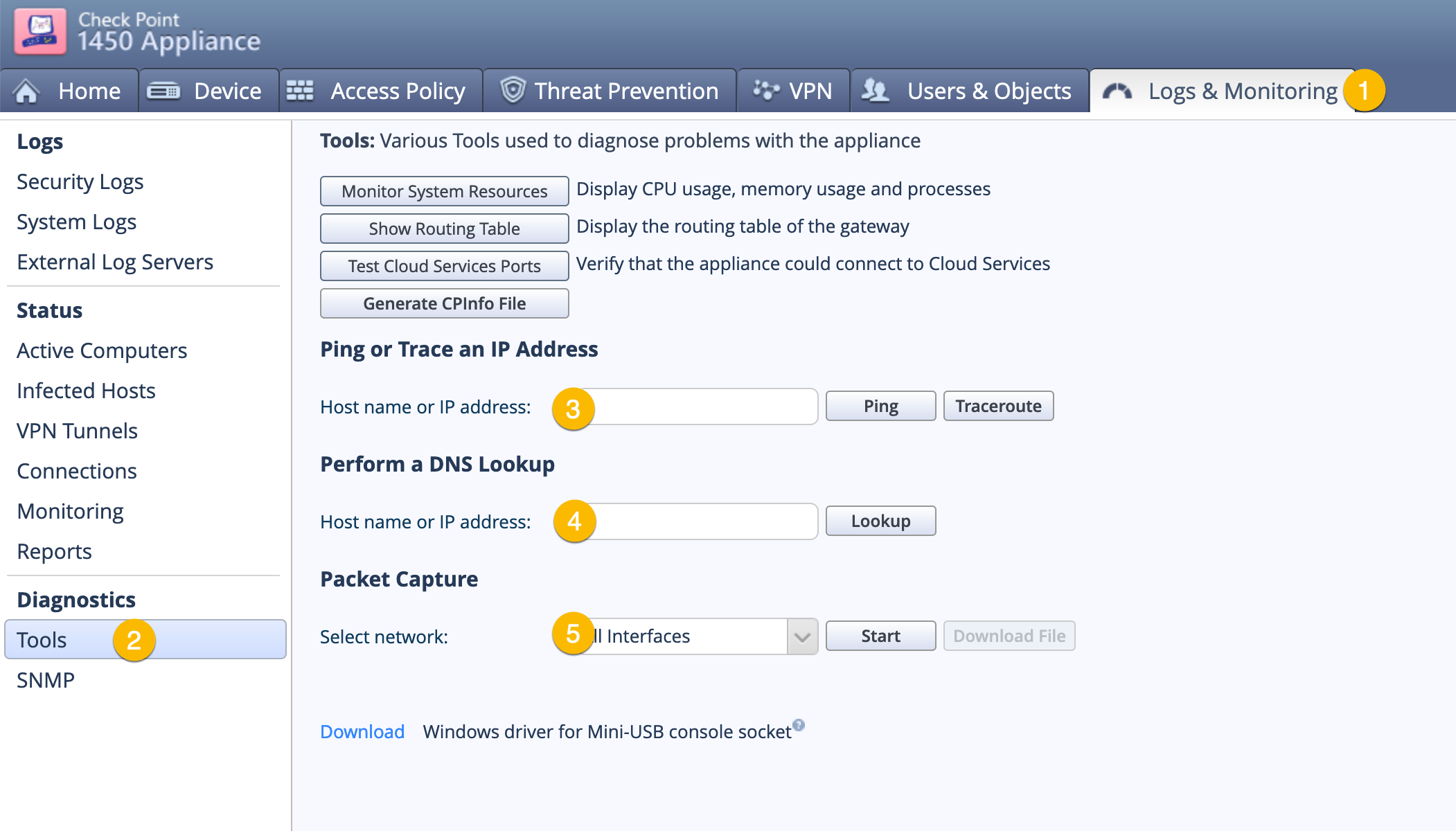
- Choose the
Logs & Monitoringtab on the top. - Choose
Toolson the left column. - Ping / Traceroute to test connectivity.
- DNS lookup to test DNS services.
- Packet Capture.
Configuring the VPN
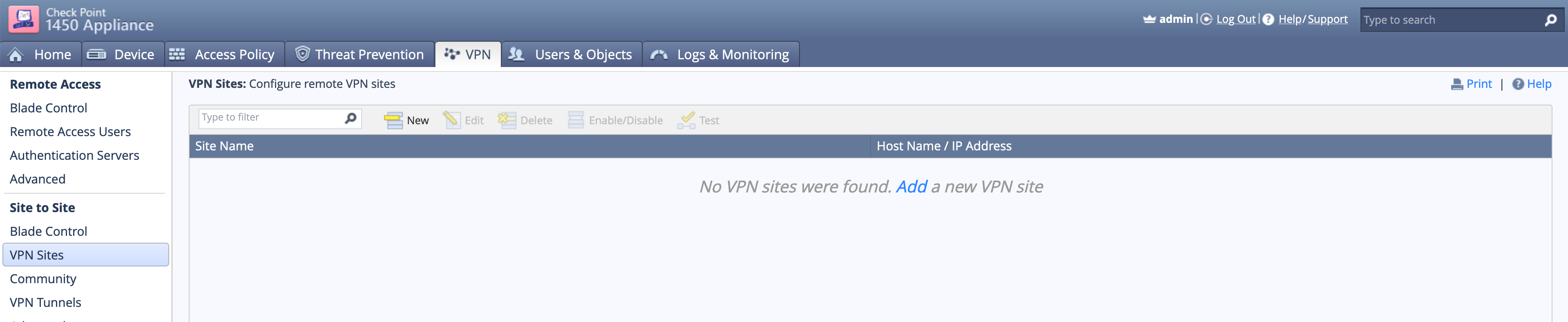
By choosing VPN on the top tab, then VPN Sites you can see I have no VPNs defined. You can click the Add link in the top/middle section of the screen.
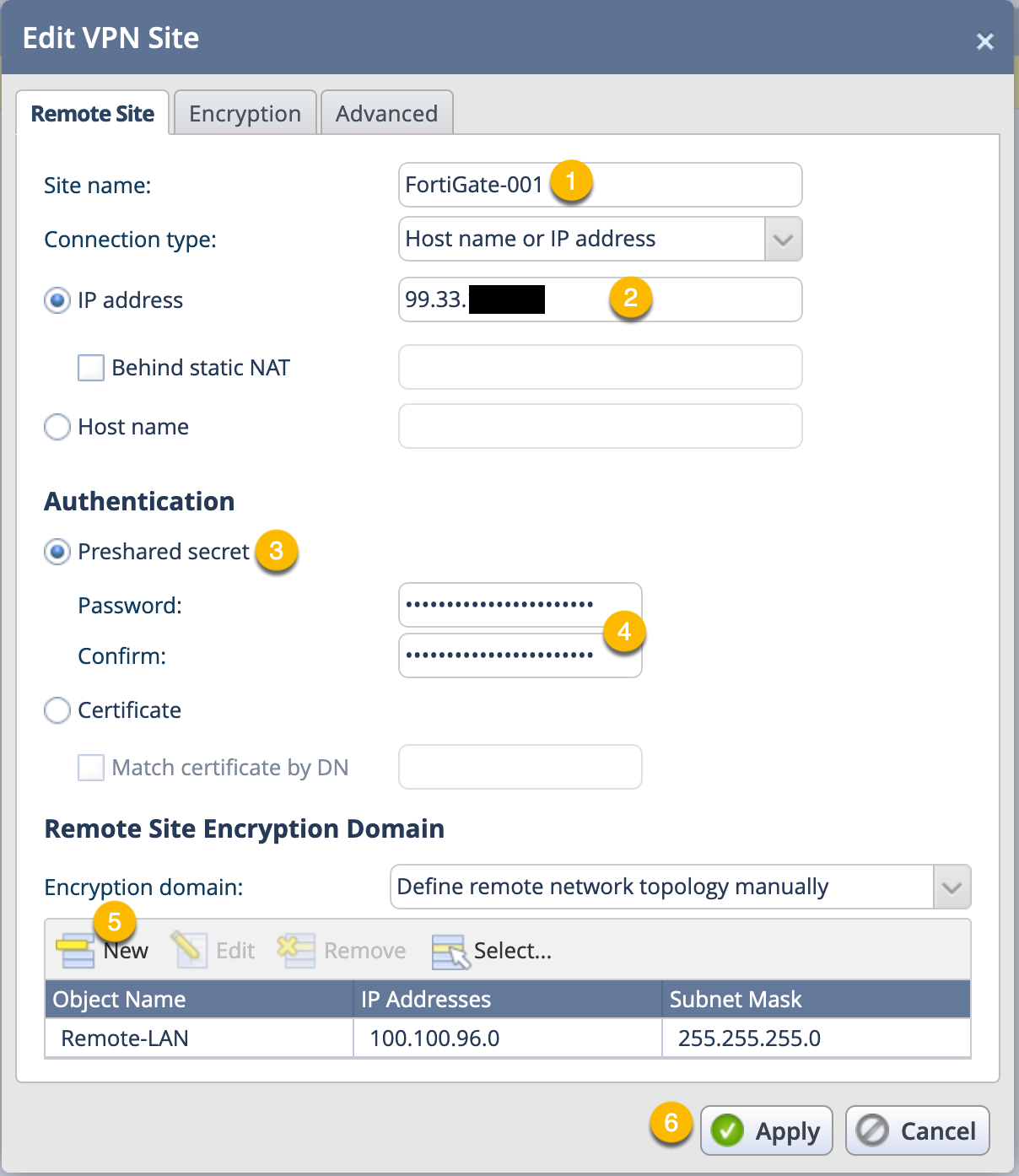
Here we can see the Remote Site configuration screen that shows the main section of the VPN connection.
- Give the VPN a descriptive name.
- Enter the remote peer IP address.
- If you are using PSK or Certificate, Choose accordingly.
- Enter and Validate the PSK (If using PSK).
- Next you will need to configure the Phase II selector for the remote site.
- Finally, click
Apply
Note: This is extremely strange when you are used to using other firewalls on the market. Checkpoint is known for its Encryption Domain that is not necessarily configured in this VPN or in the Communities if using the Centralized Management solution.
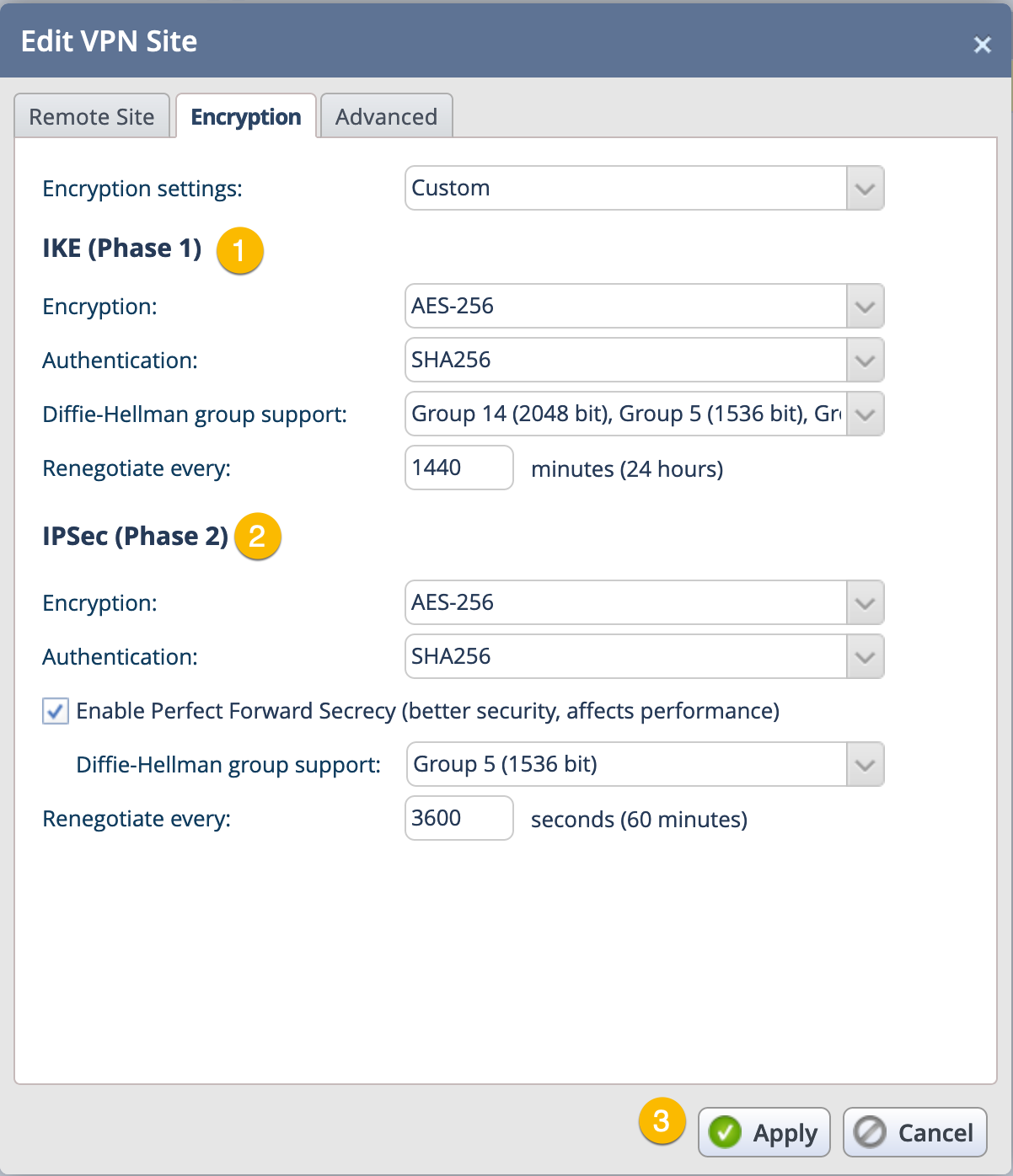
Next we configure the Phase I and Phase II proposals. If you want to add multiple Encryptions schemes as an example, you can choose additional ones and they will be added to the top (see below)
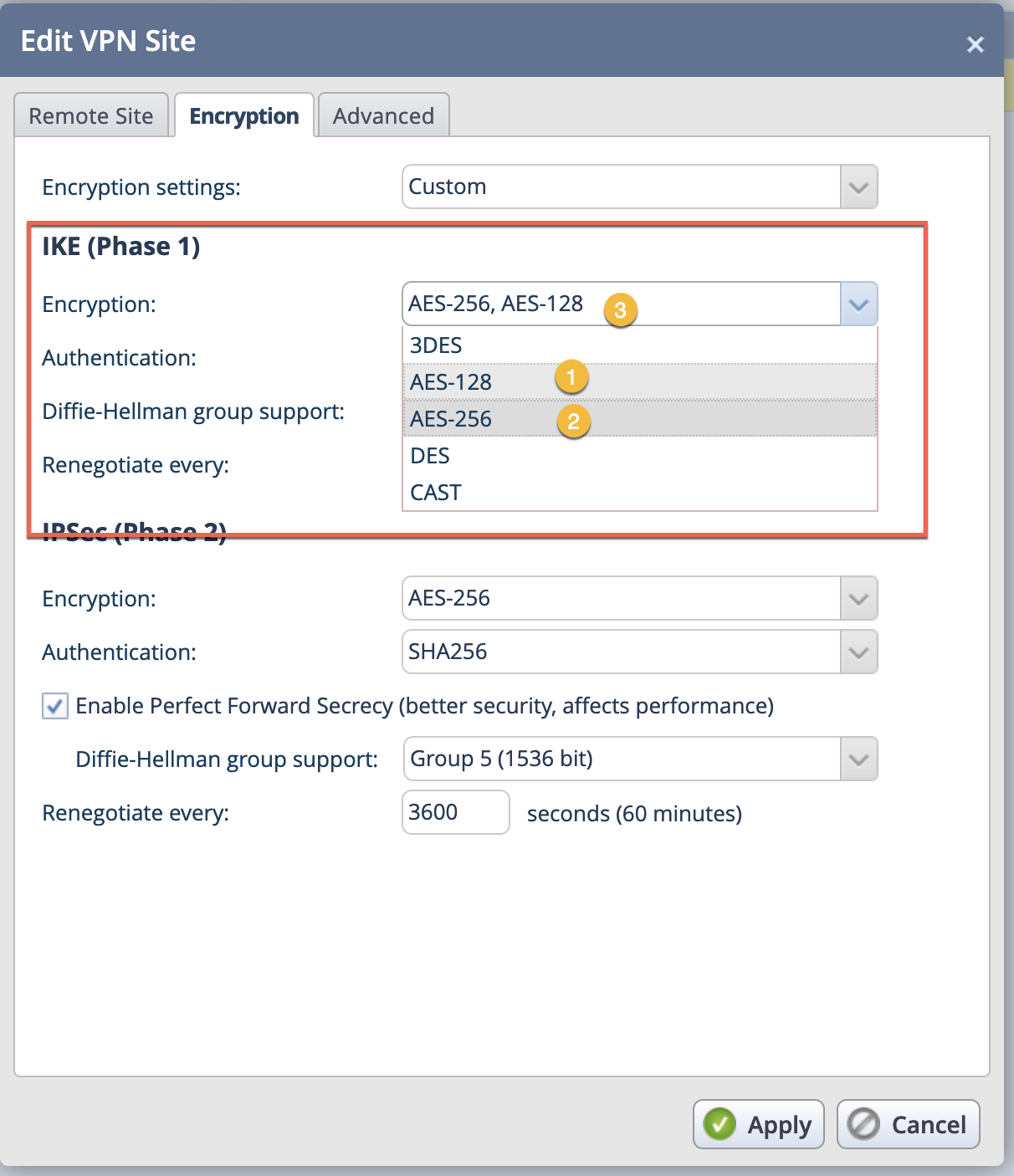
- We chose
AES 128 - We chose
AES 256 - Shows the both selected Encryption Schemes
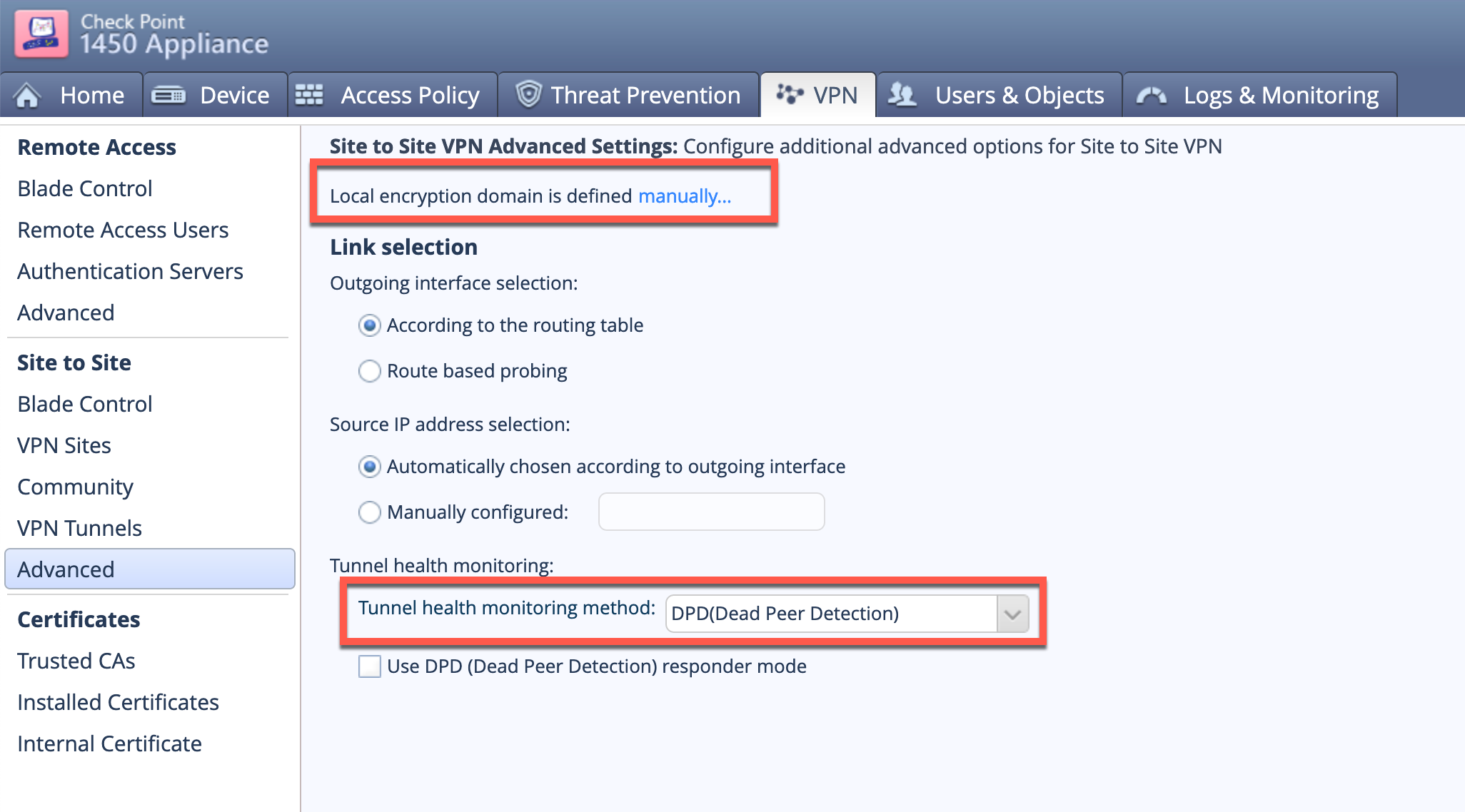
To set up the Phase II selectors for the Local side, go to VPN then Advanced. You will see the first red square that shows the local encryption domain is defined manually which you will need to select.
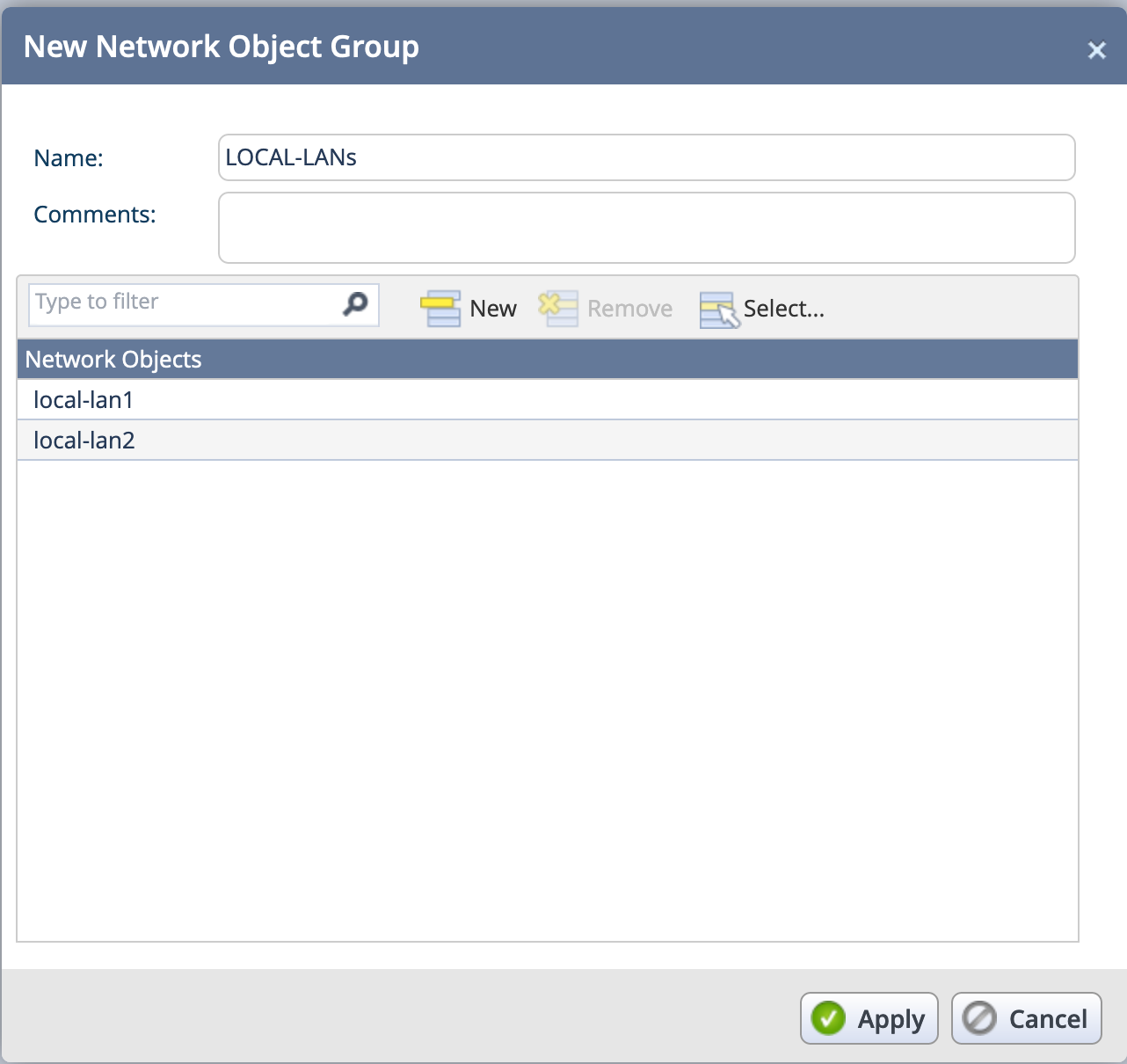
Once selected, you can add separate networks or single IP addresses, however it will NOT let you add a group. This can be problematic depending on the number of networks you have behind the checkpoint.
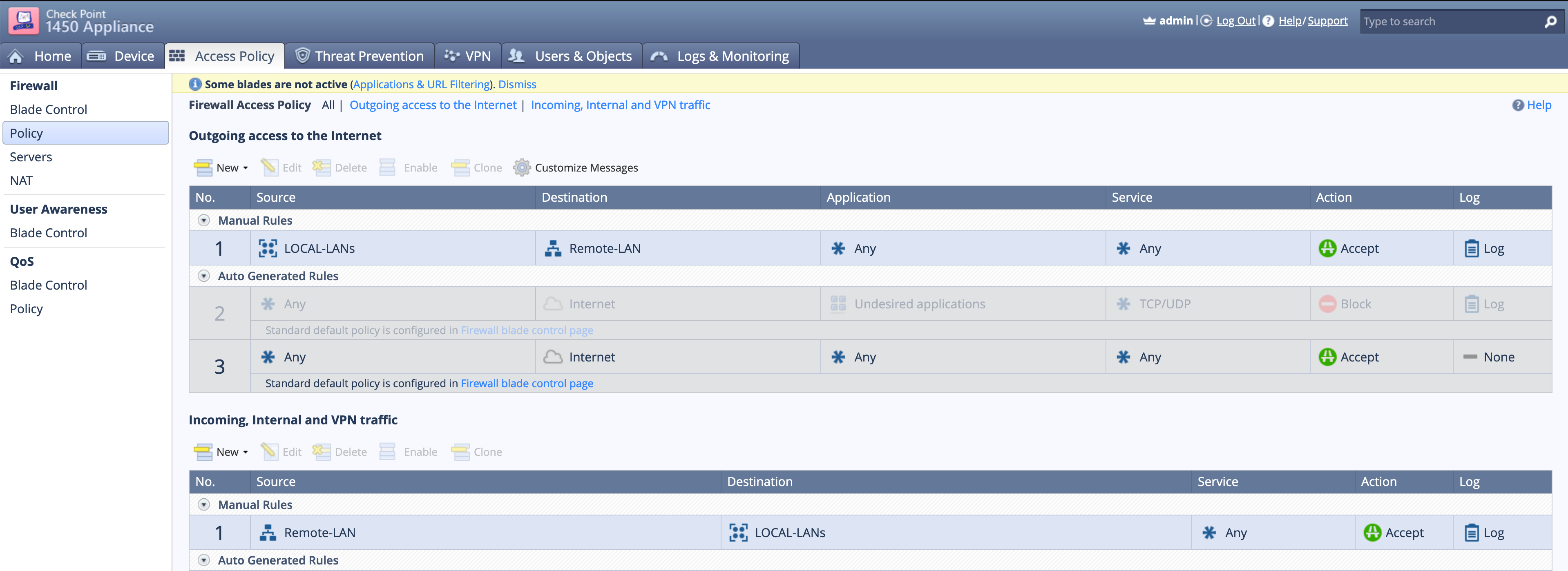
You will need to create rules (in Checkpoint = Policies in FTNT).
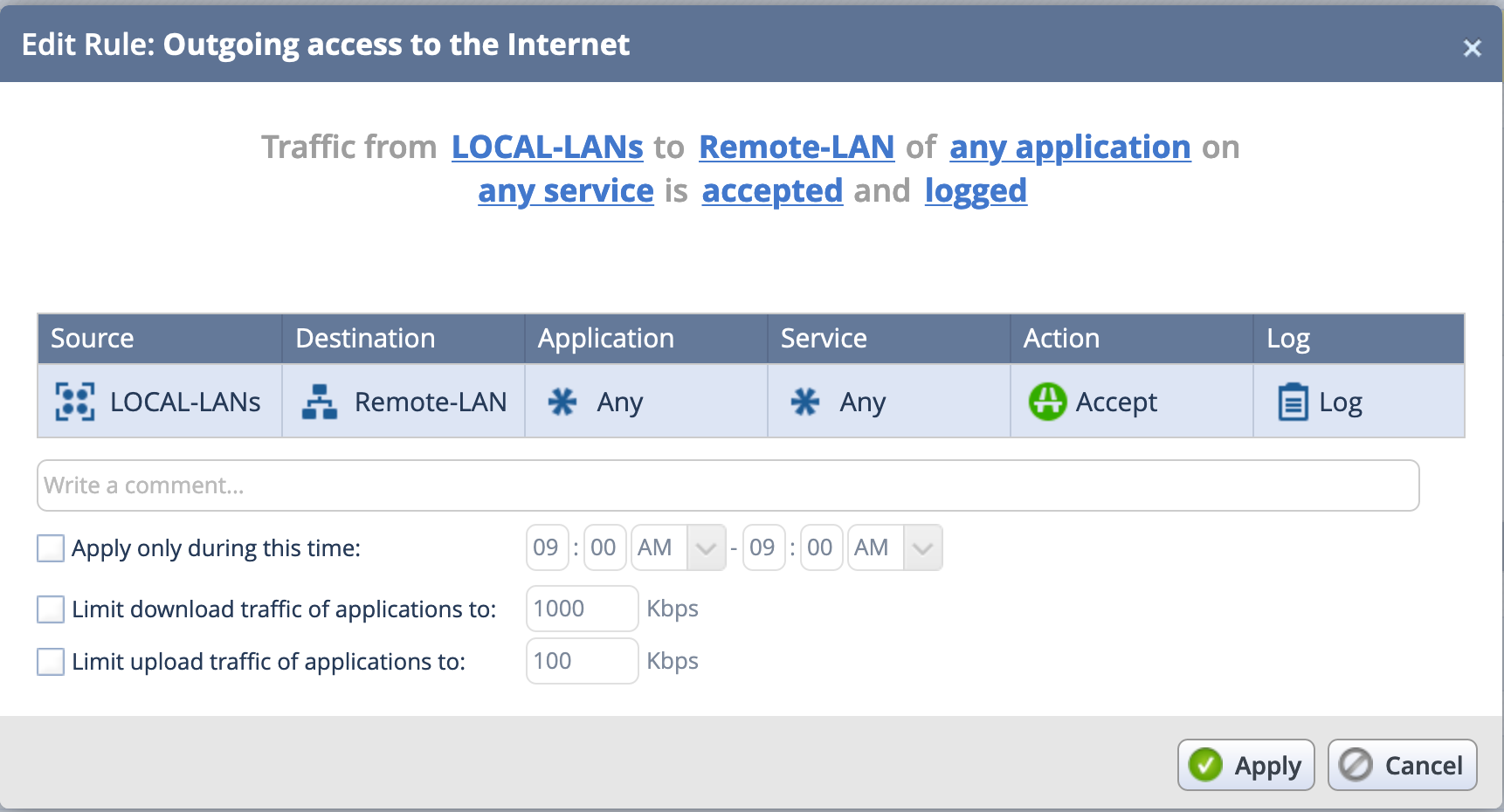
On the top section, you see the Link’d sections in regular English. By selecting each of those sections on the top, you can modify the Source / Destination / Application / Service.
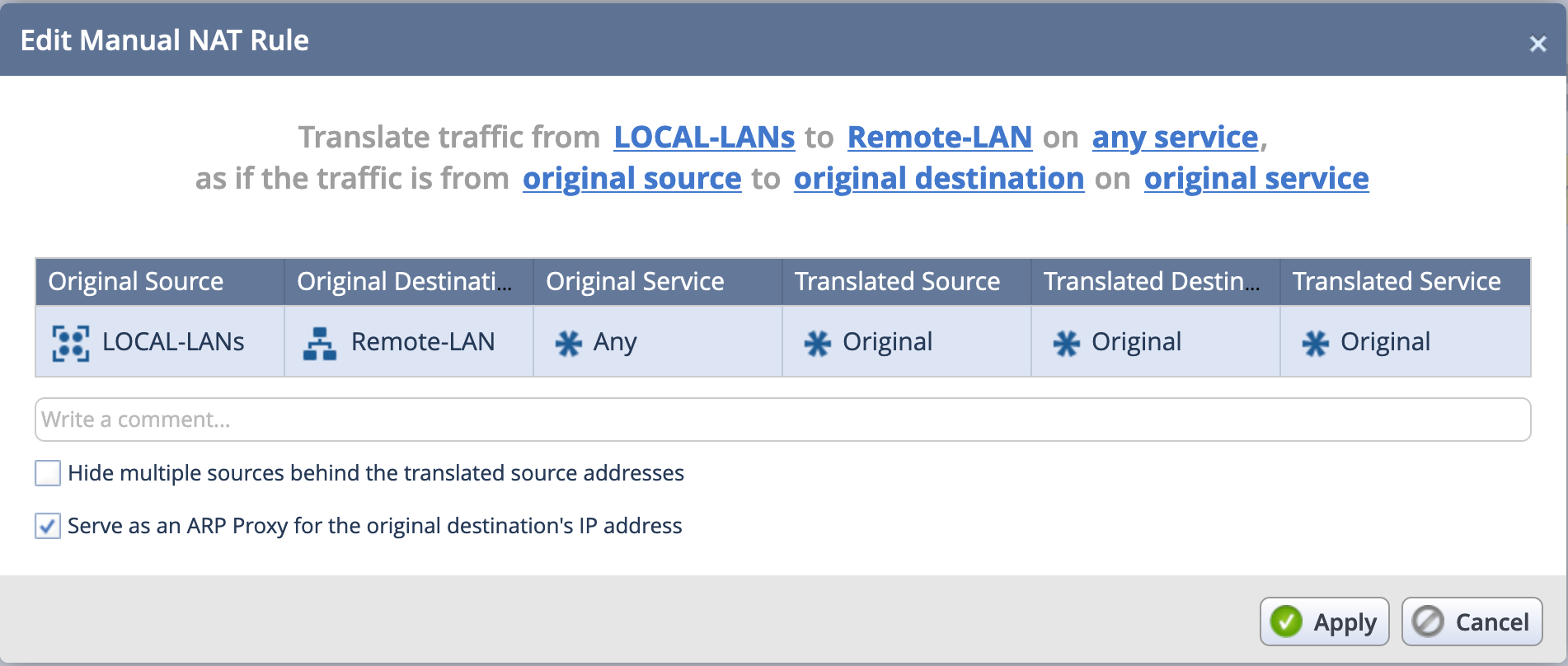
You will also need to create a no-nat rule under Access Policy then NAT. You can create a new rule.
Here we can see that when LOCA-LANs (a group containing local-lan1 and local-lan2)
Note: Yes I know I spelled the group name incorrect. Just lazy to go back and fix it after getting the screenshots. 🙂
Hope this helps
Recent posts
-

-

Had a customer with over 200 static routes on... Full Story
-

This is a work in progress, I will be... Full Story
