At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
July 30, 2024
TCP Encpsulation of ESP Packets for VPN Tunnels
Have you ever worked with international customers that have governments that block IPsec traffic on the standard UDP 500 and 4500 into the country? If you are running FortiGates, you can get around it. Fortinet can encapsulate the ESP protocol packets inside a TCP header as well as IKE packets.
NOTE: This will only work with IKEv2 and will NOT work with ADVPN
First, a refresher on IPSec VPNs
With a traditional IPSec Tunnel you have an initial IKE (Internet Key Exchange) connection which establishes the secure connection to the far end. There are to phases used to build the tunnel:
Phase 1 – In this phase, we establish an ISAKMP (Internet Security Association and Key Managament) session. In this phase, we negotiate authentication, hashing algorithms, encryption schemes, etc. When this is done, these parameters form an SA (Security Association). This Phase 1 is used for tunnel managment. This happens on UDP port 500 and for NAT-T it is UDP 4500.
Phase II – Within this secure tunnel, we then establish the second part of the tunnel which is IKE Phase II refered to as the IPsec Tunnel. In this phase, you identify what networks/IPs will be exchanged and they both must agree.
ESP – Once the tunnel is estabished, you now start to send traffic over ESP or AH. Normally it Is ESP.
This is an oversimplification of the the IPSec VPN process.
Lets get started. You can either use the VPN wizard on the FortiGate or you can create one from scratch on the cli. I like to control my objects and normally use the cli.
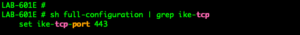
Setting up the ike-tcp-port on the FortiGate. This will only affect the tunnels where you set the transport to TCP , the default is UDP.
Before:
config system settings
"this commands is not present" set ike-tcp-port 443
After:
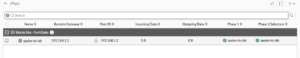
I created the VPN tunnel using the default configuration so that I can test that everything was working as planned. Once it was tested and I could ping across, I changed the transport on both side of the Phase1-interface.
![]()
Once both sides were configured, we can see that the tunnel came up as planned.
Using a standard ipsec debug (see my troubleshooting ipsec post)
![]()
Here we can see that port 443 is being used by iked.
Remember that all other components of the VPN need to be in place (policies, routes, objects, etc)
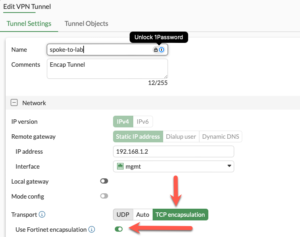
In FortiOS 7.6 the option is available in the UI.
Hope this helps.
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
