There are many options when troubleshooting in FortiGate firewalls. ... Full Story
By Manny Fernandez
February 23, 2021

Quick-Tip : Debugging IPsec VPN on FortiGate Firewalls
Quick-Tips are short how to’s to help you out in day-to-day activities. Usually they are quick easy commands to make your day brighter and help you finish up quicker so you can enjoy family, friends, and libations.
Today we will cover basic FortiGate IPsec Troubleshooting. This is intended as a quick-tip but I have another article that dives a little deeper into the PSK errors etc.
Lets get started.
Filtering the Output
When you have only one or two VPN tunnels, it is pretty easy to troubleshoot without filters. However if you have 10, 20, 100, 1000 VPN tunnels, it is impossible to do so without filtering the output..
diagnose vpn ike log-filter
By running the command above, you will see if you have any filters currently set up. When I started doing VPN way back and there were filters set up, I would be dumbfounded at why I was not receiving any traffic from a particular gateway…. yes it was the filter.
vd: any name: any interface: any IPv4 source: any multiple IPv4 sources: any IPv4 dest: 69.133.211.111 multiple IPv4 dest: any IPv6 source: any multiple IPv6 sources: any IPv6 dest: any multiple IPv6 dest: any source port: any dest port: any
The output shows what you would see if there was some filter set. If you want to reset the filter list and clear the filter, enter the following.
diagnose vpn ike log-filter clear
Now validate again
FW-01 # diagnose vpn ike log-filter vd: any name: any interface: any IPv4 source: any multiple IPv4 sources: any IPv4 dest: any multiple IPv4 dest: any IPv6 source: any multiple IPv6 sources: any IPv6 dest: any multiple IPv6 dest: any source port: any dest port: any
Here is a list of the options that you can set up
list Display the current filter. clear Erase the current filter. name Phase1 name to filter by. src-addr4 IPv4 source address range to filter by. msrc-addr4 multiple IPv4 source address to filter by. dst-addr4 IPv4 destination address range to filter by. mdst-addr4 multiple IPv4 destination address to filter by. src-addr6 IPv6 source address range to filter by. msrc-addr6 multiple IPv6 source address to filter by. dst-addr6 IPv6 destination address range to filter by. mdst-addr6 multiple IPv6 destination addresses to filter by. src-port Source port range to filter by. dst-port Destination port range to filter by. vd Index of virtual domain. -1 matches all. interface Interface that IKE connection is negotiated over. negate Negate the specified filter parameter.
The most used will be src-addr4 or dst-addr4
Listing IPsec VPN Tunnels – Phase I
To get a list of configured VPNs, running the following command:
get vpn ipsec tunnel summary
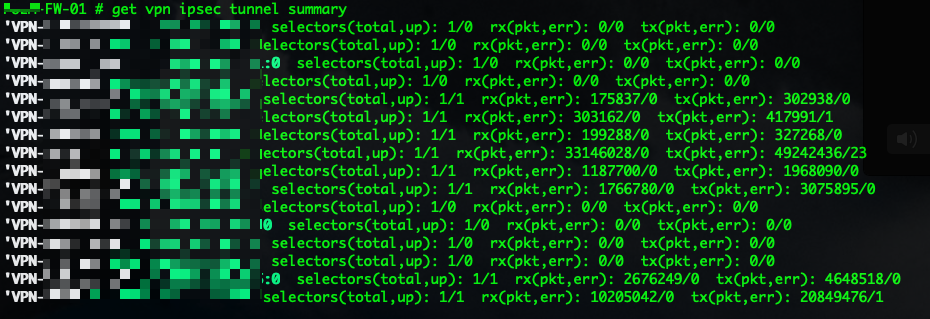
This is a good view to see what is up and passing traffic. Another version of this command is adding a details switch instead of the summary
get vpn ipsec tunnel details
Now if you want to see specifics about a particular VPN
diagnose vpn ike gateway list name %Tunnel-Name%
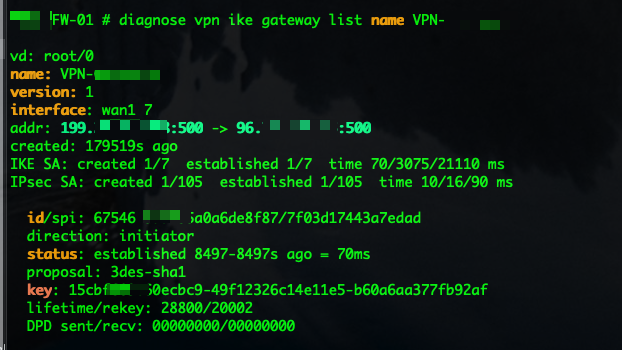
This output tells you that you are the initiator and the proposal is 3DES-SHA1 (not recommended BTW).
Bouncing VPN Tunnels
If you want to bounce a particular VPN Tunnel run the following command
dia vpn ike gateway flush name %Tunnel-Name%
You may not want to bounce the tunnel, but you may want to clear the counters on the tunnel so you could see encrypts and decrypts.
dia vpn tunnel stat flush %Tunnel-Name%
Listing IPsec VPN Tunnels – Phase II
Similar to the Phase-1 command, you can list the Phase-2 information about the tunnel.
get vpn ipsec tunnel name %Tunnel-Name%
Here is a sample output. (IP address or modified)
FW-01 # get vpn ipsec tunnel name VPN-<removed> gateway name: 'VPN-<removed>' type: route-based local-gateway: 199.26.76.158:0 (static) remote-gateway: 69.238.201.1:0 (static) mode: ike-v1 interface: 'wan1' (7) rx packets: 26 bytes: 4294 errors: 0 tx packets: 67 bytes: 6544 errors: 0 dpd: on-demand/negotiated idle: 20000ms retry: 3 count: 0 selectors name: 'VPN-<removed>' auto-negotiate: disable mode: tunnel src: 0:10.1.0.0/255.255.0.0:0 dst: 0:10.3.39.0/255.255.255.0:0 SA lifetime/rekey: 1800/1724 mtu: 1446 tx-esp-seq: 24 replay: enabled qat: 0 inbound spi: a6d747b5 enc: 3des 72b16db608054717e8bf6341661a523ac4ef65596e5e8738 auth: sha1 4b9536321a704b3123f7157ed9e57d08ec17de97 outbound spi: 1434d205 enc: 3des 4d015172a2b1b5be64fbdfee39412962bddabeb938d70669 auth: sha1 1ca00e3bd17bac0dee5e16b9c8abefbc29ef7d7d NPU acceleration: encryption(outbound) decryption(inbound)
Filtering and Debugging
Now lets set a filter for the dst-addr4 and enter the IP address of the peer.
diagnose vpn ike log-filter dst-addr4 %Peer-IP%
Then we are going to start debugging IKE and the -255 is the verbosity (another useful one is -1
dia debug application ike -255
Now we enable the debugging
dia deb en
Here is the output of the VPN coming up
ike 0: comes 69.X.X.X:500->199.X.X.X.X:500,ifindex=7.... ike 0: IKEv1 exchange=Quick id=0c7269600311ac6:1f5d4cdcfb53c0cac6:1f3ae1c6 len=172 ike 0: in 0C726960031187E15D4CDCFB53C0CAC6081ac6E1f3AE1C6000000AC8E8D306E29C4EDDBCE04276E29A2D5811CE12197F00FD3C93C949AECB34209821A740F7E424D31295E5C4AFDD92F3FF6405719A0DFB3B64DDBCF3A372DA8084DAB9779568CA1CA688E9849AB19E5ED140D2BC3B7A2FCAE26ABF03E744F54BE4506F6539B5FCB8E98DF1AFB2F77901FCAE8BB9582F06EB7E223FF10F5443E4ACA7176DBF003F4114EB8B18F27E4839795 ike 0:VPN-<removed>:69271:42226: responder received first quick-mode message ike 0:VPN-<removed>:69271: dec 0C72696003118ac6D1fCFB53C0CAC6081020011F3AE1C6000000AC010000183DE6B255897C695CB8E0B126FF387DAD7C5E223A0A00003C0000000100000001000000300103040166D18CF90000002401030000800400018001000180020E108001000200020004004650008005000205000018D848F846284662DE57AEA36E5CD6E139FDC9D5EF05000010040000000A032700FFFFFF0000000010040000000A010000FFFF000000000000 ike 0:VPN-<removed>:69271:42226: peer proposal is: peer:0:10.3.39.0-10.3.39.255:0, me:0:10.1.0.0-10.1.255.255:0 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: trying ike 0:VPN-<removed>:69271:VPN-<removed>:42226: matched phase2 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: autokey ike 0:VPN-<removed>:69271:VPN-<removed>:42226: my proposal: ike 0:VPN-<removed>:69271:VPN-<removed>:42226: proposal id = 1: ike 0:VPN-<removed>:69271:VPN-<removed>:42226: protocol id = IPSEC_ESP: ike 0:VPN-<removed>:69271:VPN-<removed>:42226: trans_id = ESP_3DES ike 0:VPN-<removed>:69271:VPN-<removed>:42226: encapsulation = ENCAPSULATION_MODE_TUNNEL ike 0:VPN-<removed>:69271:VPN-<removed>:42226: type = AUTH_ALG, val=SHA1 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: incoming proposal: ike 0:VPN-<removed>:69271:VPN-<removed>:42226: proposal id = 1: ike 0:VPN-<removed>:69271:VPN-<removed>:42226: protocol id = IPSEC_ESP: ike 0:VPN-<removed>:69271:VPN-<removed>:42226: trans_id = ESP_3DES ike 0:VPN-<removed>:69271:VPN-<removed>:42226: encapsulation = ENCAPSULATION_MODE_TUNNEL ike 0:VPN-<removed>:69271:VPN-<removed>:42226: type = AUTH_ALG, val=SHA1 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: negotiation result ike 0:VPN-<removed>:69271:VPN-<removed>:42226: proposal id = 1: ike 0:VPN-<removed>:69271:VPN-<removed>:42226: protocol id = IPSEC_ESP: ike 0:VPN-<removed>:69271:VPN-<removed>:42226: trans_id = ESP_3DES ike 0:VPN-<removed>:69271:VPN-<removed>:42226: encapsulation = ENCAPSULATION_MODE_TUNNEL ike 0:VPN-<removed>:69271:VPN-<removed>:42226: type = AUTH_ALG, val=SHA1 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: using tunnel mode. ike 0:VPN-<removed>:69271:VPN-<removed>:42226: add RESPONDER-LIFETIME 1800 seconds ike 0:VPN-<removed>: schedule auto-negotiate ike 0:VPN-<removed>:69271:VPN-<removed>:42226: replay protection enabled ike 0:VPN-<removed>:69271:VPN-<removed>:42226: SA life soft seconds=1782. ike 0:VPN-<removed>:69271:VPN-<removed>:42226: SA life hard seconds=1800. ike 0:VPN-<removed>:69271:VPN-<removed>:42226: IPsec SA selectors #src=1 #dst=1 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: src 0 7 0:10.1.0.0-10.1.255.255:0 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: dst 0 7 0:10.3.39.0-10.3.39.255:0 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: add IPsec SA: SPIs=a6dA53EF704747b9/66d18cf9 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: IPsec SA dec spi a6d7A53EF70447b9 key 24:09DACA53EF7049A478FA71222A596221482192B07B33B38B auth 20:019444C9B5D5023710426C609C8F6A706D2535EE ike 0:VPN-<removed>:69271:VPN-<removed>:42226: IPsec SA enc spi 66d1A53EF7048cf9 key 24:10972ACF16CA53EF704A6C19BCEA95985713CE315BD918 auth 20:1B8A6721B9164501183B7405464F6F098C81B360 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: added IPsec SA: SPIs=aEF704b9/66d18cf9 ike 0:VPN-<removed>:69271:VPN-<removed>:42226: sending SNMP tunnel UP trap
My proposal – This tells you what your firewall is offering as a Phase 1
Incoming proposal – This tells you what the remote gateway is sending you as Phase 1.
Hope this helps.
Recent posts
-

-

Have you ever had an IPS signature that continues... Full Story
-

Use case: Customer has a Split Tunnel Enabled but... Full Story
