At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
April 7, 2019

Using NMAP
On September 1, 1997, Nmap was first released in Phrack magazine Issue 51, Article 11. Since then it has been used by black hats, white hats and everyone in between. It is a super useful tool and I can tell you that being in the role I am in today, I do not use it as much as I used to but even still, I use it at least 5 times a week. In this post, I will try to touch on the basics and maybe some advanced uses for nmap.
Nmap works on the most major operating systems. From their website, this is what they say:
Linux (all distributions)
Microsoft Windows
Mac OS X
FreeBSD, OpenBSD, and NetBSD
Sun Solaris
Amiga, HP-UX, and Other Platforms
I will be running this from a Linux VM and it happens to be running :
[root@observium ~]# nmap -version
Nmap version 6.40 ( http://nmap.org )
Platform: x86_64-redhat-linux-gnu
Compiled with: nmap-liblua-5.2.2 openssl-1.0.1e libpcre-8.32 libpcap-1.5.3 nmap-libdnet-1.12 ipv6
Compiled without:
Available nsock engines: epoll poll select
Target Selection
In this section, you can see the various types of switches you can use to get the results you are looking for from a target selection perspective.
Other options, are the iR which chooses random IPs
nmap -iR 10 10.1.106.0/24
Nmap done: 11 IP addresses (1 host up) scanned in 7.98 seconds
nmap -iR 10 10.1.106.0/24
Nmap done: 16 IP addresses (6 hosts up) scanned in 36.22 seconds
Specifying Ports
Types of Scan
Operating System and Service Detection Type
Saving Results to a File
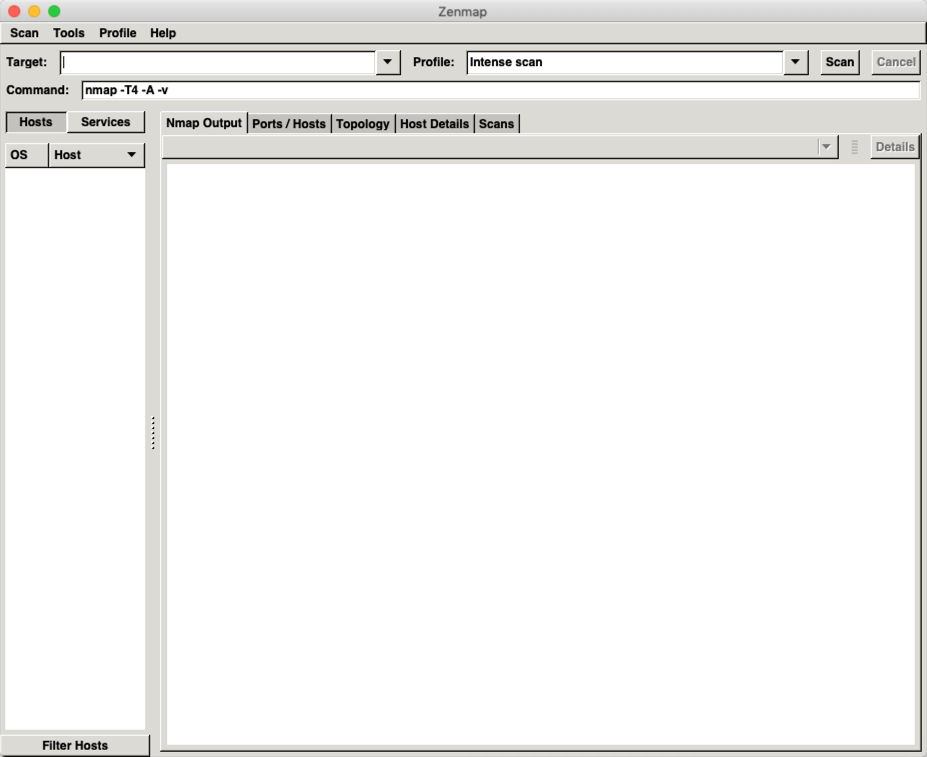
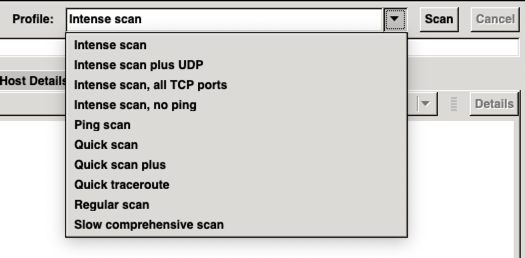
GUI Version
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
