At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
July 29, 2024

Virtual Patching – Local-In management interface
Fortinet has a 1,000+ FortiGuard Labs team on cyber security professionals and because they ship twice as many devices than their closest competitors worldwide, they have billions (yes billions) of actionable alerts per day that are processed through FortiGuard labs. Fortinet has their team of internal pentesters that look for vulnerabilities on their platforms. Not to mention the mature AI backend where they constantly process mailware, and other attack information. Fortinet developed a feature that will help you protect against vulnerabilities to the FortiGate itself. This feature was introduced in 7.4.4 and is available via the CLI, however in 7.6 its available in the GUI.
On 7.4
The first thing you want to do is validate that you have the FMWP database initiated and you are licensed for it. Run the following command diagnose autoupdate versions and look for the FMWP database.
![]()
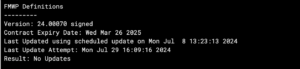
On the above screenshot, you can see that the last update was via an scheduled update.
Once you have validated that you have the database and that it is up to date, you need to ensure that the signatures are enabled. You can do this with the following commands
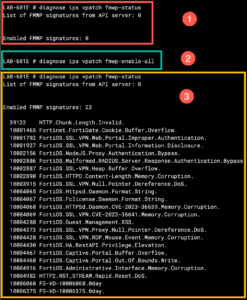
(1) diagnose ips vpatch fmwp-status will tell you how many signatures are enabled.
(2) diagnose ips vpatch fmwp-enable-all will enabled all of the virtual patches.
(3) Once you have them enabled, you can run the diag ips vpatch fmwp-status and validate they are enabled.
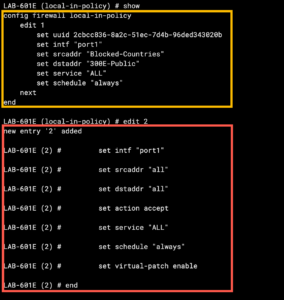
Now lets configur the local-in policy. As you can see in the figure below, I have a local-in policy already created from a previous blog post I did on geo-blocking with the local-in policy. So we will pick the next sequence number which is 2.
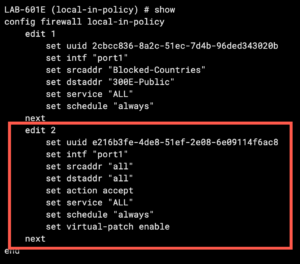
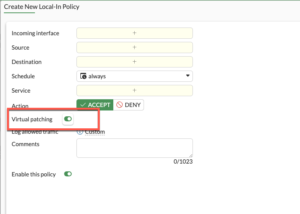
As you can see in the figure highlighted in red, we need to put the interface this applies to, in my case it is port1 You will also want to define the source address with set srcaddr in our case to all. Same with destination, service, and schedule. The most important setting for this post is the set virtual-patch enable which applies the virtual patches to these connections. Once you are done, you need to enter the end command to save it.
You should now see something like this
On 7.6
Special Thanks to Vladislav Ceban for pointing this new feature out to me. Thanks Vlad.
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
