At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
May 14, 2020

VWire with FortiGate Firewalls
Although the FortGate CAN operate in transparent mode, I rarely used/use it. Fortinet introduced VWire which is a layer 2 pair of interfaces. These interfaces do NOT have an IP address assigned to either of them. You cannot add VLANs to virtual wire pairs. However, you can enable wildcard VLANs for a virtual wire pair. This means that all VLAN-tagged traffic can pass through the virtual wire pair if allowed by virtual wire pair firewall policies. Essentially, it is similar to a transparent mode VDOM but better, less complex, and cleaner IMHO.
Use Case:
This is ONE Use Case but the possibilities are endless. Lets say you have 20 locations and they are all connected via an MPLS circuit. The remote sites are a hybrid of Trusted and Hostile sites meaning that they are known to have issues with Shadow IT…. (the ones NOT running FortiNAC, but that is a subject for a different post 😊 ). You want to make sure that you are able to run IPS against that traffic to try to protect the “soft and chewy center” of your datacenter. Lets say that the MPLS terminates at the DC on a carrier managed router. You could disconnect the router from the internal network and plug it into one side of the FortiGate VWire and then plug the other side of the FortiGate VWire to the internal network. Now you can enforce and inspect traffic as it flows from remote sites to internal and internal to remote sites.
Another Use Case, which we describe below, is blocking RDP access from the standard users. Here we will block all RDP sessions destined to the Server VLAN and permit everything else.
Configuring the VWire
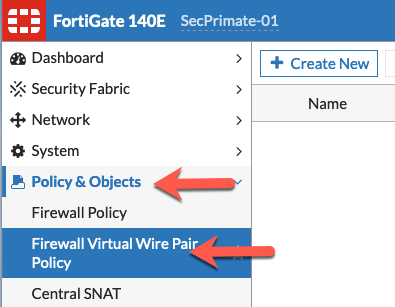
You will need to create the VWire pair by going to Network then Interface
Choose Create New
Then choose Virtul Wire Pair

Give it a Name and choose the Interface Members Note: The interfaces cannot have any configuration on them or be referenced anywhere else in the config.

If you plan on using Wildcard VLANs select it and choose the VLANs. Enter the VLAN (e.g. 1-1024)
![]()
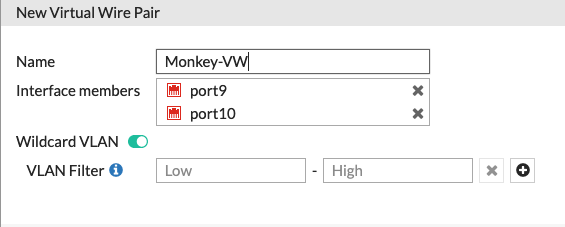
Never mind the selected Wildcard VLAN as it was switched off after I added the interfaces.

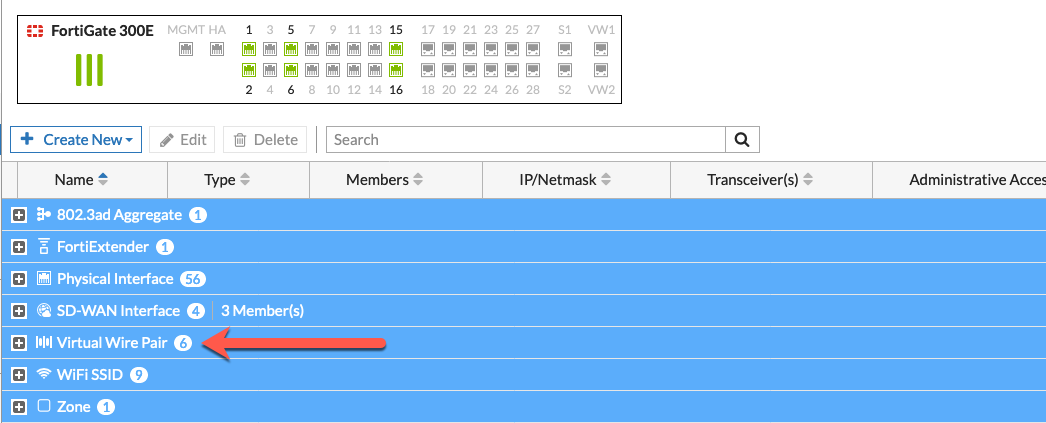
You will now have a section in the Networks | Interfaces portion of the Fortigate that will show the VWire named Monkey-VW and the two corresponding interfaces.
Creating Policies
The VWire policies are located in the same general area as the IPv4 Policies (or the new Policies in 6.4+) but in their own section.
The section is called Firewall Virtual Wire Pair Policy
On the top, right hand side of the screen, you will see the name of the VWire Pair we created in the first section.
Now you can Create New
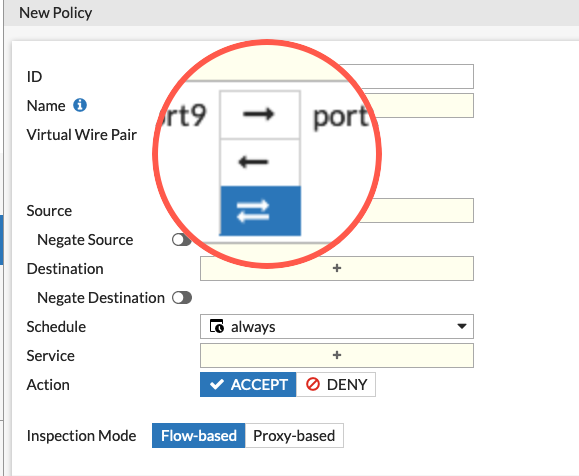
This section is pretty much the same as what you are used to seeing whether you are running Policy-Based or Profile-Based modes, with this major difference; you will see the Virtual Wire Pair instead of incoming interface and outgoing interface.
In this section, you will be able to create either unidirectional or bidirectional policy. In our example, we are going to assume that port9 is connected to common user PCs and port10 is connected to the Server side.
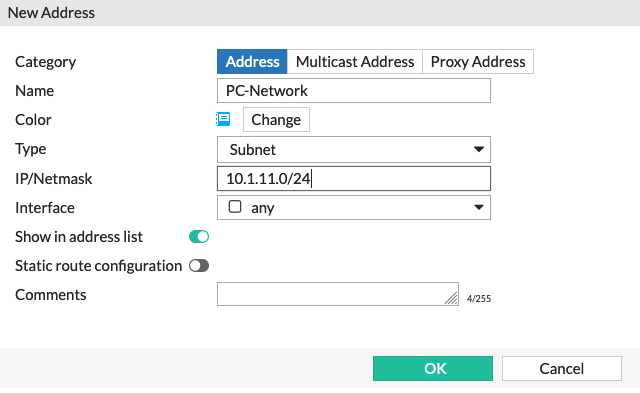
We are going to create an address object for the PC-Network represented by the 10.1.11.0/24 subnet.
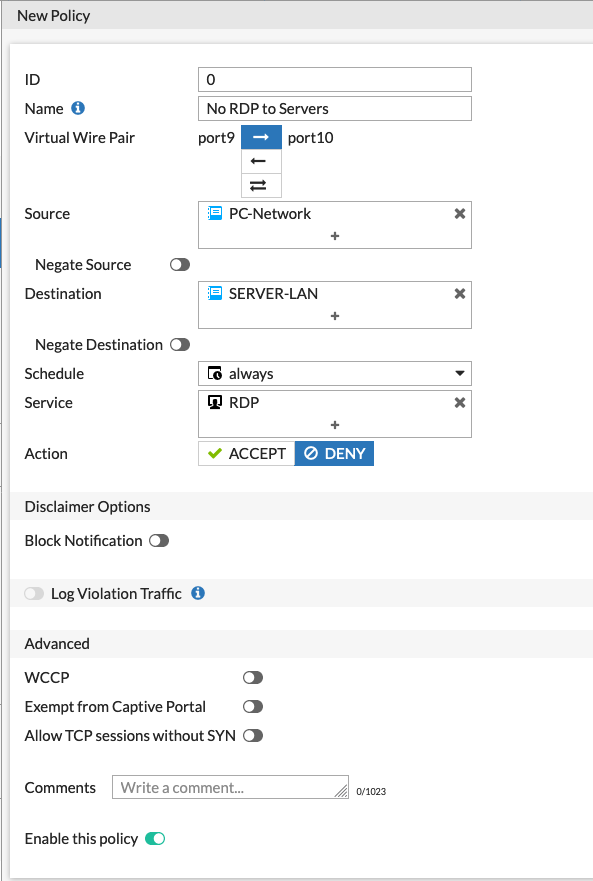
Above we can see the policy I am creating that will deny all the PCs in the PC-Network from using RDP to connect to the SERVER-LAN. Since the policy is a Deny we will not see any security profiles or Applications (In policy-mode).
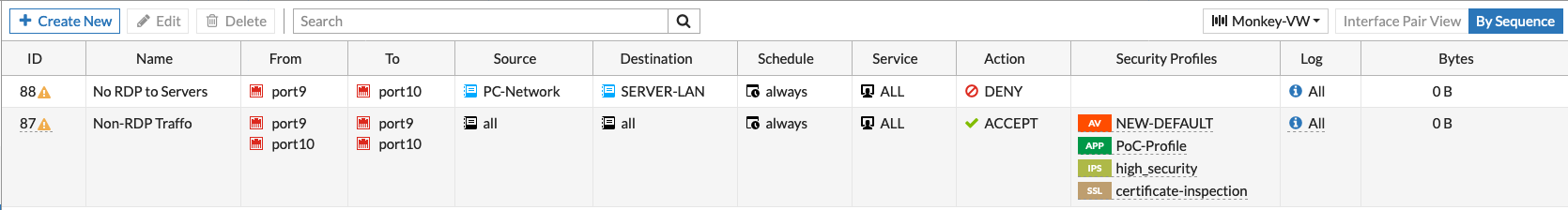
In the screenshot above, we can see that all traffic from the PC-Network (Port9) destined to SERVER-LAN (Port10) that is RDP (TCP 3389) will be denied. All other traffic back and forth will be permitted.
You can have multiple VWire configurations without the need for VDOMs. I use this configuration regularly. It is great to put the FortiGate between existing firewalls and internal switches or perimeter router. I love to identify traffic that “competitors” do not see.
Hope this helps.
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
