This is a work in progress, I will be... Full Story
By Manny Fernandez
January 7, 2020

What Diffie-Hellman (DH) Group Should I Use
There has been a lot around Diffie-Hellman groups and which ones to use. Some think that the bigger the DH group number is, the bigger the key length.
What is Diffie-Hellman
The Diffie-Hellman algorithm was created to address the issue of secure encrypted keys from being attacked over the internet when in transmission, though using the Diffie-Hellman algorithm in distributing symmetric keys securely over the internet.
I have used the “Bob and Alice” examples from text books of when I got started (Don’t Judge). The process works by two peers (Bob and Alice) generating a private and a public key pair each. Alice would send her public key to Bob and Bob would send his public key to Alice. Alice would then use the public key sent from Bob and her own private key to generate a symmetric key using the Diffie-Hellman algorithm. Bob would also take the same process as Alice and in turn produce the exact same symmetric key as Alice, though enabling them to communicate securely over the in-secure internet. Both peers can now encrypt, transmit and decrypt data using their symmetric keys.
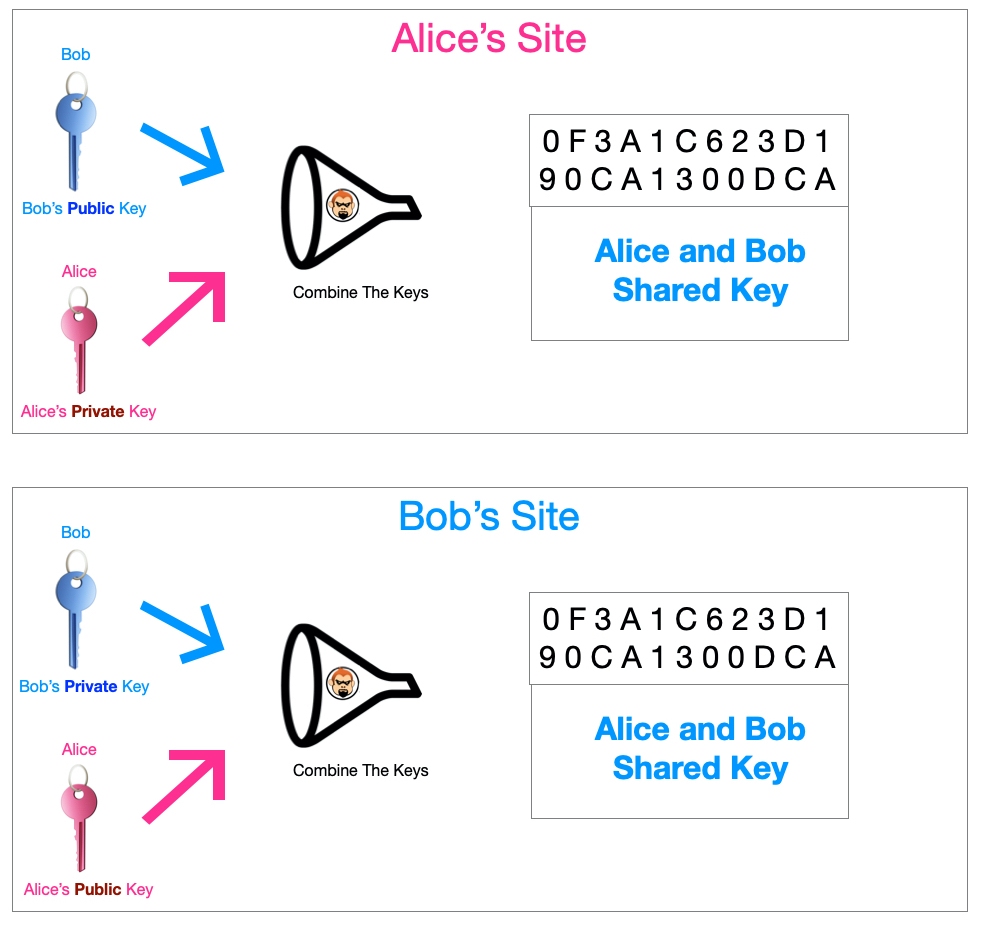
As compute power and more people involved in white-hat, black-hat and grey-hat hacking, some concerns have come to light. Things like Man-in-the-Middle attacks where an attacker could intercept and send another key and use that information to get in-between the communication.
Diffie-Hellman public key cryptography is used by all major VPN gateway’s today, but not all VPN gateways are the same. Some platforms such as Cisco will only support the stronger DH groups only when using IKEv2, which works out well since you should try to use IKEv2 instead of IKEv1.
DES and 3DES does not need as strong a DH group, however DES and 3DES should never be used unless you are under some encryption restriction based on country restriction. AES should use a stronger DH Group. If you are using encryption or authentication algorithms with a 128-bit key, use Diffie-Hellman groups 19, 20. If you are using encryption or authentication algorithms with a 256-bit key or higher, use Diffie-Hellman group 21. RFC 5114 Sec 4 states DH Group 24 strength is about equal to a modular key that is 2048-bits long, that is not strong enough to protect 128 or 256-bit AES, you should stay away from 24.
ecp256 Group 19 (256 bit ECP) ecp384 Group 20 (384 bit ECP) ecp521 Group 21 (521 bit ECP) modp1024 Group 2 (1024 bit modulus) **Avoid** modp1024s160 Group 22 (1024 bit modulus, 160 bit POS) modp1536 Group 5 (1536 bit modulus) **Avoid** modp2048 Group 14 (2048 bit modulus) **Avoid if possible** modp2048s224 Group 23 (2048 bit modulus, 224 bit POS) modp2048s256 Group 24 (2048 bit modulus, 256 bit POS) **Avoid** modp3072 Group 15 (3072 bit modulus) modp4096 Group 16 (4096 bit modulus) modp6144 Group 17 (6144 bit modulus) modp768 Group 1 (768 bit modulus) **Avoid** modp8192 Group 18 (8192 bit modulus)
My Standard
The way I normally set up VPNs is as follows
Phase I
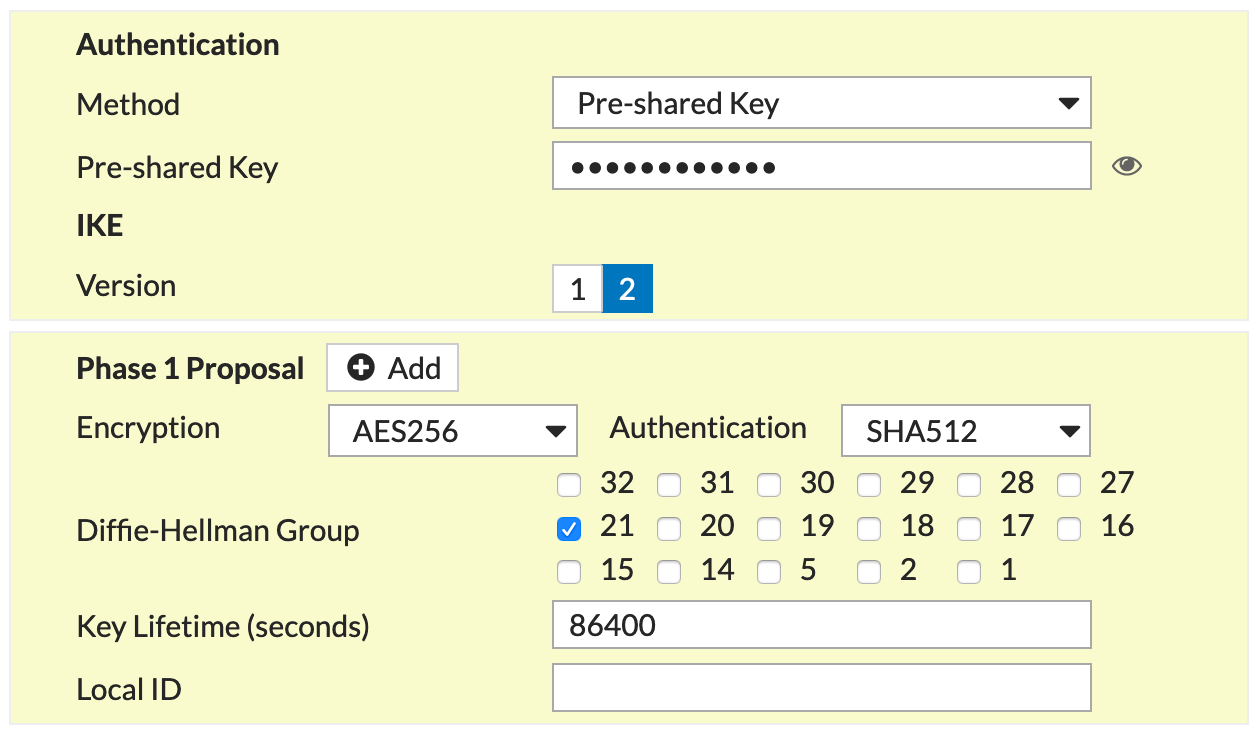
Phase II

Recent posts
-

-

I have been playing with the free version of... Full Story
-

In my day job, I am on a lot... Full Story
