At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
December 31, 2019

Wrong Egress Interface when using VPN
Today I was troubleshooting a problem with a site-to-site, route-based VPN. Here was the skinny.
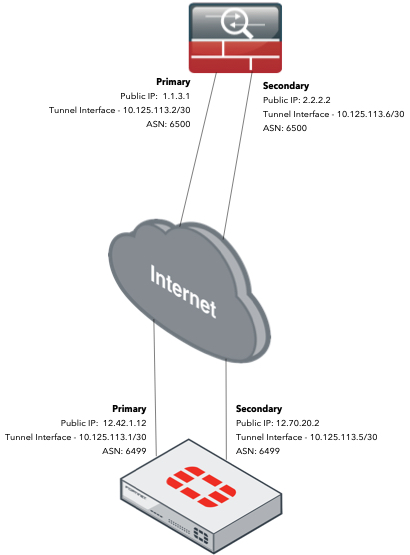
The Setup
I created two separate VPNs and the Phase II selectors were 0.0.0.0/0 for both of them. I went back and forth with the ASA folks on how they wanted to do it. Initially, we were going to do policy-based VPNs (no route-based). In the policy-based we would have created an IP Pool for the 10.125.113.X network. In the route-based, I just NAT’d it using the egress interface’s IP address.
I had BGP configured between the VPNs and I was seeing the initial SYN from the remote side coming in on TCP 179 (BGP’s port). However, I was never seeing my SYN/ACK going back to the remote site.
2019-12-31 17:27:39.528540 VPN-to-ASA-P in 10.125.113.2.19804 -> 10.125.113.1.179: syn 3612720548 2019-12-31 17:27:39.528667 root out 10.125.113.1.179 -> 10.125.113.2.19804: syn 1972465373 ack 3612720549 2019-12-31 17:27:39.528681 root in 10.125.113.1.179 -> 10.125.113.2.19804: syn 1972465373 ack 3612720549 2019-12-31 17:27:39.528708 root out 10.125.113.2.19804 -> 10.125.113.1.179: rst 3612720549 2019-12-31 17:27:39.528715 root in 10.125.113.2.19804 -> 10.125.113.1.179: rst 3612720549
The Problem
If you look at the snippet from above, you can see the SYN packet came from the interface VPN-to-ASA from 10.125.113.1 on port 179. However the second line shows the problem, the return traffic was NOT being routed through the VPN-to-ASA interface. I tried adding a static route to the 10.125.113.2 address and forcing it through the VPN interface…. no dice.
After pulling out the tiny bit of stubble I have left on my head, I decided to remove the IP Pool I mentioned above…. voilá.
2019-12-31 18:40:32.996374 VPN-to-ASA-P out 10.125.113.1.2935 -> 10.125.113.2.179: syn 810114191 2019-12-31 18:40:33.004241 VPN-to-ASA-P in 10.125.113.2.179 -> 10.125.113.1.2935: syn 3736743939 ack 810114192 2019-12-31 18:40:33.004331 VPN-to-ASA-P out 10.125.113.1.2935 -> 10.125.113.2.179: ack 3736743940 2019-12-31 18:40:33.004512 VPN-to-ASA-P out 10.125.113.1.2935 -> 10.125.113.2.179: psh 810114192 ack 3736743940
Now you can see the correct ingress and egress interfaces.
Remember, the IP Pool was just created and was not referenced anywhere.
Customer was running 6.0.2 so I am going to check if it is a bug.
Hope this helps.
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
