At its core, IEEE 802.1X is a network layer... Full Story
By Manny Fernandez
August 31, 2018
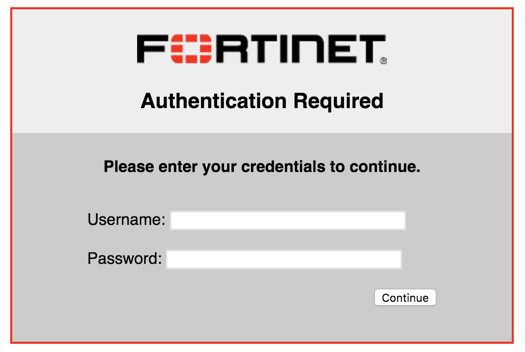
Wired Captive Portal with Fortigate
Use Case: Customer wanted to have their devices that are authenticated to AD, egress to the Internet without needing to authenticate via ‘Captive Portal’ while machines that are NOT members of the domain to require separate authentication using the onboard Captive Portal page (although an external option IS available).
Here is what we did:
1. Configured FSSO (Fortinet Sigle Sign On) to tie into the Active Directory.
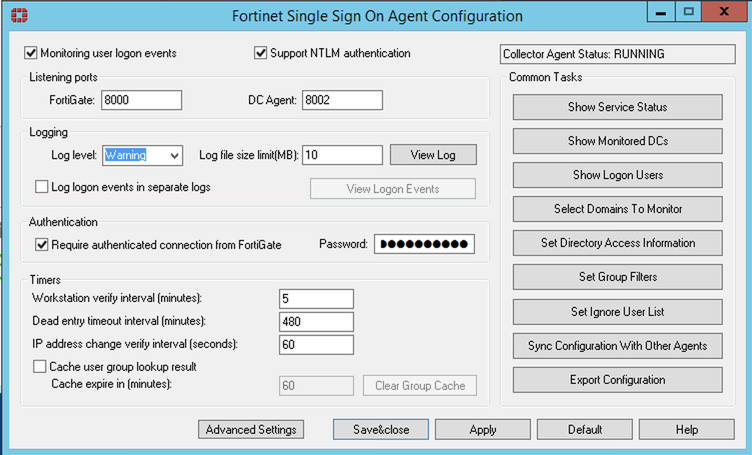
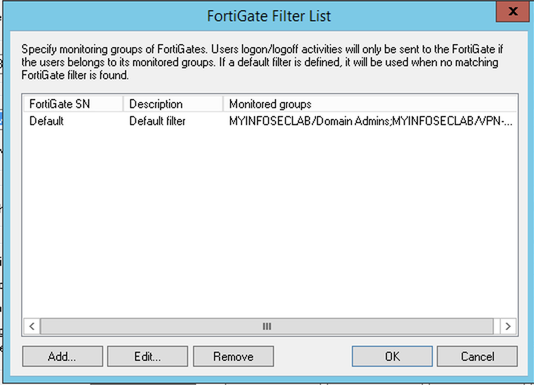
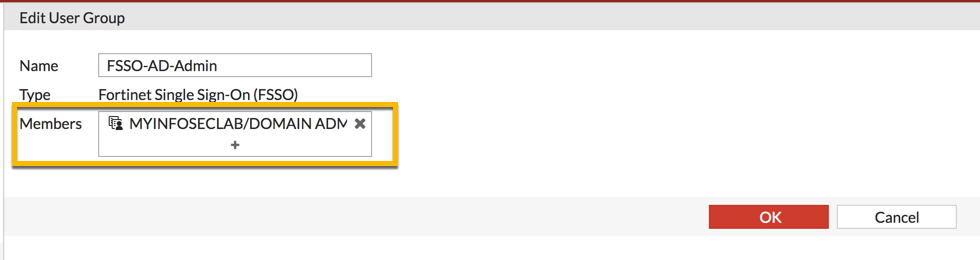
2. Added the two AD Security Groups that I wanted to have participate in the auth.
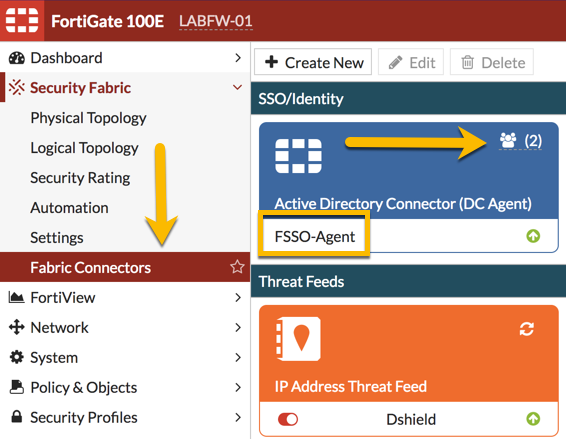
3. Added the FSSO to the Fortigate and added a user group based on FSSO we defined earlier on.
4. Configured ‘Captive Portal’ on the interface we wanted to use.
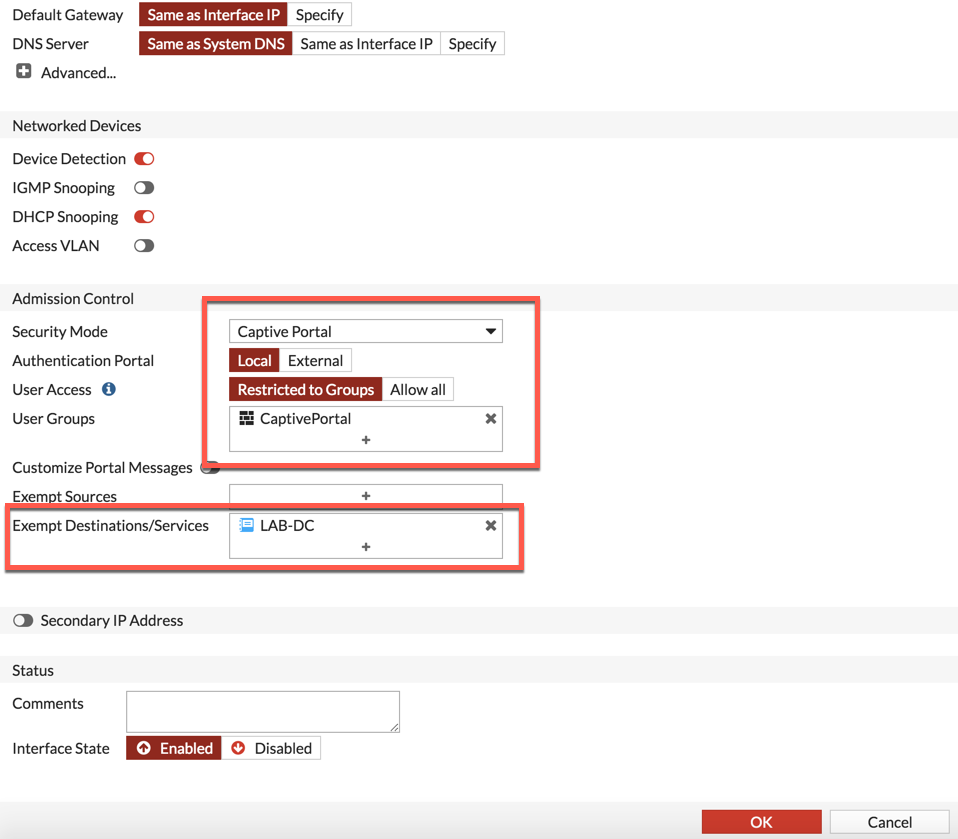
5. Selected what we wanted to exempt and what groups were required to use the captive portal on the interface.
In my environment, the Windows machine was sitting across a L3 boundary so I needed to exclude traffic going to it from the ‘Captive Portal’
6. Created a policy with the source interface as ‘captiveportal’ and the destination ‘WAN1 and WAN2’ with source being ‘all’ and the user group of the FSSO (step 3).
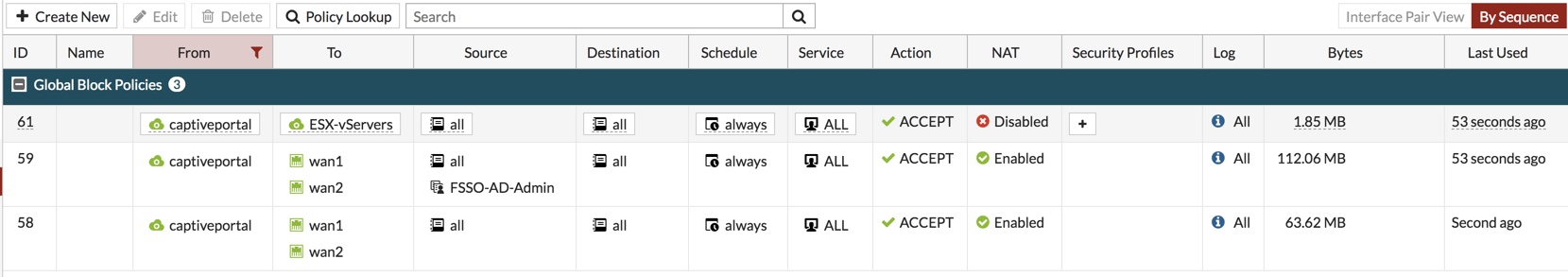
7. Then underneath that policy, I added another policy that permits all all.
8. Then tested.
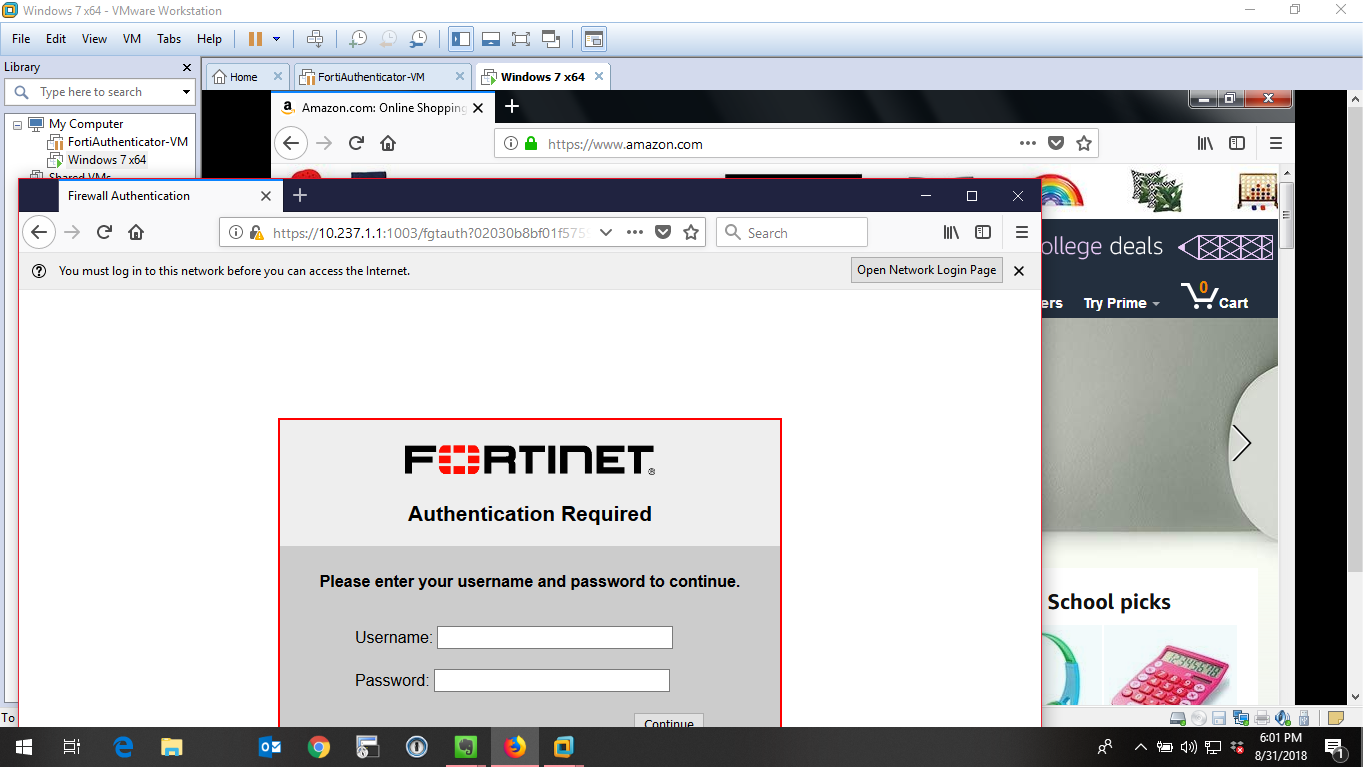
In the screenshot, you can see the left screen is the PC that is NOT part of the domain, the one in the background is the Windows machine that is part of the domain. The one in the back is directly connected while the one in the front is asking for the creds.
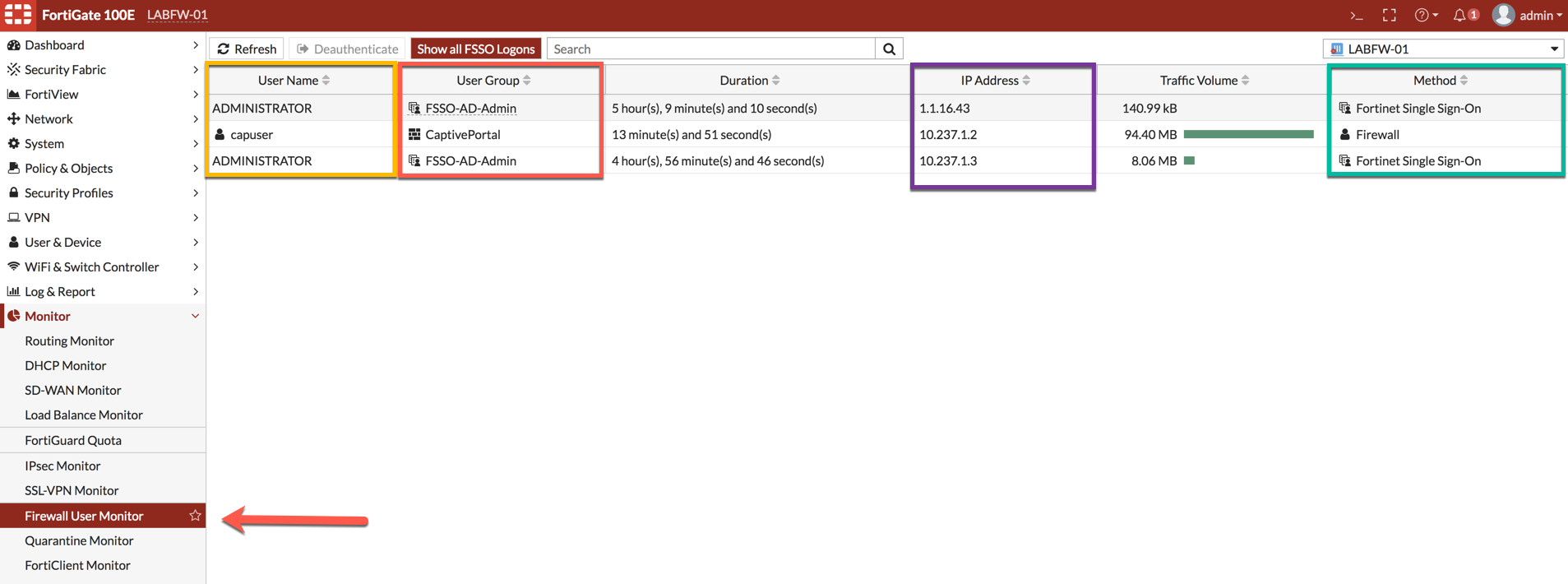
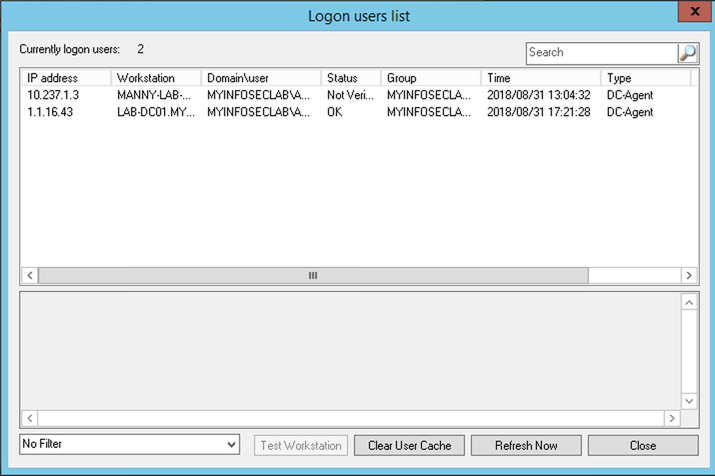
Here you can see the users logged in, the method they used to log in, and their correspoinding IP address.
Recent posts
-

-

In case you did not see the previous FortiNAC... Full Story
-

This is our 5th session where we are going... Full Story
-

Now that we have Wireshark installed and somewhat configured,... Full Story
-

The Philosophy of Packet Analysis Troubleshooting isn't about looking... Full Story
