There are many options when troubleshooting in FortiGate firewalls. ... Full Story
By Manny Fernandez
June 29, 2016

Context-Based Access Control (CBAC)
CBAC is barely used today. It has long been substituted with Zone-Based Firewall (Discussed later on a different post) and even ASA firewalls in most cases. However for the CCIE v4, you will need to know how to configure it and troubleshoot it.
What is CBAC?
CBAC is a combination of a couple of older Cisco technologies. It is a combination of Reflexive Access-Lists and TCP intercept.
Reflexive Access-Lists: In a nutshell, the Reflexive ACLs will automatically punch holes in your ACL (the opposite way) to permit traffic that was originated from inside your network. Similar to what you see today with the ‘stateful’ but not quite the same.
TCP Intercept: TCP Intercepts protect the router from DoS attacks specifically with embryonic sessions. There are two modes for TCP Intercept; Intercept Mode and Watch mode.
Intercept Mode: – In Intercept mode, the router will intercept the 3-way handshake requests and essentially proxy the connection to the inside hosts. This is not recommended because under a DoS, your router would be the target and could bring down more devices at once.
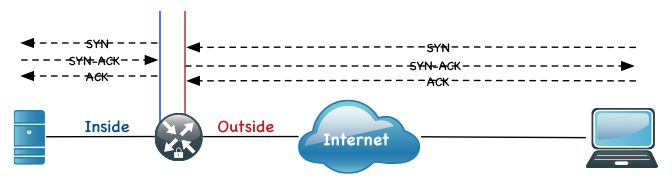
The following diagram shows the 3-Way handshake terminating on the router’s ‘outside’ interface.
Watch Mode: When using ‘watch mode’ the router will watch connections and based on a ‘low:high’ ratio (configurable) will reset the connections if the embryonic sessions meet that criteria.
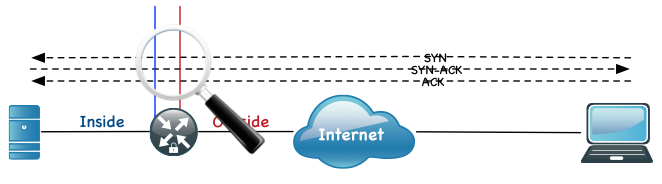
In the Watch diagram, we see the 3-way handshake is terminating directly on the server. The TCP Intercept will continue to monitor connections and based on a low:high ratio, will start to reset embryonic connections.
ip tcp intercept mode {intercept | watch}
Steps required for configuring CBAC
- Name the inspection (e.g. CBAC_INSPECT)
- Choose what protocols you want to inspect (e.g. TCP/UDP/ICMP or any specific such as HTTP, DNS etc).
- Configure ‘ip inspect’ on the interface you will be inspecting.
- Assign an access-list on the egress point.
—————————————————————————
Types of Access-Lists
Standard – Is used to define source IPs such as in a route-map ACL where you choose to redistribute based on an ACL. There is no concept of ‘permit tcp|udp|icmp|protocol’ in ‘standard’ ACLs. Standard ACLs use the following numbers or the identifier of ‘standard’: 1-99 and 1300-1999
Extended – Is used to match source, destination &/or protocol. This is much more flexible than the standard and as such, is normally used more often than ‘standard’. Extended ACLs use the following numbers or the identifier of ‘extended’: 100-199 and 2000-2699.
Time-Based – Time-Based ACLs allow you to defin a ‘time-range’ which is applied to the end of the ACL to delineate that it is bound by time (periodic or absolute); periodic allows you to create a range of times whereas absolute is based on a hard date/time.
For Time-Based, we first define a range or absolute time:
time-range permittelenet periodic daily 8:00 to 16:00
or
time-range permittelnet
absolute start 00:00 10 September 2015
We then add that to the end of an ACL ‘access-list 100 permit tcp any any eq 23 time-range permit_telnet‘
NOTE: (Implicit Deny) One thing to note, when you create an access-list and there are no ACE (access control entries), the implicit deny is ignored. Once you add an ACE to the ACL, then the implicit deny is in play. This was done to protect engineers becasue you could lock yourself out of the device. Best practice is to remove the ACL from an interface before making changes.
Example 1
In this example, we will set up a a webserver sitting on the inside network (not recommended is real-world), permit some traffic and protect the webserver.
ip inspect name CBAC_INSPECT tcp
ip inspect name CBAC_INSPECT udp
ip inspect name CBAC_INSPECT icmp
You can inspect specific “applications” (this is not application aware, it just tells it what ports to look at) within the specific protocols and not have them inspect ALL. For instance you can do the following:
ip inspect name CBAC_INSPECT telenet
A good command to use to identify what port-mappings exists to be used in the above example is:
show ip port-map ## Can also use the modifier ‘|’ to grep a particular.
#Sample output
R1(config)#do sh ip port-map
Default mapping: snmp udp port 161 system defined
Default mapping: echo tcp port 7 system defined
Default mapping: echo udp port 7 system defined
Default mapping: telnet tcp port 23 system defined
Default mapping: wins tcp port 1512 system defined
Default mapping: n2h2server tcp port 9285 system defined
To add a custom entry:
ip port-map http port 8080
## In the above example, we are adding 8080 to the HTTP port mapping. So now, if we do an ‘inspect http’ the following will be selected:
Default mapping: http tcp port 80 system defined
Default mapping: http tcp port 8080 user defined
Default mapping: https tcp port 443 system defined
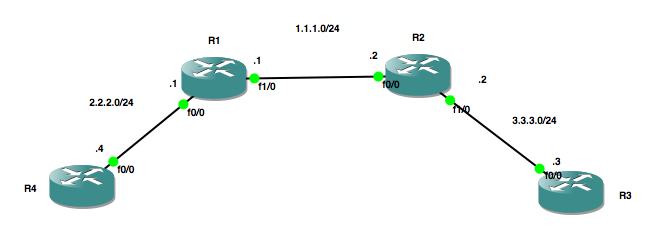
Router 1 Configuration
R1#sh run | s interface|ip inspect
ip inspect name CBAC_INSPECT tcp
ip inspect name CBAC_INSPECT udp
ip inspect name CBAC_INSPECT icmp
interface FastEthernet0/0
description !!!! Connected to R4 interface f0/0 !!!
ip address 2.2.2.1 255.255.255.0
duplex half
interface FastEthernet1/0
description !!!! Connected to R2 interface f0/0 !!!
ip address 1.1.1.1 255.255.255.0
duplex auto
speed autoip route 3.3.3.0 255.255.255.0 1.1.1.2 name “Router 3 Segment”
Router 2 Configuration
R2#sh run | s interface
interface FastEthernet0/0
description !!! Connected to R1 interface f1/0 !!!
ip address 1.1.1.2 255.255.255.0
duplex half
interface FastEthernet1/0
ip address 3.3.3.2 255.255.255.0
duplex auto
speed autoip route 2.2.2.0 255.255.255.0 1.1.1.1 name “Router 4 Segment”
Router 3 Configuration
R3#sh run | s interface
interface FastEthernet0/0
ip address 3.3.3.3 255.255.255.0
duplex halfip route 0.0.0.0 0.0.0.0 3.3.3.2
Router 4 Configuration
R4#sh run | s interface
interface FastEthernet0/0
ip address 2.2.2.4 255.255.255.0
duplex halfip route 0.0.0.0 0.0.0.0 2.2.2.1
I have enabled HTTP on Router 4 and it will server as a webserver as well as a telnet server for this lab.
We are going to apply the inspect to the inbound interface of R1 coming from R4.
interface FastEthernet0/0
description !!!! Connected to R4 interface f0/0 !!!
ip address 2.2.2.1 255.255.255.0
ip inspect CBAC_INSPECT in
duplex half
We will now create the ACL on R1 and apply it in the inbound direction on interface f1/0 (coming from R2 and R3),
— R1 —
ip access-list extended INBOUND_ACL
permit icmp any any
deny ip any anyint f1/0
ip access-group INBOUND_ACL in
— R2 —
#Pinging router 1 from r2 we have success.
ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 60/64/68 ms
#Telneting router 1 from r2 fails.
R2#1.1.1.1
Trying 1.1.1.1 …
% Destination unreachable; gateway or host down
R2#
#On r1, we see the ping packets on the permit, and we see
#the hit count on the deny increasing because of the telnet #attempt
R1#sh access-lists
Extended IP access list INBOUND_ACL
10 permit icmp any any (15 matches)
20 deny ip any any (3 matches)
The reflexcive access-list portion without the inspect, will show you the ACE’s being created in the inbound ACL however in CBAC, you will need to turn some debugging on to see the those entries. You can choose the ‘object-creation, object-deletion or both.
debug ip inspect object-creation | object-deletion
The following is an output of the debug for the object creation when telneting from r4 to r3:
*Sep 13 11:31:14.691: CBAC* OBJ_CREATE: Pak 63A65D14 sis 642764AC initiator_addr (2.2.2.4:44648) responder_addr (3.3.3.3:23)
initiator_alt_addr (2.2.2.4:44648) responder_alt_addr (3.3.3.3:23)
*Sep 13 11:31:14.691: CBAC OBJ-CREATE: sid 6416EF58 acl INBOUND_ACL Prot: tcp
*Sep 13 11:31:14.691: Src 3.3.3.3 Port [23:23]
*Sep 13 11:31:14.691: Dst 2.2.2.4 Port [44648:44648]
*Sep 13 11:31:14.695: CBAC OBJ_CREATE: create host entry 64076240 addr 3.3.3.3 bucket 0 (vrf 0:0)
We can see that there was a TCP 23 ACE added to the ‘INBOUND_ACL’ ACL permitting traffic from 3.3.3.3 (R3) sourcing from port 23, to come back to 2.2.2.4 (R4) on its source port of 44648. I enabled both creation and deletion. The following shows the deletion:
*Sep 13 11:32:56.931: CBAC OBJ_DELETE: delete sis 642764AC
*Sep 13 11:32:56.931: CBAC OBJ-DELETE: sid 6416EF58 on acl INBOUND_ACL Prot: tcp
*Sep 13 11:32:56.931: Src 3.3.3.3 Port [23:23]
*Sep 13 11:32:56.931: Dst 2.2.2.4 Port [44648:44648]
Additionally, you can use the command
R1#sh ip inspect sessions detail
Established Sessions
Session 642764AC (2.2.2.4:21124)=>(3.3.3.3:23) tcp SIS_OPEN
Created 00:00:18, Last heard 00:00:14
Bytes sent (initiator:responder) [31:71]
In SID 3.3.3.3[23:23]=>2.2.2.4[21124:21124] on ACL INBOUND_ACL (12 matches)
One thing to remember is that you need to be congnizant of the control plane and its needs. for instance, if you are using a routing protocol (EIGRP, OSPF, RIP, BGP) you need to make sure that the particular protocols are permited through the ACL appied to the ‘outside’ interface.
To log creation of objects to syslog, you need to enable audit trail on both the inspect and globally.
ip inspect audit trail
ip inspect name CBAC_INSPECT tcp audit-trail on
Coming soon, I will do a blog post on the CBAC with HA. Stay Tuned.
Recent posts
-

-

Have you ever had an IPS signature that continues... Full Story
-

Use case: Customer has a Split Tunnel Enabled but... Full Story
