In FortiOS 7.4, Fortinet enhanced the ability to do... Full Story
By Manny Fernandez
September 7, 2019

How we used Fortinet to host a CTF (Capture the Flag)
Every years, the South Florida ISSA puts on a Capture the Flag / Chili Cook Off event. For the past few years, I have been involved in setting up and managing the connectivity for the event. I decided to write up a blog post showing the infrastructure. I am not putting any specifics about the games themselves.
Here is what we ended up using:
- Fortigate 1500D
- FortiAnalyzer 400F
- FortiSwitch 448D-FPoE
- FortiSwitch 124D-PoE
- FortiAP 321C
Here is the layout:
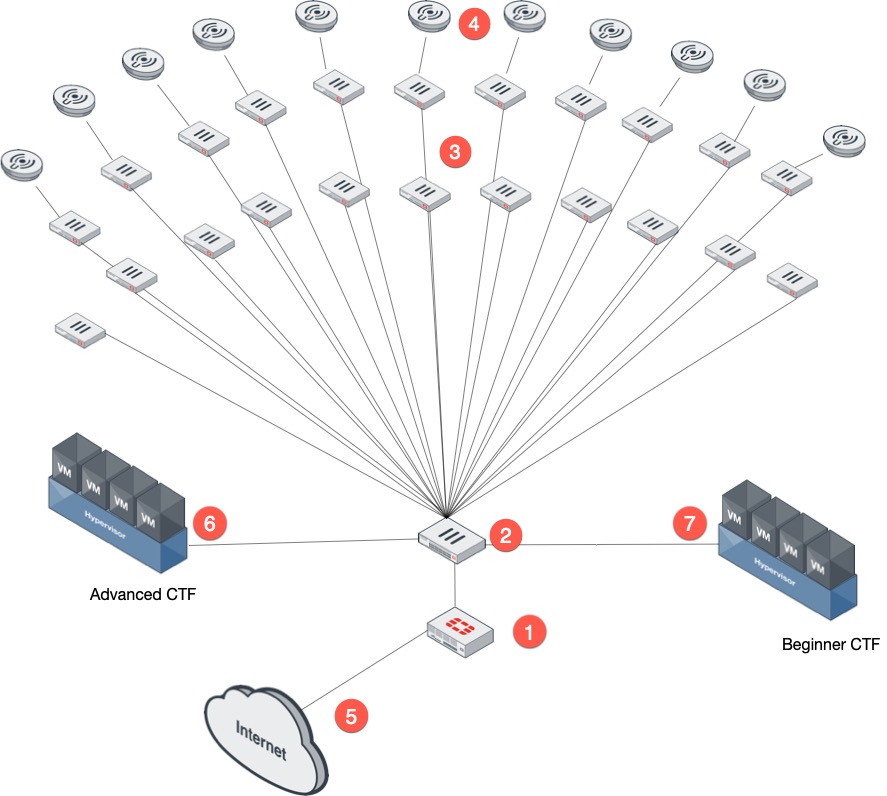
In this environment here are the pieces:
- Fortigate – The Fortigate, the focal point of the config controlled all the switches as well as the Access Points.
- FortiSwitch 448D-FPoE served as the distribution switch for all the tables (3).
- FortiSwitch 124D-PoE – These switches powered the Access Points (4) and allowed the participants to plug into their respective table.
- Access Points – In previous years (prior to 2018) there was no wireless capability for the games. Starting 2018, we provided WiFi as well.
- Internet Access – Also prior to 2018, there was no Internet access from the game itself. Thanks to the gracious IT Department at FIU, they provided an Internet connection for us to use.
- Advanced CTF Environment – The advanced CTF environment was segmented from the Beginner network. They too had an SSID for their teams. This year, Rod Soto integrated an IOT flag involving a lamp. The challenge was to change the color of the light.
- Beginner CTF Environment – The Beginner environment was segmented as well from the advanced and even from other beginner teams.
Each table had their own subnet which kept them isolated from the other tables and Beginner SSID segments as well.
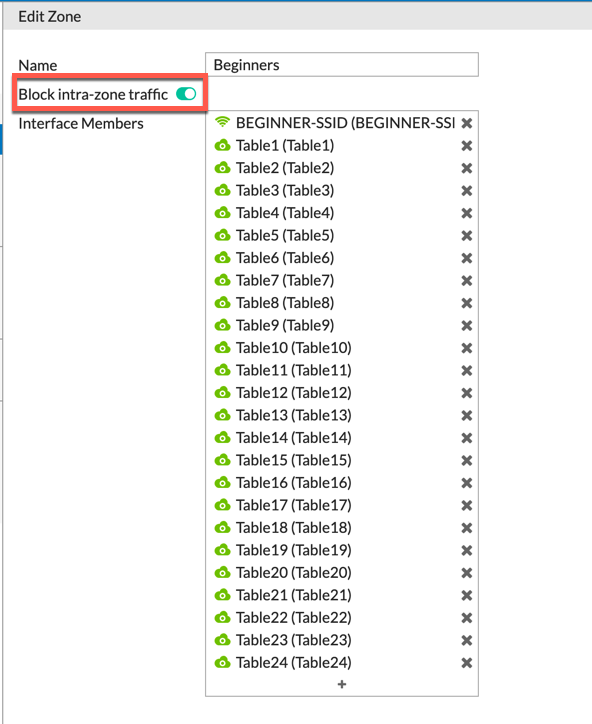
As you can see, we used the Block intra-zone traffic setting int the Zone configurations.
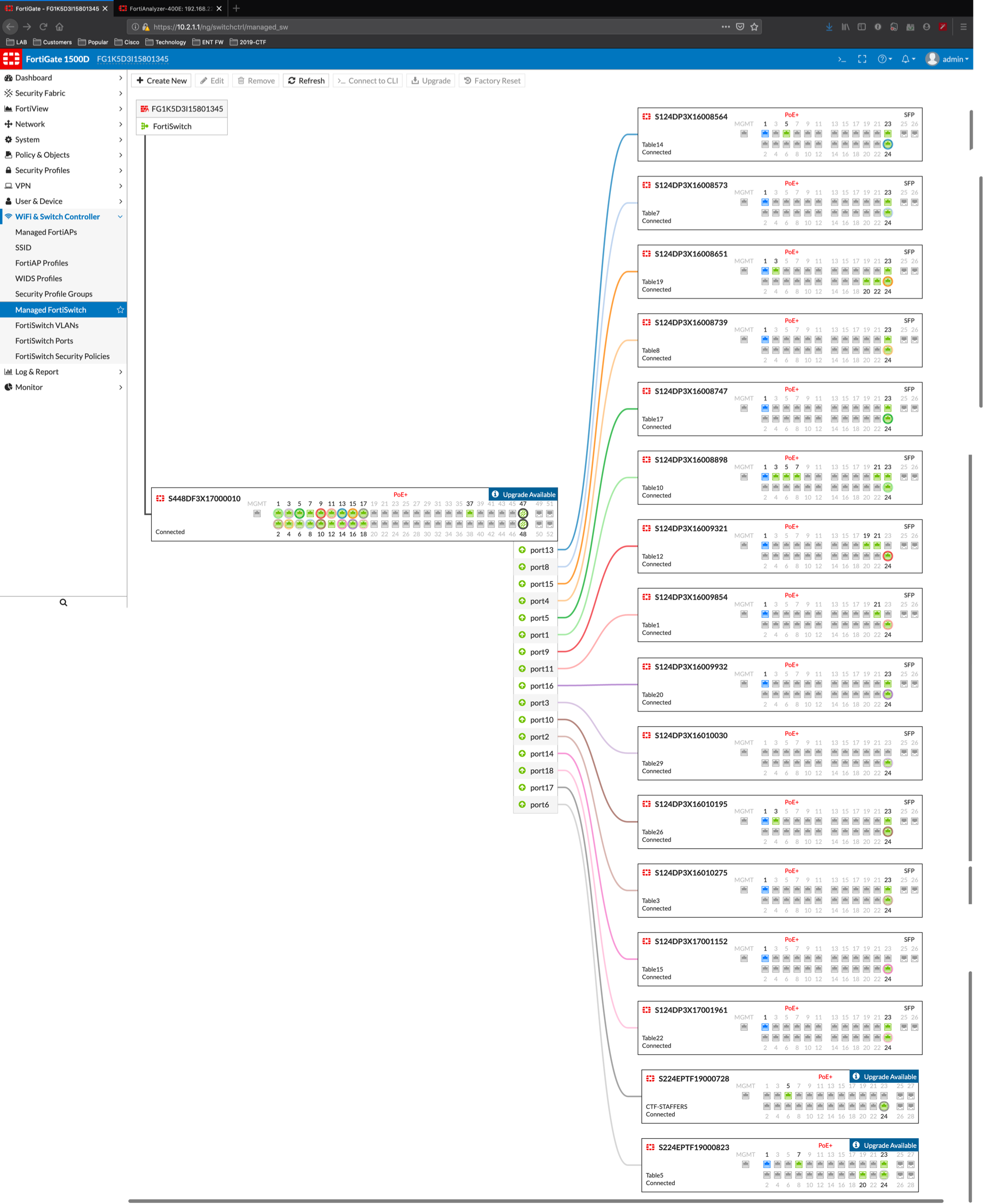
From within the Fortigate, we were able to manage and monitor all the traffic from the switches
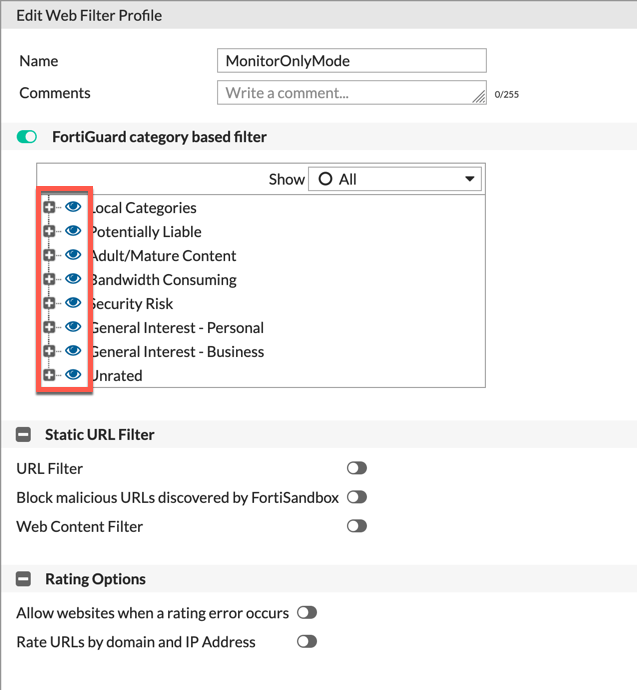
Security Profiles
To capture all of the Good traffic as well as the Bad traffic, we set up Monitor-Only profiles and assigned them to the policies.
Web Filter
DNS Filter
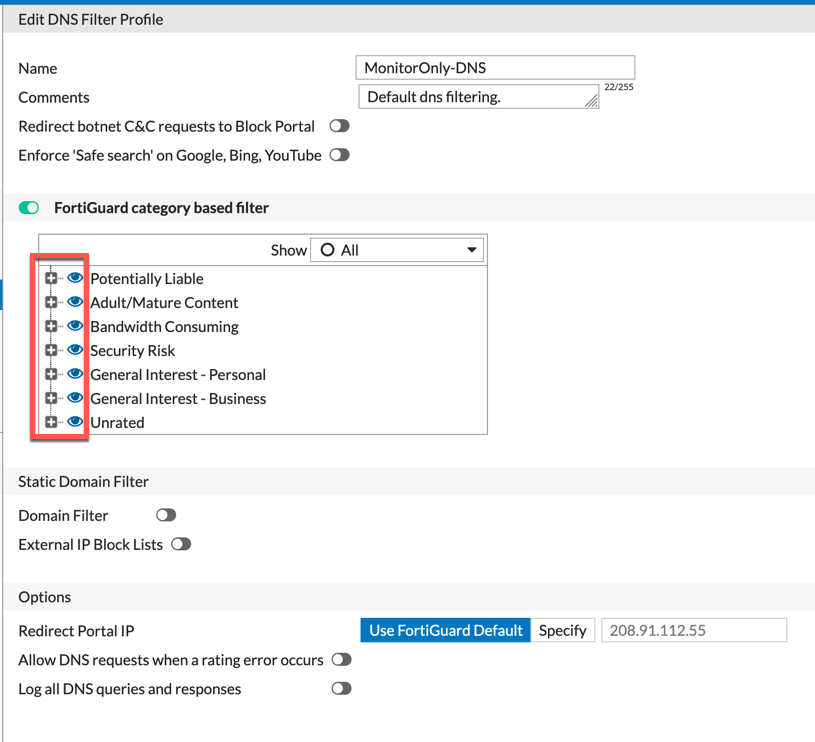
Application Profile
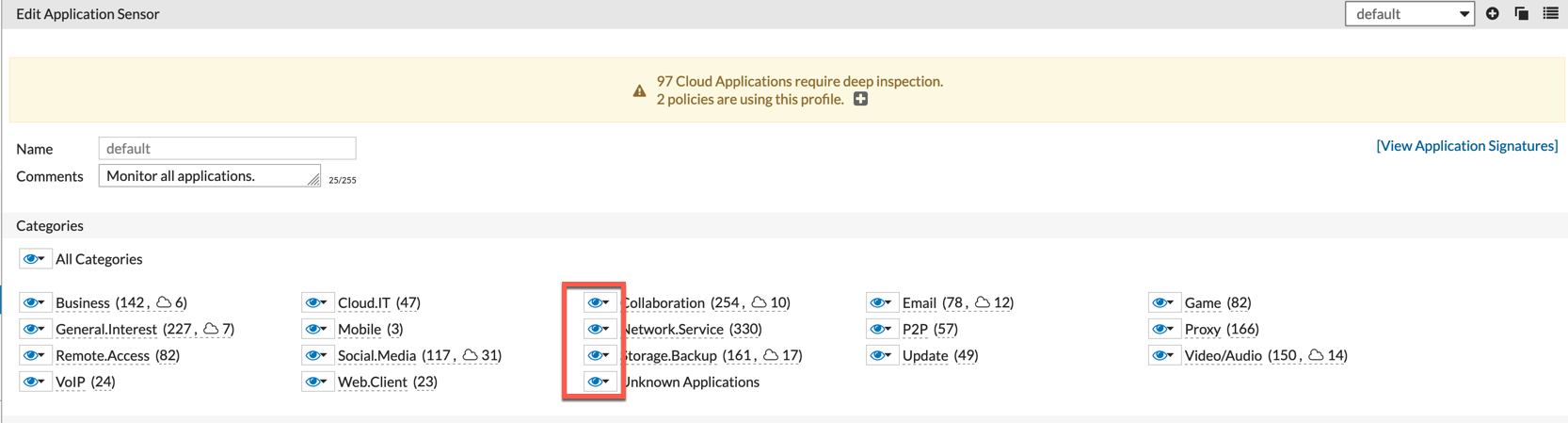
IPS Profile
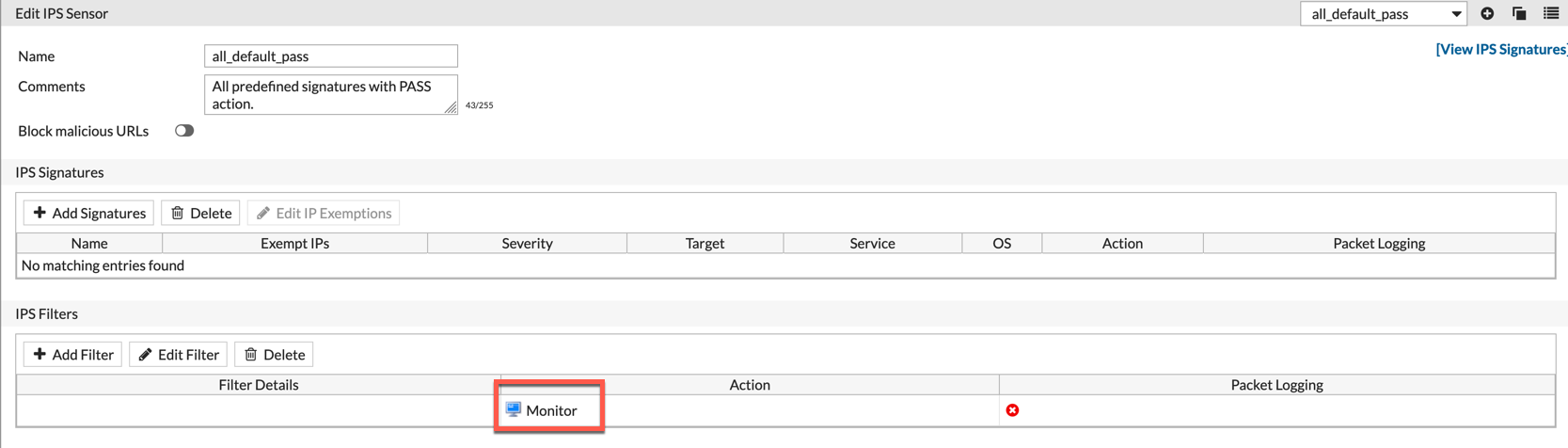
Interface Configuration
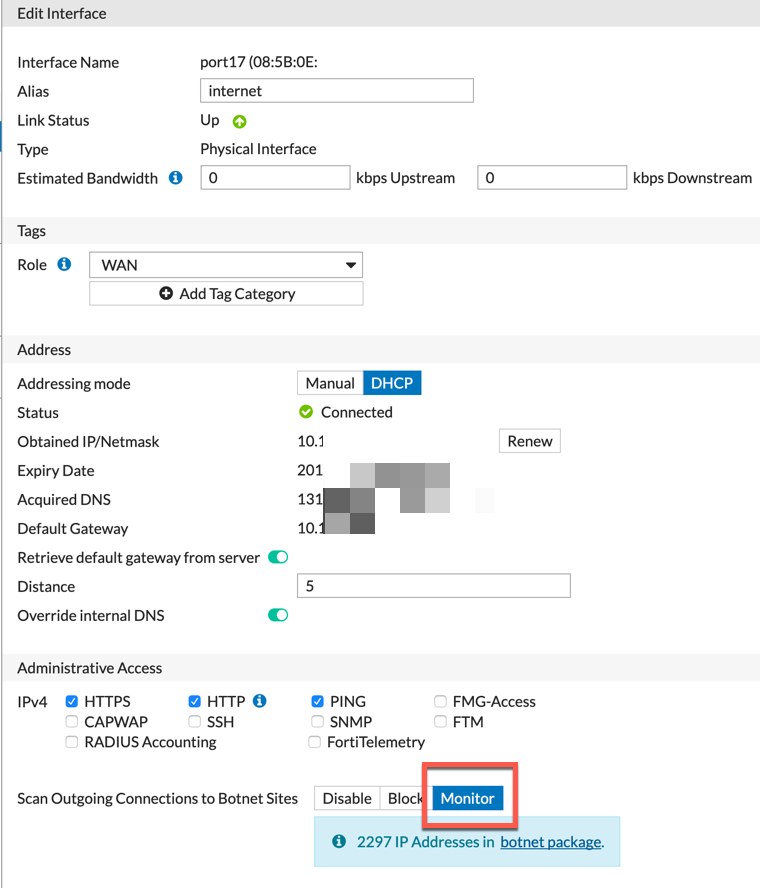
As you can see above, we are using the Scan Outgoing Connection to Botnet Sites with the monitor mode.
Logging
In addition to the FAZ-400F we had on-site, we also had one of the event coordinators run a Splunk instance so we were dumping all the logs to Splunk and FortiAnalyzer.
WiFi Clients
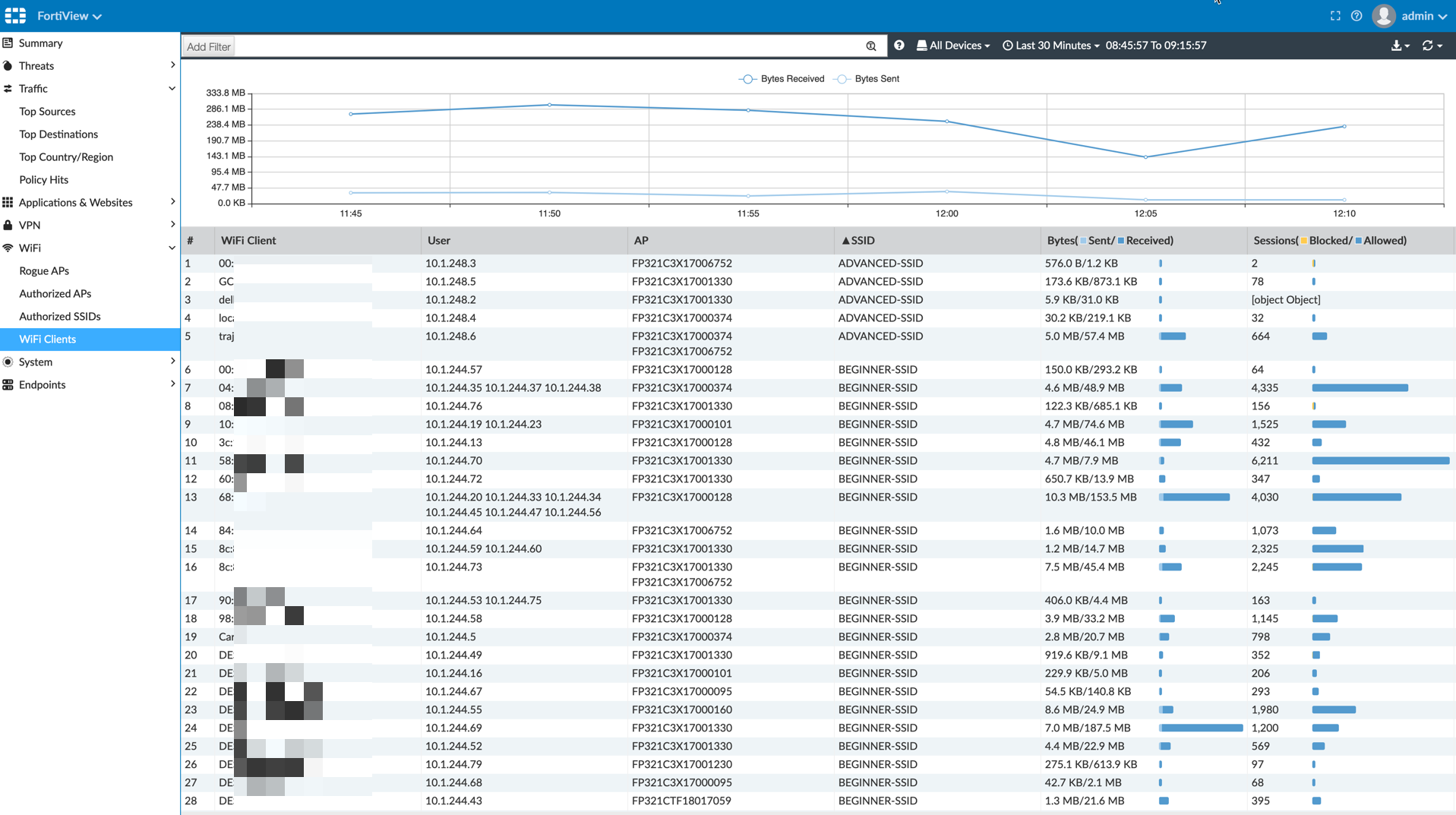
As you can see above, we had a good number of users connected to the WiFi which was truly great.
FortiAnalyzer FortiView
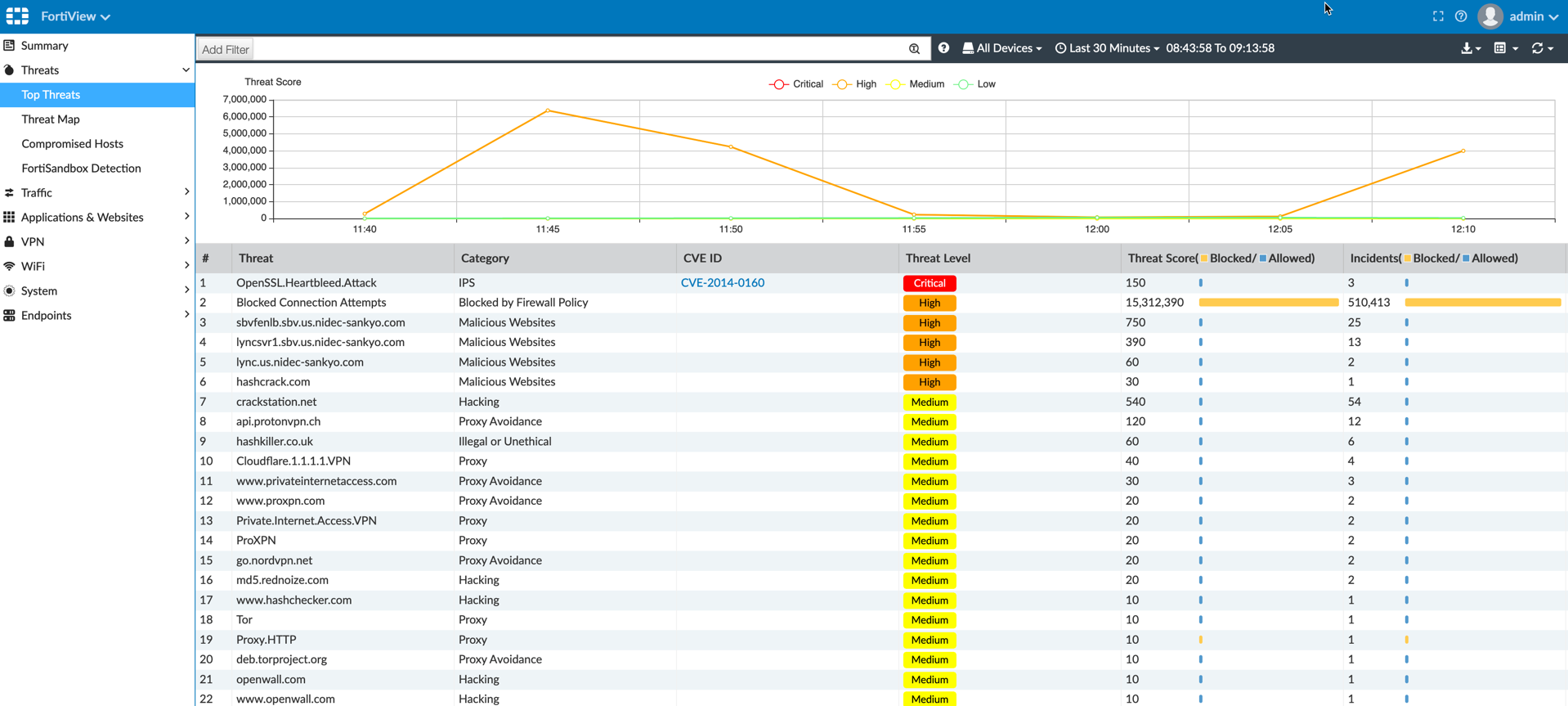
Later in the game, we blocked BitTorrent to limit the downloads.
Advanced IOT Flag SUCCESS


Recent posts
-

-

Apple shortcuts have been an amazing addition to IOS. ... Full Story
-

Years ago, when I started using FortiGates, I had... Full Story
