There are many options when troubleshooting in FortiGate firewalls. ... Full Story
By Manny Fernandez
September 9, 2019

Using Active Directory Groups to Control Web Content Policies
This is another question I get asked a lot. When customers first deploy a Fortigate firewall and they have migrated from another platform, they are unaware of the Active Directory (AD) integration with the Fortigate. When you create Web Content Filter profiles, you may want to assign them to a particular AD group. Fortinet has different ways of using AD groups in the IPv4 / v6 Policies.
- Direct Pole – Using the Fabric Connector section, you can have the Fortigate poll the AD server(s). This does not require agents on Active Directory Server.
- FSSO Agent – The Fortinet Single Sign-On agent. This agent is installed on a server that is part of the domain. Not necessarily a Domain Controller but COULD be.
- FortiAuthenticator – With the mobility agent, which is a small foot-print agent installed on the PC, there is no need to poll the AD since the agents will contact the FortiAuthenticator (FAC) with the logged on user. The Fortigate will query the FAC and gather the information.
- FortiNAC – With FortiNAC, you can integrate with the FortiGate to populate the user based on the NAC Authentication.
In this post, I will cover the Direct Poll as well as a bit on FSSO . Either way, once you can identify the user, you will be able to use that user to match inside a policy.
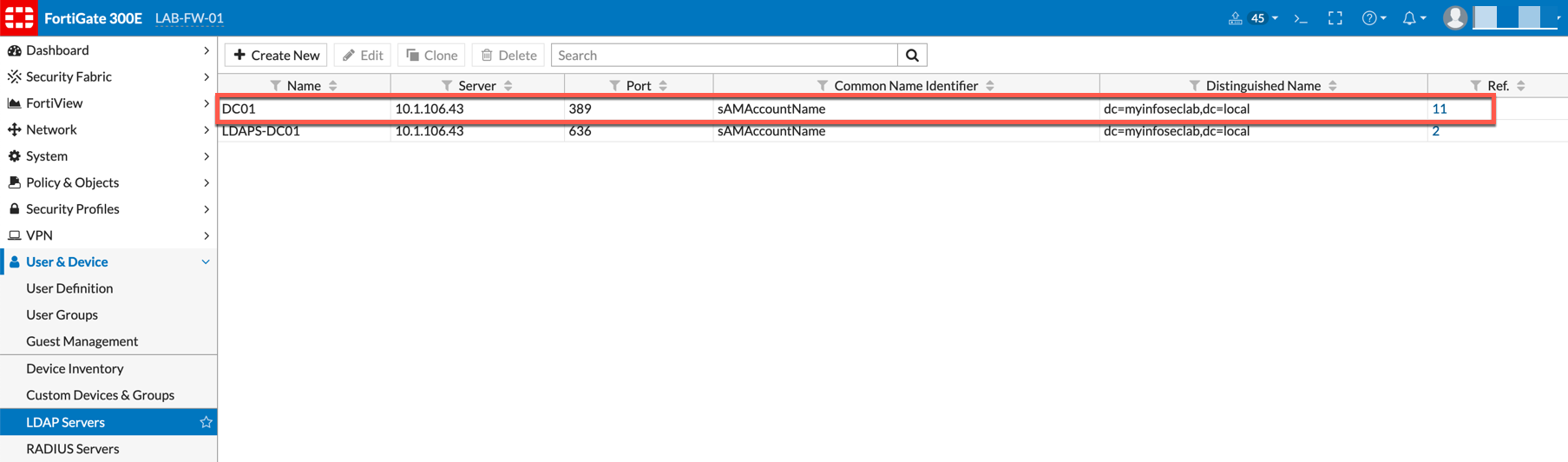
Connecting to an LDAP Server
With the Fortigate, we can add multiple domains from multiple forests and poll them for users based on User Groups and IPv4 Policies.
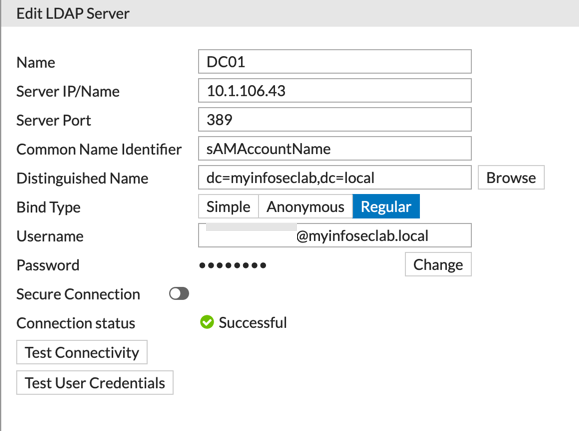
Above you can see the screenshot from my lab DC. Key thing to remember here is to use the sAMAccountName on the Common Name Identifier . It is absolutely case sensitive. You can add a user, set the Bind Type to Regular. The username can use the @domain-name.c . You can Test Connectivity to test the connection to the LDAP server. Finally, you can Test User Credentials .
Active Directory Groups
I normally set up groups that match the names I use in the Fortigate Configuration
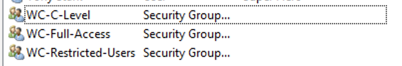
As you can see, I created Web-Content Active Directory Security Groups. I will use these groups to create the policies.
Fortigate User Groups
Once you have the LDAP communication and the Active Directory Groups, you will need to create corresponding Fortigate Groups. These groups will be used in the policies.
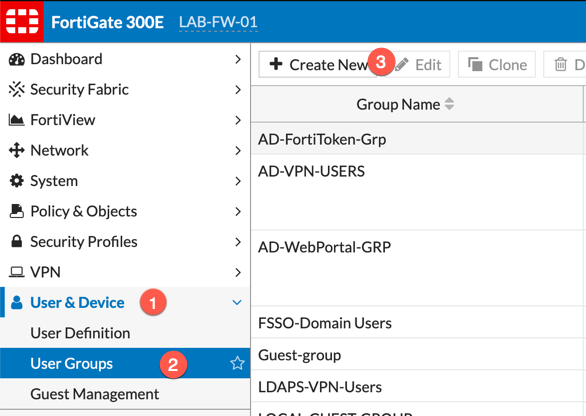
You will need to browse to (1) Users and Devices, (2) User Groups, (3) Create New
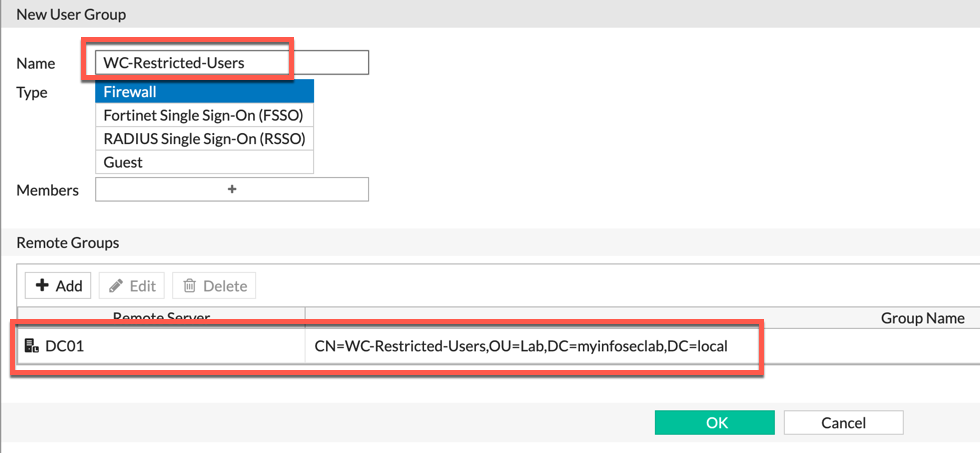
You can give the User Group a name (preferably descriptive) and choose the Remote Groups section. There you will be promoted to use the LDAP server of your choice, and Select the Security Group from Active Directory.
Setting up Direct Polling
In this section, you will need to create a polling
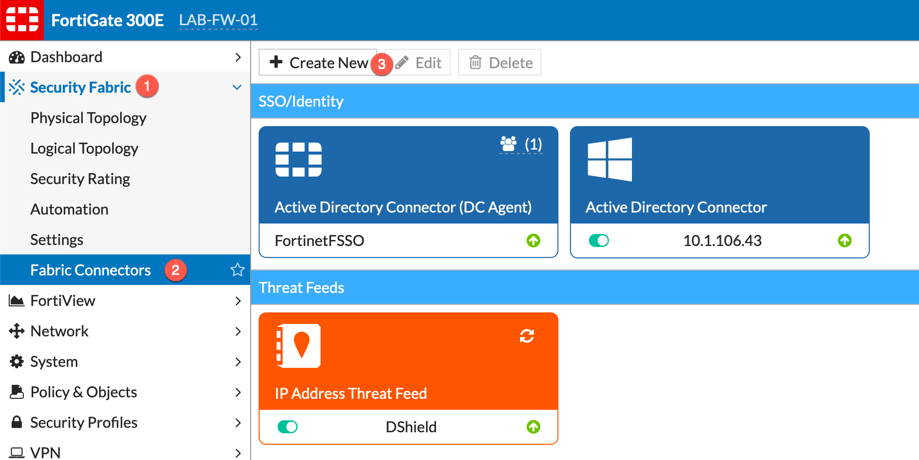
Go to Security Fabric, then choose Fabric Connectors and the Create New

You will either want to choose the Poll Active Directory Server from smaller environments or Fortinet Single Sign-on Agent
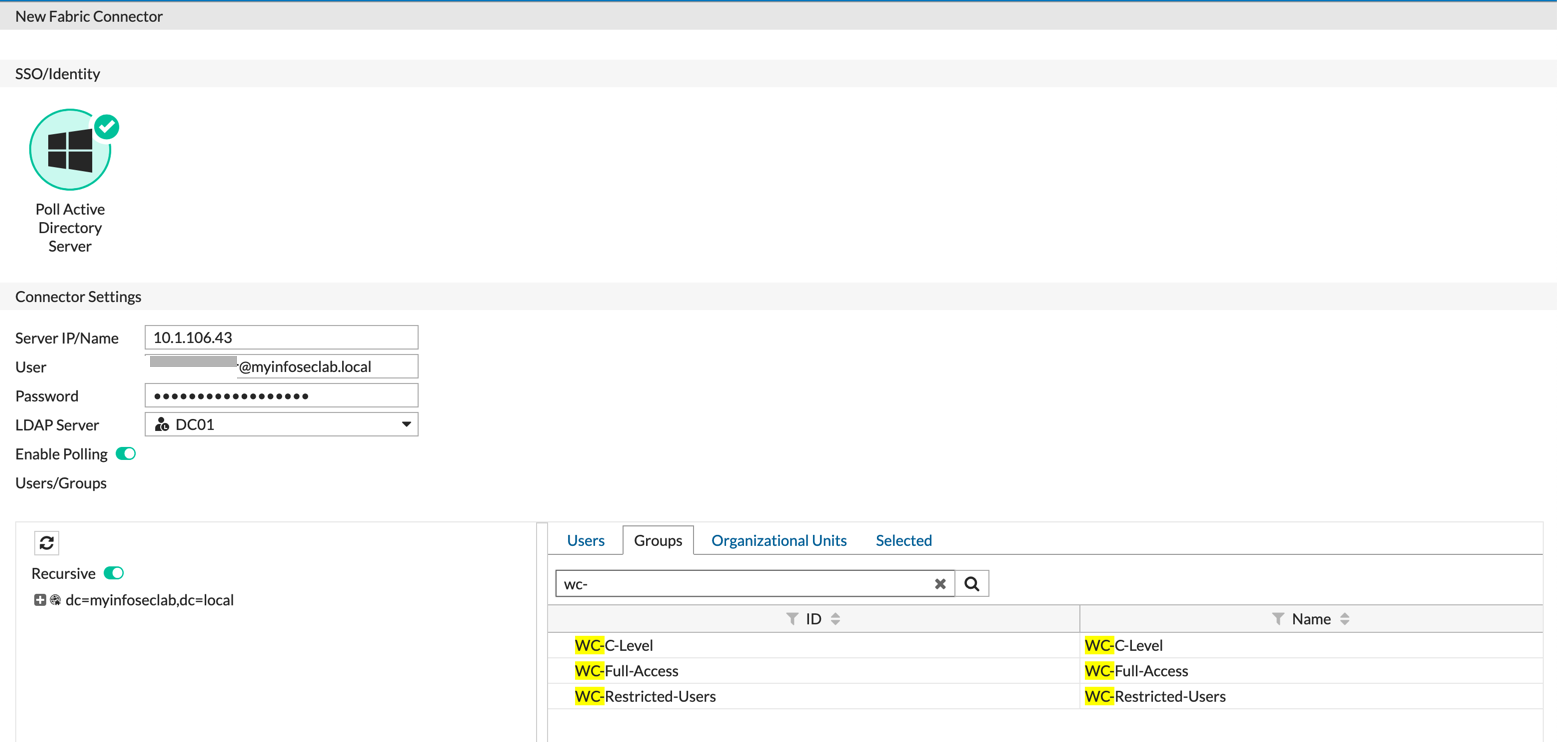
Option 1 – Direct Poll
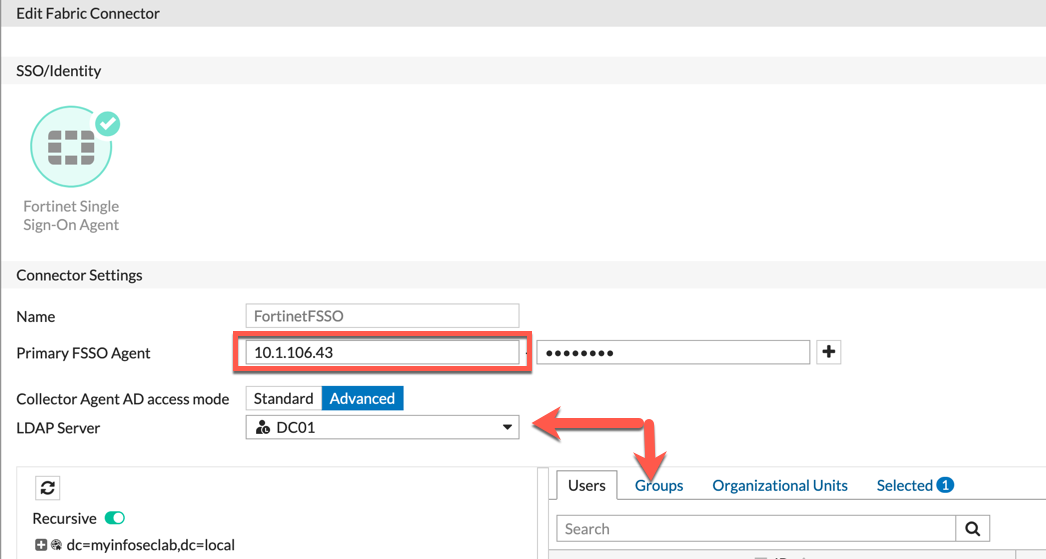
Option 2 – FSSO
Creating the Security Profile
Once you have add the groups you created, you can now go to the Web-Filter profile.
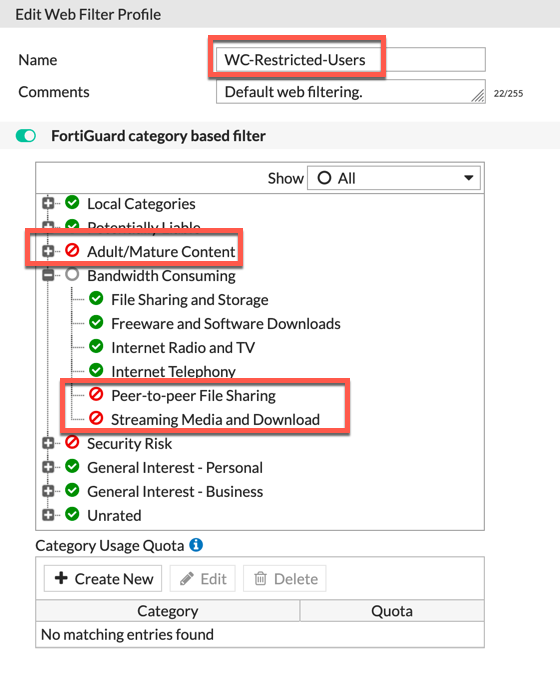
In the example above, I am blocking Adult/Mature Content as well as Security Risk and some categories of the Bandwidth Consuming group.
Using the Profile in a Policy
Now we have all the pieces in place to create the policy. Note that you can create an `Application Control, AV, IPS, DLP, etc. profile as well and add to the policy. These will match those users in the AD group as well.
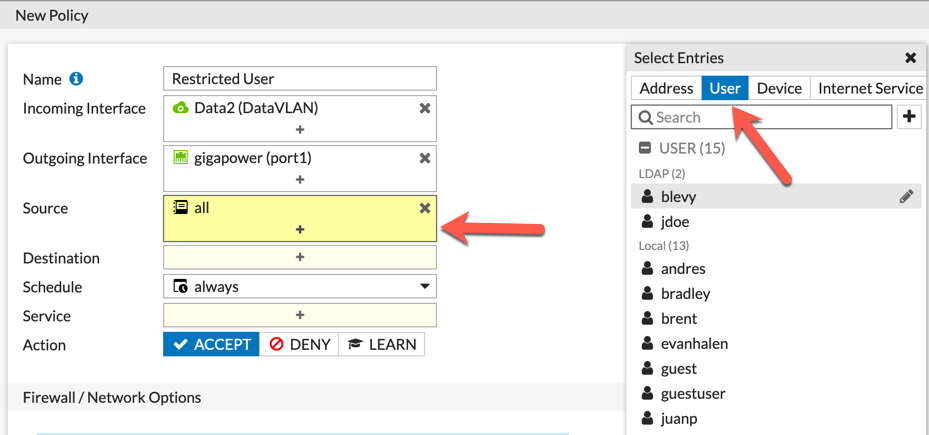
Above, we can see the creation of the policy. We can see that we chose the Data2 VLAN as the source and the destination as Gigapower . Then on the source, we chose all and then we are going to choose User-Group.
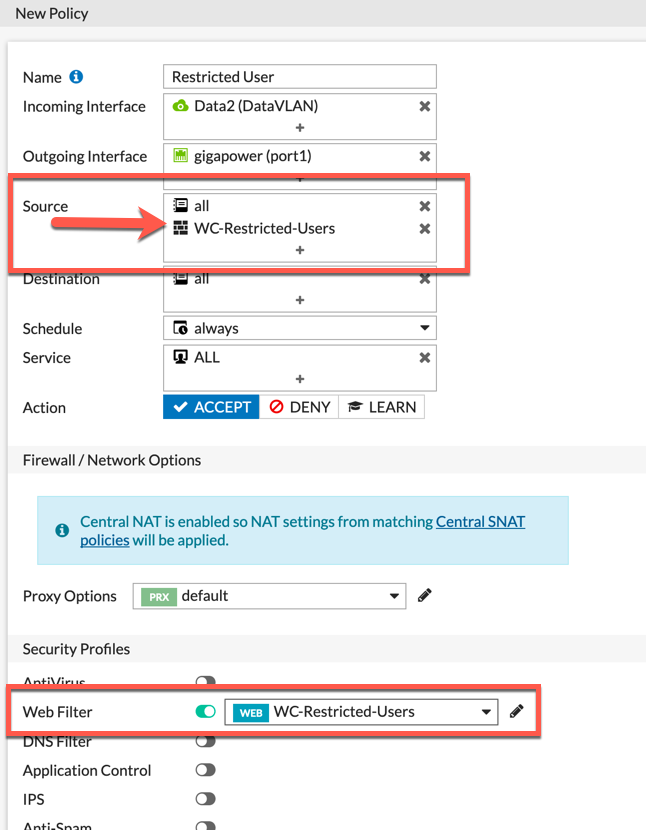
You can see the WC-Restricted-Users listed in the Source section.
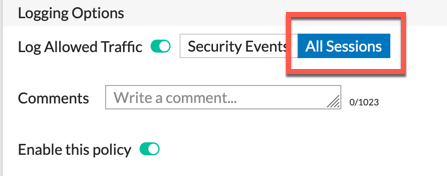
Logging
Also noteworthy is the logging section of the policy. If you want to capture and report on allowed traffic as well as the blocked, you will need to log All Session
Recent posts
-

-

Have you ever had an IPS signature that continues... Full Story
-

Use case: Customer has a Split Tunnel Enabled but... Full Story
