There are many options when troubleshooting in FortiGate firewalls. ... Full Story
By Manny Fernandez
September 29, 2016

Packet Capture on Cisco ASA Firewall
This post is a four part post geared at engineers looking to do packet captures on Cisco ASA, PaloAlto and Fortinet Fotigate followed by a tcpdump overview as well. In this post, I am focussing on the ASA and its different forms of packet capture and how to display and download the captures you are capturing. I will cover both command line as well as ASDM.

Cisco Adaptive Security Appliance (ASA)
Command Line
The ASA has a few ways to perform the packet capture. There is the command line and the Adaptive Security Device Manager (ASDM). The ‘cli’ has a couple of ways to do this. One is by creating an access list and identifying the match criteria, then calling that access list from the capture command; the other bring a one line command defining source/destination and interface.
One Line
The one line option is as follows:
capture capin interface inside match ip host 192.168.1.1 host 10.1.1.1
By adding this line into the cli, you would create a capture instance named ‘capin’ on interface ‘inside’ that is looking to match any traffic matching ‘192168.1.1’ or ’10.1.1.1’. It will also capture it in raw format.
Options for this command are as follows:
port – (Optional) If you set the protocol to tcp or udp, specifies the integer or name of a TCP or UDP port.
raw-data – (Optional) Captures inbound and outbound packets on one or more interfaces. This setting is the default.
real-time – Displays the captured packets continuously in real-time. To terminate real-time packet capture, enter Ctrl + c. This option applies only to raw-data and asp-drop captures.
tls-proxy – (Optional) Captures decrypted inbound and outbound data from TLS Proxy on one or more interfaces
trace trace_count – (Optional) Captures packet trace information, and the number of packets to capture. This is used with an access list to insert trace packets into the data path to determine whether the packet is processed as expected.
type – (Optional) Specifies the type of data captured.
url url – (Optional) Specifies a URL prefix to match for data capture. Use the URL format http://server/path to capture HTTP traffic to the server. Use https://server/path to capture HTTPS traffic to the server.
user webvpn-user – (Optional) Specifies a username for a WebVPN capture.
webvpn – (Optional) Captures WebVPN data for a specific WebVPN connection.
Displaying the packet capture.
sh capture capin
decode Display decode information for each packet
1: 23:58:31.819522 10.10.2.164.64309 > 10.13.13.11.43022: S 2233355225:2233355225(0) win 8192 <mss 1380,nop,wscale 8,nop,nop,sackOK>
2: 23:58:34.840380 10.10.2.164.64309 > 10.13.13.11.43022: S 2233355225:2233355225(0) win 8192 <mss 1380,nop,wscale 8,nop,nop,sackOK>
3: 23:58:34.854982 10.13.13.11.43022 > 10.10.2.164.64309: R 2207241527:2207241527(0) ack 2233355226 win 0
4: 23:58:35.371120 10.10.2.164.64309 > 10.13.13.11.43022: S 1416202529:1416202529(0) win 8192 <mss 1380,nop,nop,sackOK>
detail Display more information for each packet
1: 23:58:31.819522 ecbd.1d85.72d9 a493.4c1d.ad8d 0x0800 Length: 66
10.10.2.164.64309 > 10.13.13.11.43022: S [tcp sum ok] 2233355225:2233355225(0) win 8192 <mss 1380,nop,wscale 8,nop,nop,sackOK> (DF) (ttl 127, id 23855)
2: 23:58:34.840380 ecbd.1d85.72d9 a493.4c1d.ad8d 0x0800 Length: 66
10.10.2.164.64309 > 10.13.13.11.43022: S [tcp sum ok] 2233355225:2233355225(0) win 8192 <mss 1380,nop,wscale 8,nop,nop,sackOK> (DF) (ttl 127, id 23893)
3: 23:58:34.854982 a493.4c1d.ad8d ecbd.1d85.72d9 0x0800 Length: 54
10.13.13.11.43022 > 10.10.2.164.64309: R [tcp sum ok] 2207241527:2207241527(0) ack 2233355226 win 0 (DF) (ttl 127, id 32526)
4: 23:58:35.371120 ecbd.1d85.72d9 a493.4c1d.ad8d 0x0800 Length: 62
dump Display hex dump for each packet
1: 23:58:31.819522 10.10.2.164.64309 > 10.13.13.11.43022: S 2233355225:2233355225(0) win 8192 <mss 1380,nop,wscale 8,nop,nop,sackOK>
0x0000 a493 4c1d ad8d ecbd 1d85 72d9 0800 4500 ..L…….r…E.
0x0010 0034 5d2f 4000 7f06 7acf 0a0a 02a4 0a0d .4]/@…z…….
0x0020 0d0b fb35 a80e 851e 4bd9 0000 0000 8002 …5….K…….
0x0030 2000 b75e 0000 0204 0564 0103 0308 0101 ..^…..d……
0x0040 0402 ..
2: 23:58:34.840380 10.10.2.164.64309 > 10.13.13.11.43022: S 2233355225:2233355225(0) win 8192 <mss 1380,nop,wscale 8,nop,nop,sackOK>
0x0000 a493 4c1d ad8d ecbd 1d85 72d9 0800 4500 ..L…….r…E.
0x0010 0034 5d55 4000 7f06 7aa9 0a0a 02a4 0a0d .4]U@…z…….
0x0020 0d0b fb35 a80e 851e 4bd9 0000 0000 8002 …5….K…….
0x0030 2000 b75e 0000 0204 0564 0103 0308 0101 ..^…..d……
0x0040 0402 ..
packet-number Display packet <number> in capture (in the example, 17)
17: 23:58:39.504734 10.13.13.11.43022 > 10.10.2.164.64309: R 777829587:777829587(0) ack 954091150 win 0
1 packet shown
trace Display extended trace information for each packet
1: 23:58:31.819522 10.10.2.164.64309 > 10.13.13.11.43022: S 2233355225:2233355225(0) win 8192 <mss 1380,nop,wscale 8,nop,nop,sackOK>
2: 23:58:34.840380 10.10.2.164.64309 > 10.13.13.11.43022: S 2233355225:2233355225(0) win 8192 <mss 1380,nop,wscale 8,nop,nop,sackOK>
3: 23:58:34.854982 10.13.13.11.43022 > 10.10.2.164.64309: R 2207241527:2207241527(0) ack 2233355226 win 0
The other way is by creating an access-list and then using that access-list to match the capture:
access-list capin extended permit tcp host 192.168.1.1 host 10.1.1.1 eq 80
access-list capin extended permit tcp host 192.168.1.1 host 10.1.1.1 eq 443cap capin access-list capin in interface inside
In the example above, we created an access-list named ‘capin’ which matched traffic from 192.168.1.1 to 10.1.1.1 on port 80 and 443. We then created the capture named ‘capin’ and told it to use the access-list named ‘capin’. We applied it to the inside interface. Now you can use the same ‘sh cap’ commands you used above to display the packets captured.
A good idea to keep these capture right in your head is to name them using the following naming convention:
If you are capturing inbound packets on the ‘inside’ interface, use: inside-in
If you are capturing outbound packet on the ‘inside’ interface, use: inside-out
To download the capture: https://%IP-Address-of-ASA%/capture/%Capture-Name%
Adaptive Security Device Manager (ASDM)
The ASA has a nice Java based GUI for it. The worst thing about it is the very fact that it is Java based and has issues (as does other Java based programs) running in environments that have Java getting updated. Cisco is working on a unified platform with their ASA and SourceFIRE platforms and hopefully it will be an HTML 5 version, although that introduces an entirely new set of challenges and issues.
From the ASDM, go up to ‘Wizards’ and choose ‘Packet Capture Wizard’
Choose ‘Next’
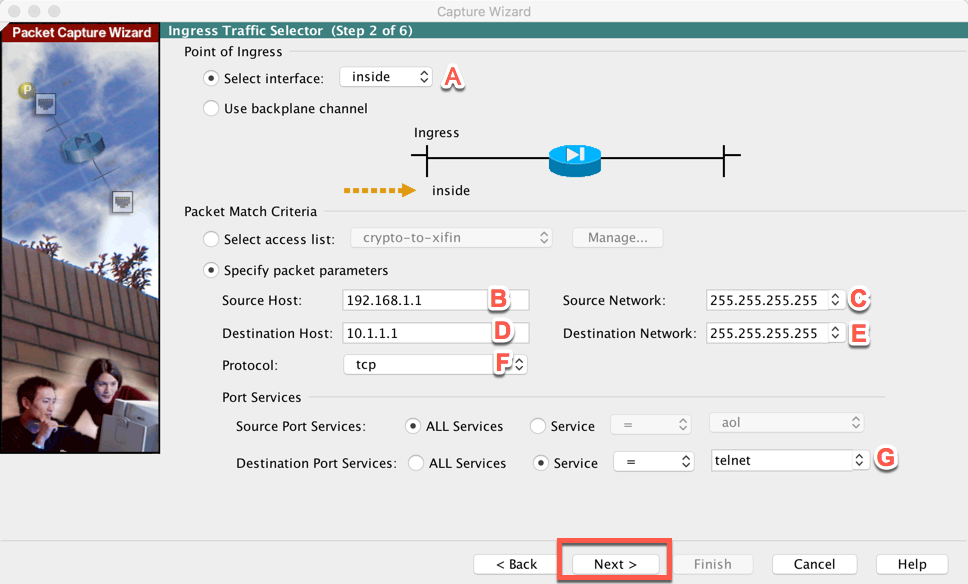
Now you will need to define what packets are going to match. I will break down the sections:
A – This is the ingress interface; where the packets are coming from (source).
B – Here you define the source IP
C – Subnet mask. If you select a ‘host’ in B, this must be all ‘255’
D – Destination IP or network. If you want to do ‘any’ you will need to enter 0.0.0.0.
E – Subnet mask for the network, all 255 for host, or 0.0.0.0 for any
F & G – Allow you to select traffic based on source/destination/protocol etc.
Now choose ’Next’
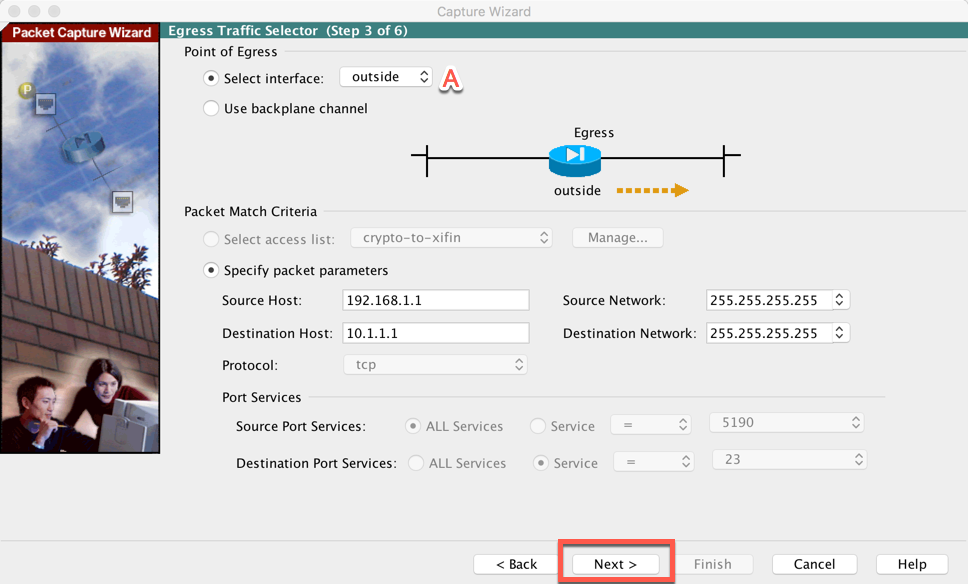
In this screen, you will only need to choose the egress interface or where the packets are existing from. Now choose ‘Next’
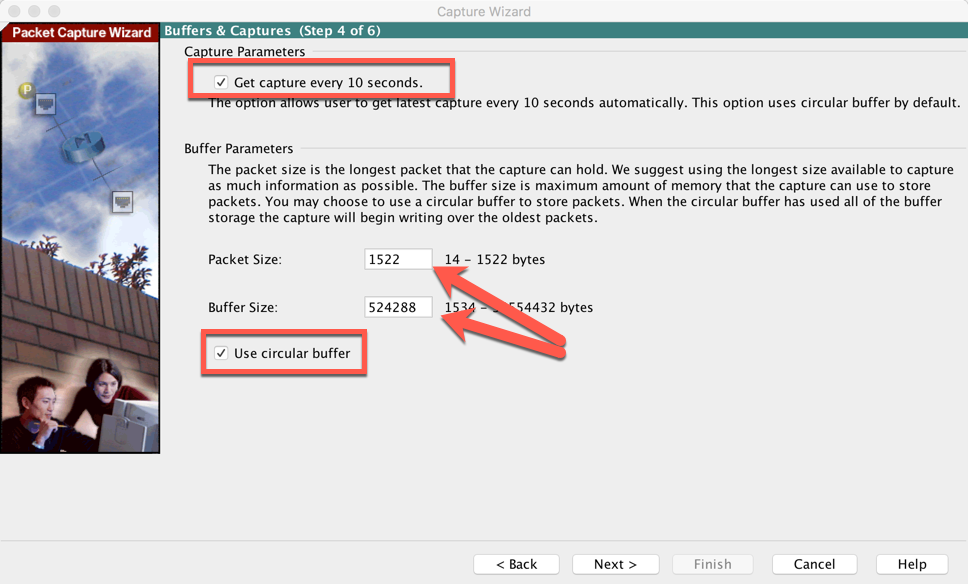
The first box is very useful when you want it to update the capture ever 10 seconds. If you do not choose this, you will need to manually update the capture on the next screen.
Also, you can set the size of the capture and choose the circular logging. Then hit next.
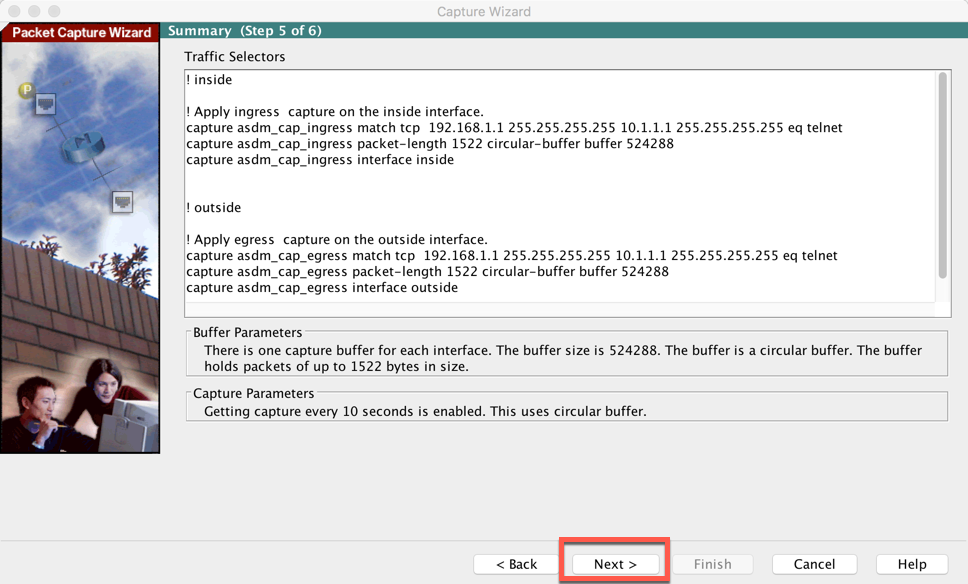
The next screen actually gives you the equivalent cli command. Now hit ‘Next’
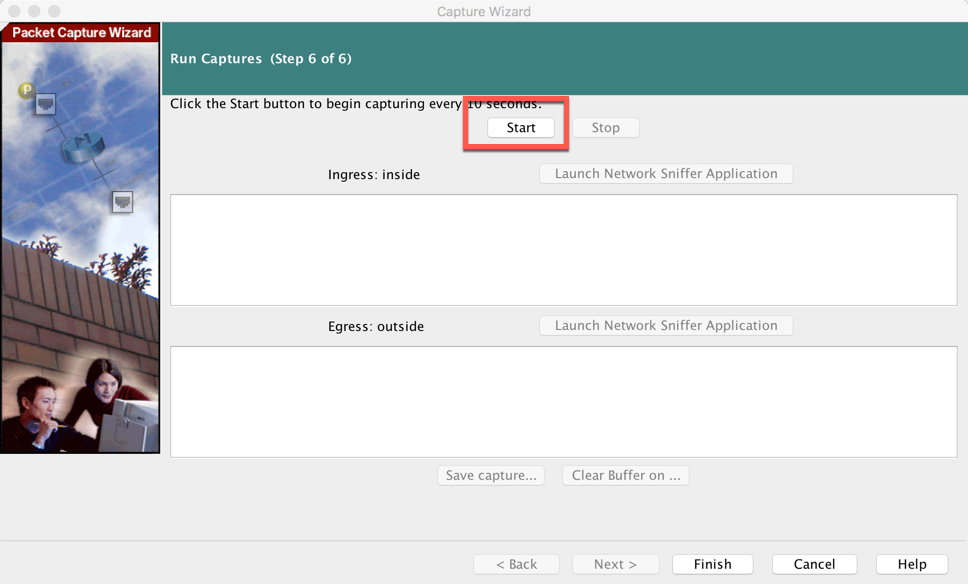
Now you need to actually ‘Start’ the capture.
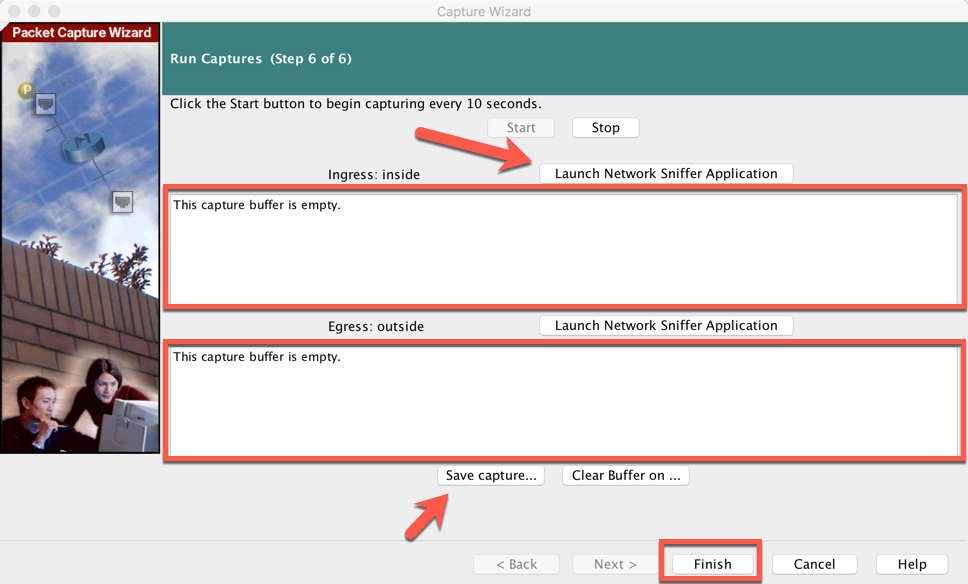
Once the capture starts to populate the ‘Ingress’ and ‘Egress’ sections, you can hit the ‘Launch Network Sniffer Application’ (You need to have the path in preferences). You can save the capture by clicking ‘Save Capture’. Now Finish.
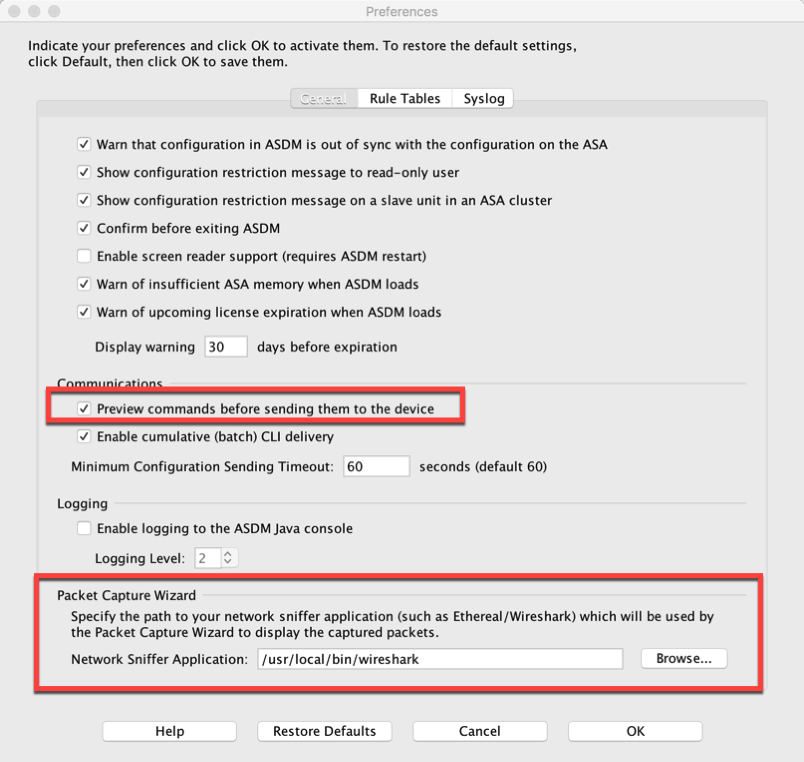
You can select the path to your ‘Network Sniffer’.
You should also select the ‘Preview Commands before sending them to the devices’. It will display the commands before sending them to the ASA. It is a good way to learn the cli version of the GUI change you made.
Recent posts
-

-

Have you ever had an IPS signature that continues... Full Story
-

Use case: Customer has a Split Tunnel Enabled but... Full Story
