There are many options when troubleshooting in FortiGate firewalls. ... Full Story
By Manny Fernandez
April 27, 2020

Syslog Filtering on FortiGate Firewall & Syslog-NG
We recommend sending FortiGate logs to a FortiAnalyzer as it produces great reports and great, usable information. However sometimes, you need to send logs to other platforms such as SIEMs. When sending to a SIEM, you usually have an EPS or Event Per-Second charge, although some have moved to total amount of data. You may want to filter some logs from being sent to a particular syslog server. Here is a quick How-To setting up syslog-ng and FortiGate Syslog Filters.
I am going to install syslog-ng on a CentOS 7 in my lab. I always deploy the minimum install.
Installing Syslog-NG
This will be a brief install and not a lot of customization. Syslog-NG has a corporate edition with support. Syslog-NG (paid and community versions) allow you to create a distributed syslog environment. In another life, I owned an MSSP and we had an instance of syslog-ng running on our Linux firewalls and they would collect locally and forward to our SOC for processing and archival.
Note: Although this article contains a syslog-ng install, you can obviously use any syslog solution.
After you have a vanilla CentOS box up and running, you will need to install the repository and then the packages.
yum install wget wget https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm rpm -Uvh epel-release-latest-7.noarch.rpm cd /etc/yum.repos.d/ wget https://copr.fedorainfracloud.org/coprs/czanik/syslog-ng324/repo/epel-7/czanik-syslog-ng325-epel-7.repo yum install syslog-ng #Ensure you answer yes when prompted Remove the default syslog package yum erase rsyslog Enable auto start and manually start syslog-ng systemctl enable syslog-ng systemctl start syslog-ng
After you install syslog-ng you will need to configure the /etc/syslog-ng/syslog-ng.conf file.
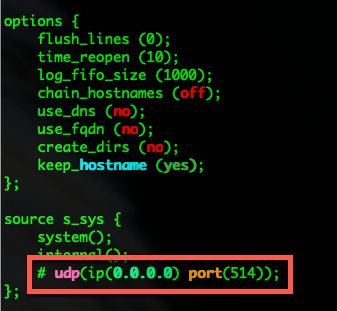
Look for the ling that is remarked out with the # and remove the #. The config should like the one below.
Note: You will need to sudo or su if not the file will be read-only. If you are using vi as I do, the command to allow you to edit the file will be i and once you are done, you need to hit esc then x
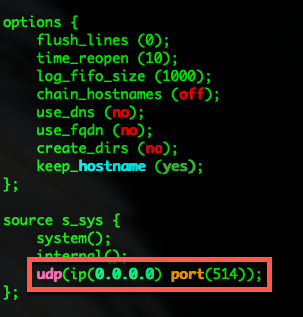
You will also need to either disable the firewall or create a rule allowing UDP 514 or whatever port you defined in the /etc/syslog-ng/syslog-ng.conf
Configuring the FortiGate
The FortiGate allows you to configure multiple FortiAnalyzers (FAZ) and multiple syslog servers. I will not cover FAZ in this article but will cover syslog.
LAB-FW-01 # config log syslogd syslogd Configure first syslog device. syslogd2 Configure second syslog device. syslogd3 Configure third syslog device. syslogd4 Configure fourth syslog device.
When configuring syslog servers on the FortiGate, you can see on the snippet above that you have 4 syslog servers you can create. In this example I will use syslogd the first one available to me.
config log syslogd setting
set status enable
set server "10.1.106.218"
set source-ip "10.1.106.1"
end
In my example, I am enabling this syslog instance with the set status enable then I will set the IP address of the server using set server "10.1.106.218" and the source-ip with the set source-ip "10.1.106.1".
There are other configurations you can add such as format (default, csv, or cef), etc.
config log syslogd setting set status enable set server "10.1.106.218" set mode udp set port 514 set facility local7 set source-ip "10.1.106.1" set format default set priority default set max-log-rate 0 end
Configuring Filters
By replacing the settings in the syslog configuration to filter you can now define filters for that syslog instance’s configuration. Remember that each filter is tied to the syslog instance number. That is, if you want to create a filter for your syslogd2 instance, you would need to enter config log syslogd2 filter and so on for the others.
config log syslogd filter
set severity information
set forward-traffic enable
set local-traffic enable
set multicast-traffic enable
set sniffer-traffic enable
set anomaly enable
set voip enable
set filter "logid(0100032002)"
set filter-type include
end
As you can see in my filter, I ONLY want authentication messages with the following message id 0100032002
The other important command above is the filter-type . With this command, you can make the matched message ID’s from the previous line either include or exclude meaning that I want everything except 0100032002 or I ONLY want 0100032002.
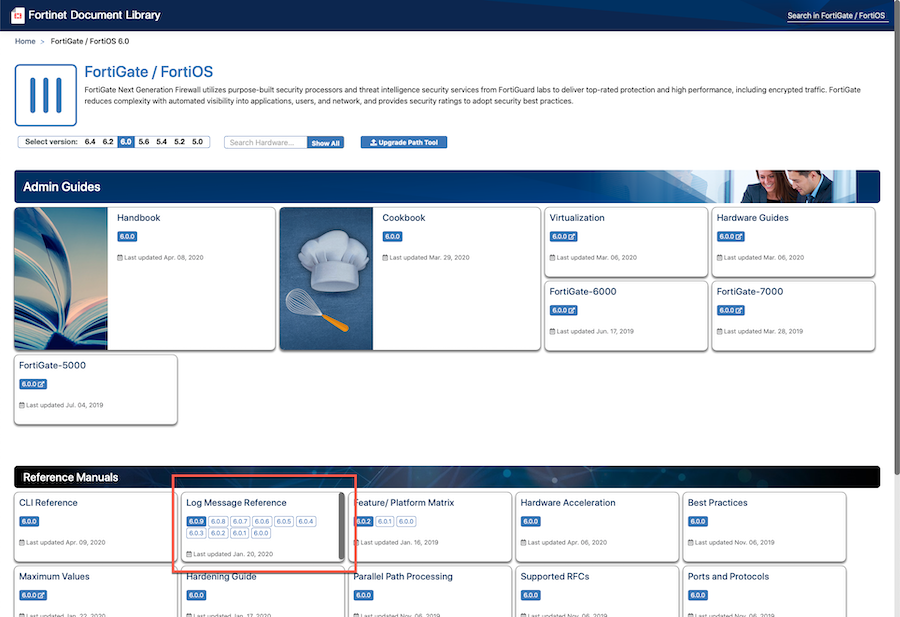
To find the message IDs, you should go to the Fortinet Docs repository. The link provided is specifically for 6.4 but you can look for your version for FortiOS. Look for the Log Message Reference section of the doc page.
Recent posts
-

-

Have you ever had an IPS signature that continues... Full Story
-

Use case: Customer has a Split Tunnel Enabled but... Full Story