There are many options when troubleshooting in FortiGate firewalls. ... Full Story
By Manny Fernandez
August 2, 2021
DNS Doctoring on FortiGate
Sometimes, you have a scenario where your internal servers or devices are using external DNS servers (e.g. 8.8.8.8 or 4.2.2.2 ) and the server are connecting to a URL of a server that is ALSO sitting behind the FortiGate. Such is the issue I ran into today.
Customer is a service provider. He has internal customer’s servers that connect to his Screen Connect server which lives inside his network. The problem was, that the internal devices were using 8.8.8.8 to resolve and the resolution was returning the external VIP IP address (information blurred to protect customer info). The issue was the specific interfaces section of the VIP.
Since the VIP is configured to specifically respond on an interface ( gig-e or outside) and not inside, when coming from the inside the VIP would not work. I changed the specific interface to any and created an inside to inside policy.
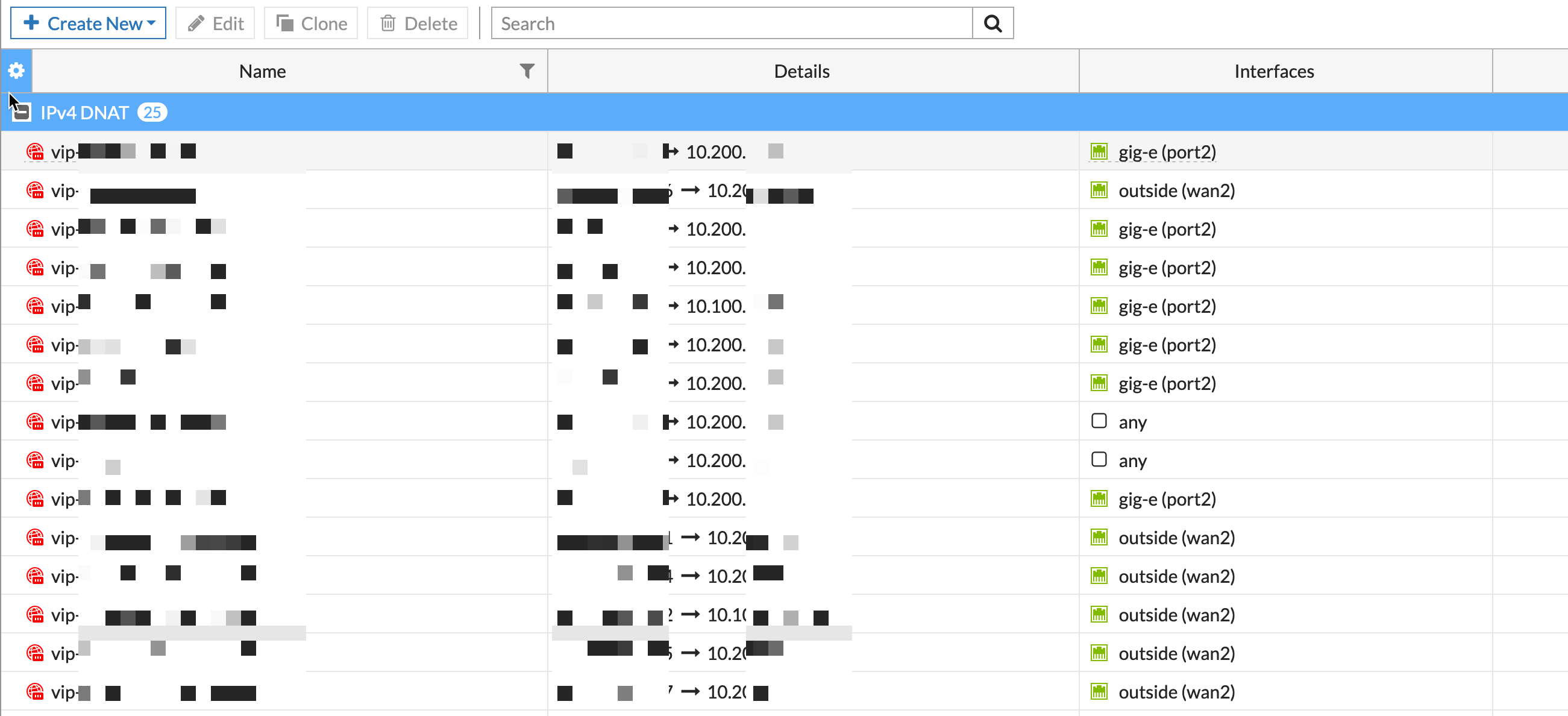
Above we can see there are two entries with any as the interfaces.
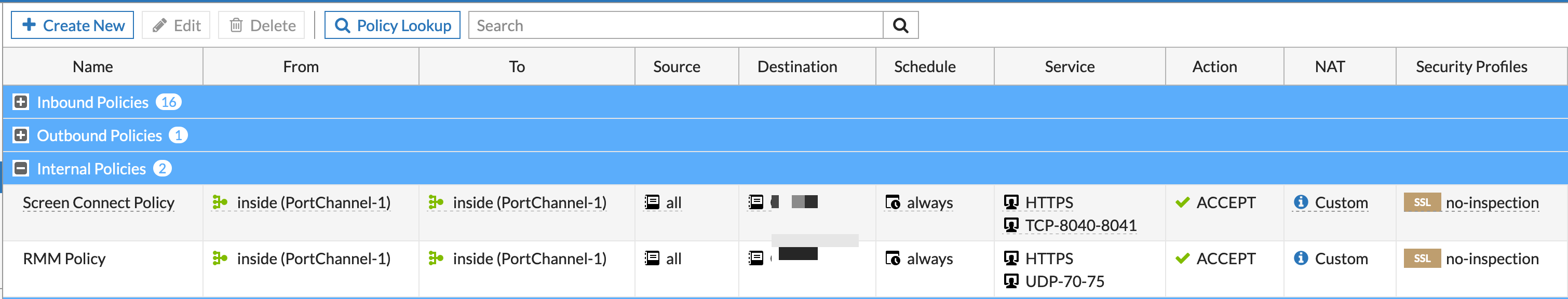
Additionally, you can see the inside to inside policy permitting specific traffic to those specific internal side of the VIPs.
Cisco
In the Cisco world, it is easier honestly, because you need to add one keyword to the NAT statement.
nat (inside,outside) source static 12.1.1.1 10.1.1.1 dns
The keyword in the statement is dns which re-writes the DNS.
The ASA will re-write the Pubic (global ) IP to the Private (local) IP. So querying and getting back 12.1.1.1 would be re-written to 10.1.1.1.
Palo Alto
From what I have been able to gather, PAN does not do either one of the above options (I could be wrong …. some newer version). They suggest doing split-DNS where you use an internal DNS server that resolved FQDNS to internal IPs while your external DNS resolved to the public IP addresses.
FortiGate can do this as well and frankly better since we can run a full blow DNS server on an interface to serve as the inside DNS server without needing to stand up a server.
UPDATE: Thanks to Jeff Wollach He pointed out that PAN does have this feature. Here is a link to read up on it.
Leave a comment
Recent posts
-

-

Have you ever had an IPS signature that continues... Full Story
-

Use case: Customer has a Split Tunnel Enabled but... Full Story

Hey Manny… Great write-up!! Actually, Palo Alto Networks has a feature called DNS rewrite that was added in PAN-OS 9.0.2 about 1 1/12 years ago. Check out the Knowledgebase article. https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClfjCAC&refURL=http%3A%2F%2Fknowledgebase.paloaltonetworks.com%2FKCSArticleDetail
Here’s the correct link. Sorry! https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-new-features/networking-features/dns-rewrite-dest-nat.html