There are many options when troubleshooting in FortiGate firewalls. ... Full Story
By Manny Fernandez
November 19, 2019
DNS over TLS (DoT) on the Fortigate
I recently wrote an article about the difference between DNS over HTTPS and DNS over TLS and the differences between the two. Now as promised, I will show how to configure DoT. Lets get started.
Requirements: FortiOS 6.2x
As stated above, you require 6.2x to configure this feature.
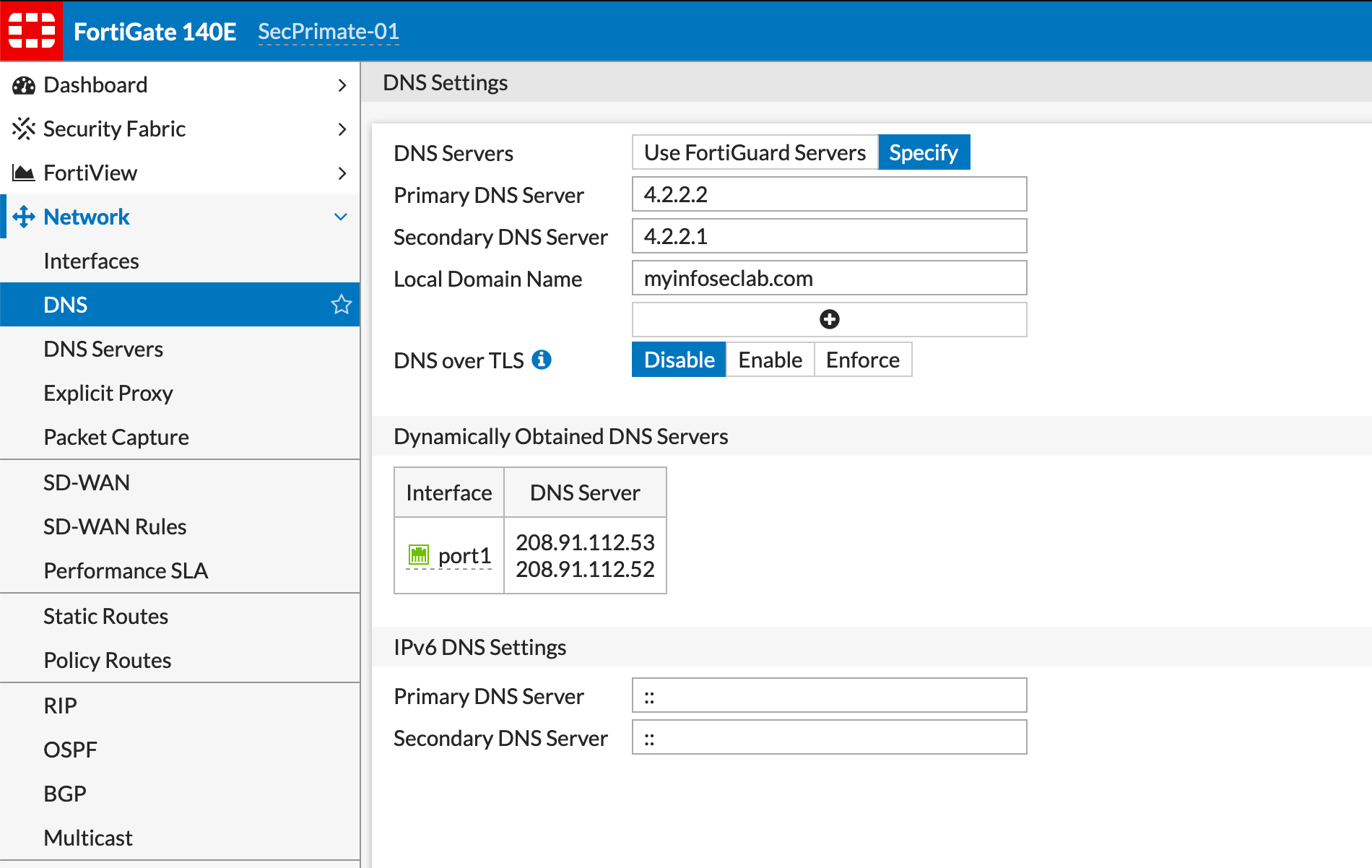
Here we can see the DNS over TLS is disabled, which is the default.
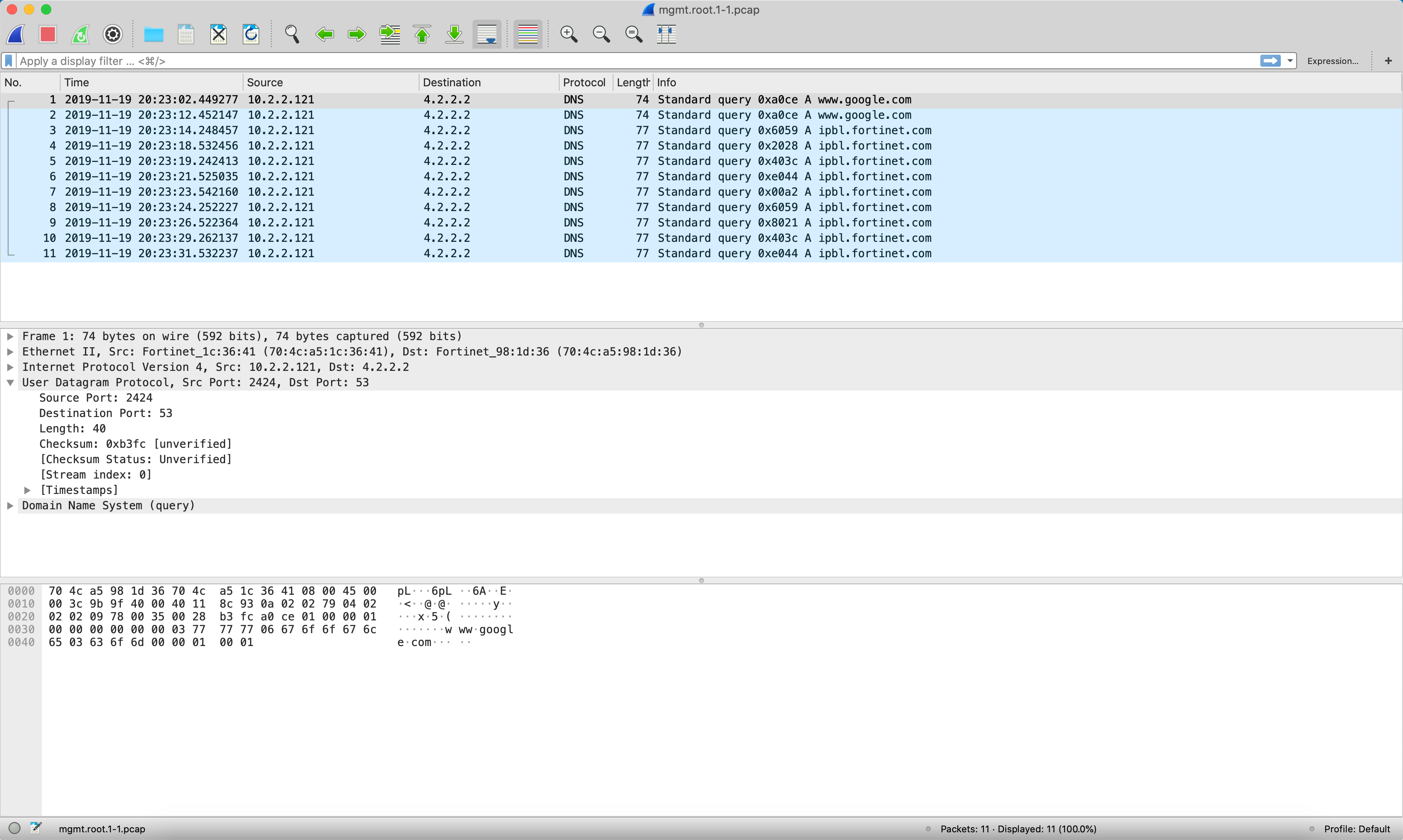
Here we can see a packet capture showing a standard DNS query. As you see this traffic is UDP 53.
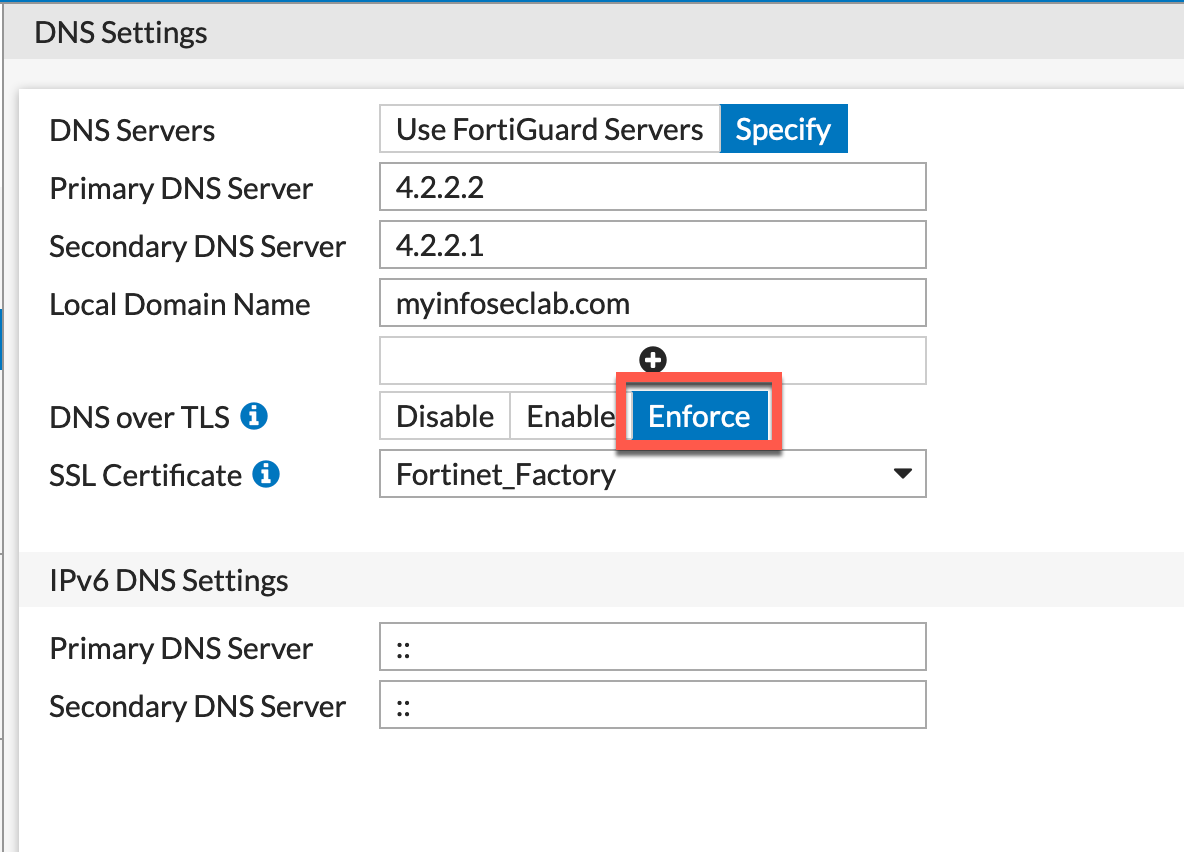
In the screenshot above, we can see that this is set up in Enforce mode which is Strict mode. You will need to choose the certificate you want to use from the drop down.
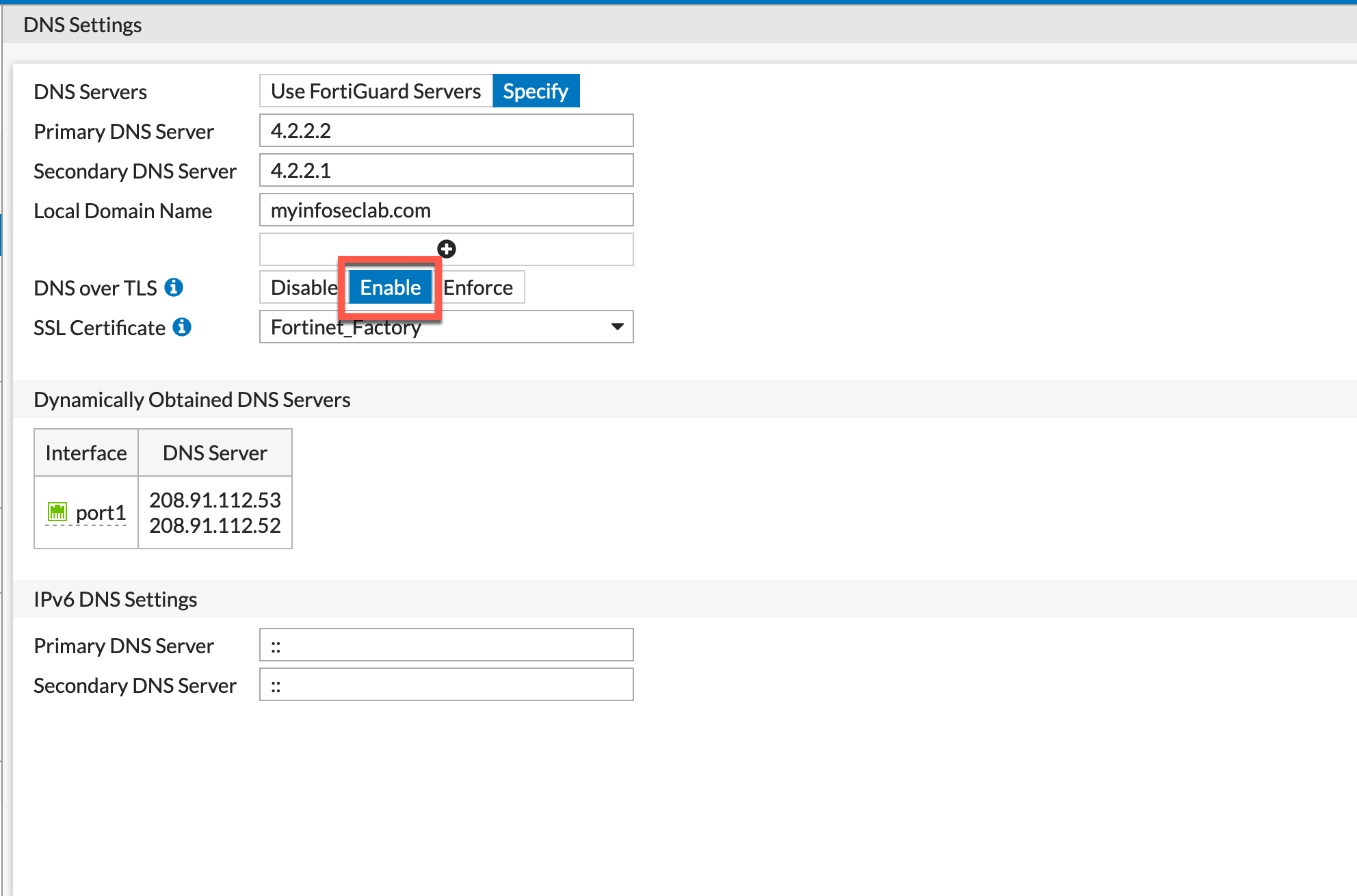
With the Enable option here, this is actually opportunistic mode. In this mode, the client will attempt to make a TLS connection on port 853 and if it fails, it will fall back to the standard UDP 53.
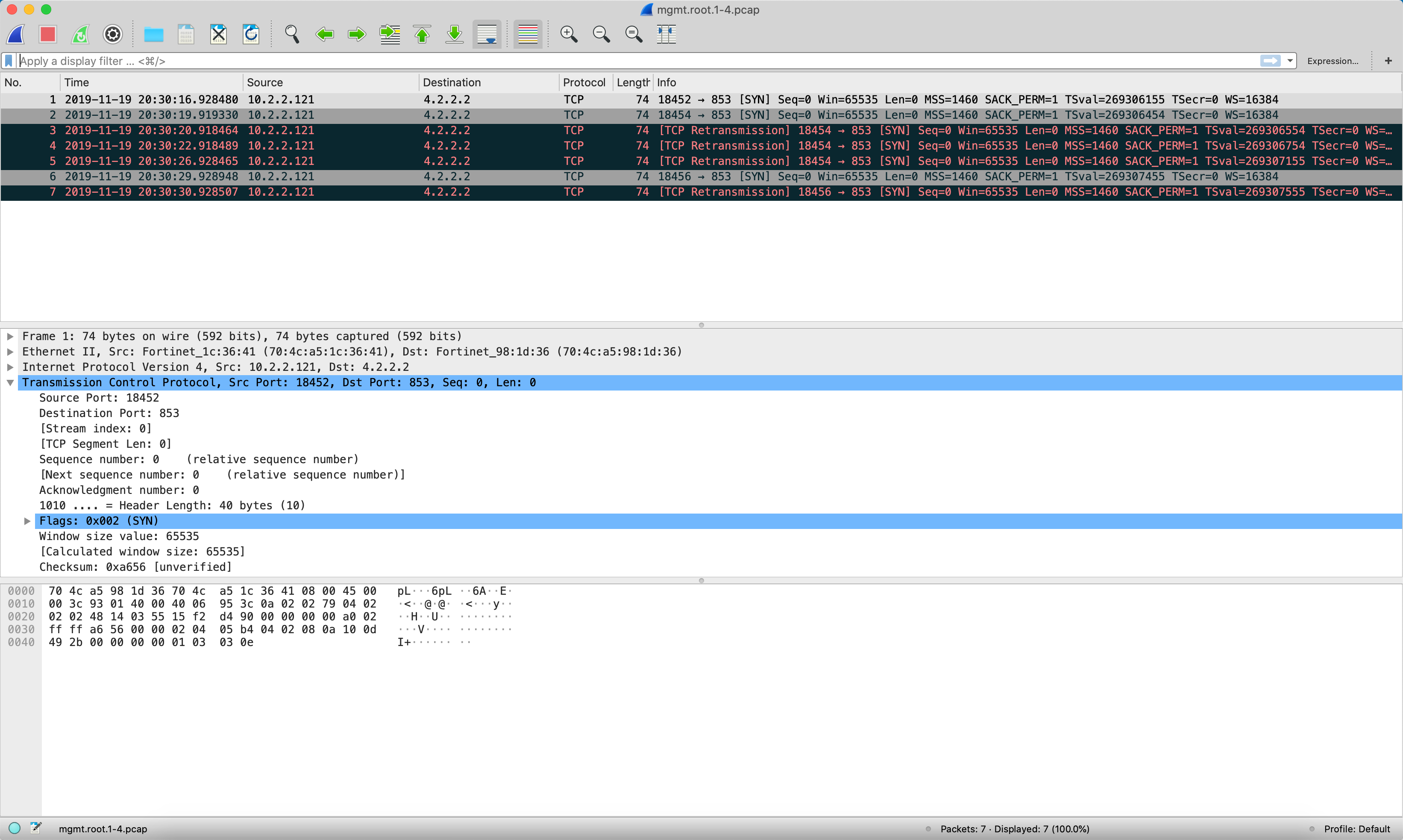
Here you can see the packet capture after turning on DoT. Notice it is using TCP and is using port 853.
DoH Blocking
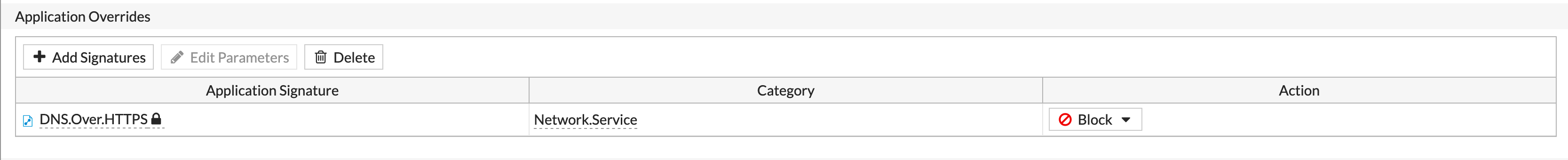
If you want to block DNS over HTTPS, Fortinet has a application signature for it.
Recent posts
-

-

Have you ever had an IPS signature that continues... Full Story
-

Use case: Customer has a Split Tunnel Enabled but... Full Story
