There are many options when troubleshooting in FortiGate firewalls. ... Full Story
By Manny Fernandez
October 21, 2016

Personal Information Security Hygiene Program
With today’s threat landscape ever increasing, it is important to practice good InfoSec Hygiene at work but equally important at home. Today we have everything on our computers, various cloud services or both. When I look back at my pictures since 2009, I cringe at ever losing them. I do not even have them printed out for the most part. In addition to that there are memories, documents, forms, music, movies, not to mention confidential information such as tax returns, banking statements, medical records and the like. Following these few recommendations will go a long way in protecting you from the basic attacks. In the event of a directed attack where someone has singled you out, there may be other risks at play outside of the scope of this post, but these are good starting points.
Passwords
I cannot say this enough about passwords. Password are an important part of your personal security program. It is important to NOT re-use your passwords. The reason for this is that you may go to a small e-commerce website (acme.com) and you enter your “standard” username and password that you use everywhere. After all, you can remember this password because it is the same at every site. Now, acme.com gets breached. The hackers will gather the hashed password or worst yet, the password in the clear and they will try them at most major sites (e.g. Dropbox, Gmail, Amazon, Facebook, Twitter, LinkedIn, Netflix etc). In some cases, if you use your corporate email, they may test access to your corporate network. Once they find a match, rest assured and are able to get access to your Gmail account as an example, they could reset password on all sites that are tied to your Gmail account. I use a password manager to keep track of my over 600 login credentials that are all unique.
1Password
1Password is the password manager I use. It works on Mac, Windows, Android and IOS. 1Password it is developed by AgileBites https://1password.com. Some of the features I use most:
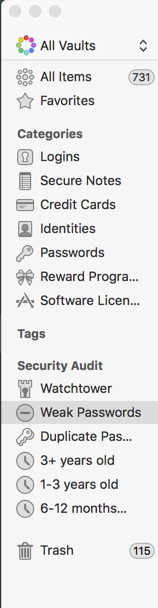 1Password can store much more than your passwords. It can store secure notes, software licenses, Credit Cards, separate password, credential combinations.
1Password can store much more than your passwords. It can store secure notes, software licenses, Credit Cards, separate password, credential combinations.
Watchtower
One of the most important features that I love is “Watchtower”. This is a service integrated into the product that constantly checks breached websites and compares them to your database. It will identify if you have passwords in those breached websites. It will warn you by giving you a visible red stripe across the top of the application.
Password Rotation
1Password also has a filter that will warn you of credentials that are duplicates as well as passwords that have not been changed in ‘x’ amount of time. By default the filters are (6-12 months, 1 years or 3 years). In addition to these features, 1Password will warn you of weak passwords.
Please note that 1Password is not the only Password Manager available. Some of the other password managers are:
- Lastpass – Lastpass is an online solution. It stores the password in the cloud.
- 1Password – 1Password is a local Password Manager but can use iCloud or Dropbox to synchronize.
- Keepass – Keepass is an opensource solution.
There is also an artcile on PCMagazine that covers additional pasword managers.
Password Security Questions
One of the habits I got into about 3 years ago is picking random answers for security questions. For example, “What college did you graduate from?” I would put anything from real universities, of which I did NOT attend, to made up ones such as ‘Table University’. Since 1Password can store more than just passwords, I normally take a screenshot of the crazy answers I did for the password/account to store in case I need to access the account later on.
SOCIAL MEDIA
Facebook – Facebook is a social media “forum” that allows you to post pictures, articles, links, videos and just comments (I know, everyone knows what FB is). They have the ‘Like’ button that you can use to show support for the post and recently, other options became available (e.g. Wow, love, haha, sad & angry). With the adoption of Facebook and other social media, it is very easy to reconnoiter someone.
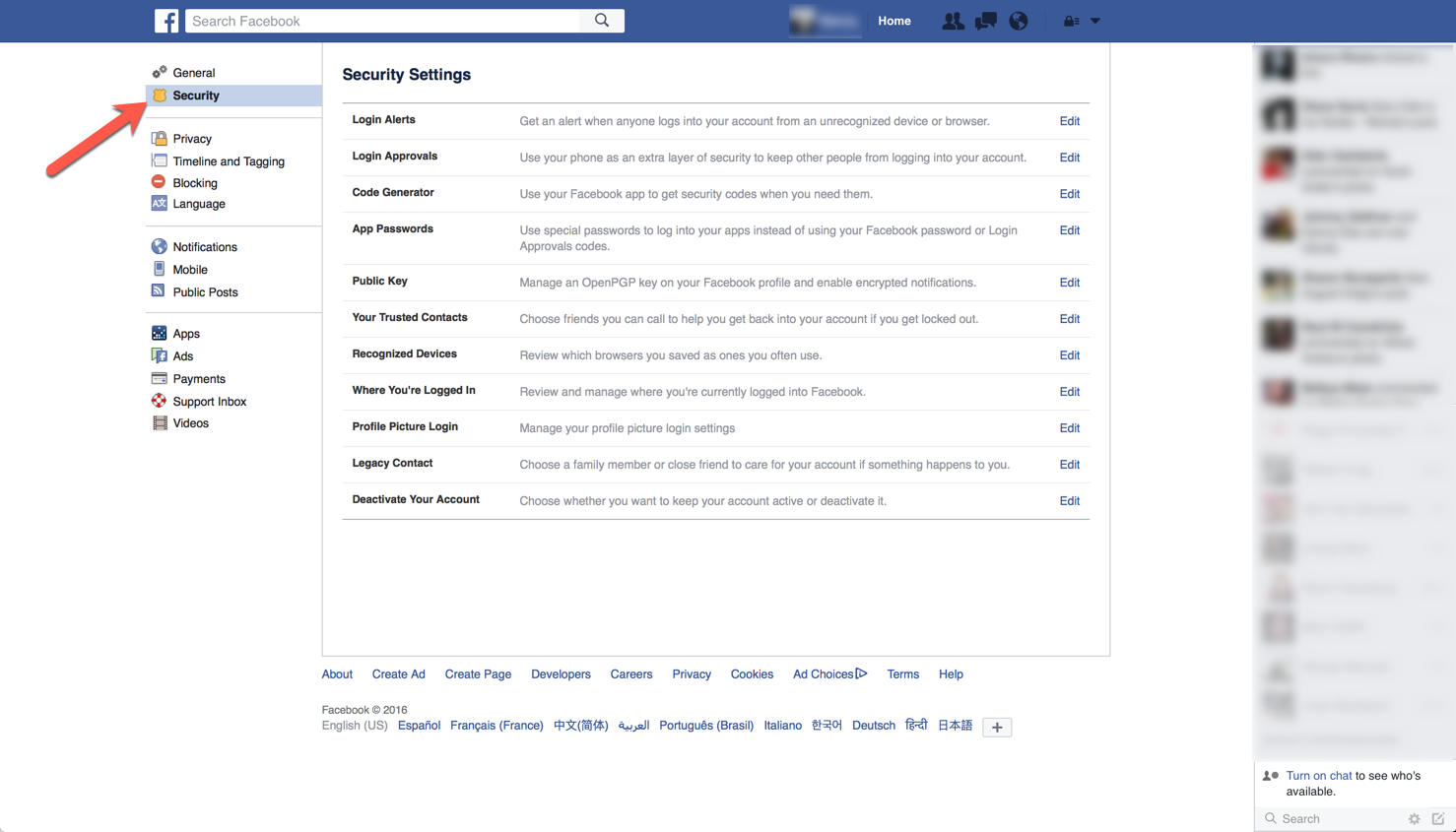
In Facebook, you should go to your ‘Settings’ and Choose ‘Security’. Here are some of the options available to you there:
- Login Alerts – Login alerts is a good idea because you will be notified if someone logs into your account from a non-trusted device. This is key in catching people who hijack your account.
- Login Approvals – By turning on this feature, you will be prompted to enter a code which is tied to a text message sent to your phone.
- Code generator – Is the ability to use a two-factor type capability with the Facebook app.
- App Password – Allows you to create a password for a specific application.
- Public Key – I use it, but if you are not proficient in PGP and use PGP of some flavor, this will not work for you.
- Your Trusted Contacts – Helps you unlock you account by using friends. Needless to say, you want to make sure you trust these people.
- Recognized Devices – It is a good idea to go through this list regularly. Remove any devices or applications that are no longer in use or applicable.
- Legacy Contact – In case you die, someone will be able to go in and post things on your behalf.
TIP 1 – Do not put your real information on Facebook regarding your birthday. You should get into the habit of using a fake persona for useless things such as birthday when validating an age requirement. You can do something like 2 months more or less and 2 years more of less. So if you are born on July 4th, 1972, you could use something like September 6, 1974.
TIP 2 – SPAM email account. It is wise to have a Gmail, Hotmail, Yahoo etc. mail account to be used with stuff you know you do not care about such as RadioShack. When they were around, if you gave them your email address, you would get ~5 emails per day. Set up an account you have the password to but not that it clutters you
Additional Security Settings
In addition to the information we have already discussed, there is the ability to require approval before allowing you to be tagged and who can see your posts.

- Who can see your future posts. This is important if you want to limit your visibility.
- Review all your posts and things you are tagged in, this is important because you do not want to allow anyone to tag you (or you may not). There may be an old TBT picture you are not comfortable with.
Shared Logins
You want to limit the services you use other credentials for. Given the opportunity to use your Facebook account to log into a web site, choose creating an account using your email. This keeps your important accounts safe. What inevitably starts to happen is that you use these important credentials on various sites and then you forget what site has access to your credentials.

Backups
How many backups should you have? As many as you can. With the introduction of ransomware in which the malware will encrypt all your data on your machine and sometimes any mapped drives as well, it is important to have not only backups but versioning. Versioning is the process of keeping multiple versions of a file and having the ability to restore the file at its various versions. Lets say that you have a Word document. You save this document as doc1.doc. You then modify doc1.doc by adding a period to it. Later you come back, you should have two versions of the doc; one with and one without the period.

I use a service called Crashplan. Crashplan is an online archival service. This should not be confused with Dropbox or Box as Crashplan does not allow you to share or collaborate. I pay $149.00 a year but have unlimited storage and up to ten computers. I back up my computers as well as my family’s computers. I have over 10TB in Crashplan. The beauty of this solution is that it automatically encrypts data locally and then syncs it to the cloud. Also, it will only backup the changes (deltas) making subsequent backups much faster. Here are some alternative solutions.
- Backblaze
- Amazon
- Dropbox
- Mozy
- Carbonite
You need to ensure that version history is turned on and/or available. In the unfortunate event that you are affected by a ransomeware, you can easily restore the non-encrypted version of your data. Some of these solutions do not allow you to backup external drive (e.g. USB portable HDD). This should be considered before purchasing the service and syncing all of your data.
Content Filtering

Cisco Systems acquired OpenDNS recently, however they still offer their free service. What OpenDNS does is, when your machines are using OpenDNS as their DNS service, you can configure it to block malicious sites. This is how it works. Lets say you are browsing and you enter www.goodguy.com as the URL. Your machine will send that query to OpenDNS. If OpenDNS returns a known bad guy IP, it will either redirect you to an OpenDNS website or sent you to a loopback address essentially blocking the site. It also protects you from fraud and phishing sites. The best way to configure this is to configure your device that hands out IP addresses (router/firewall) with OpenDNS.
Two-Factor Authentication
More and More, we are seeing cloud and online services offering multi-factor authentication. It is a good idea to implement 2-factor authentication. Some solutions offer an SMS or Text message with a code. GoDaddy, for instance will ask for your username and password and then it will send you a text message with a one-time password. Companies are moving away from tthe SMS technology and are moving more towards a service such as Google Authenticator.
Browser Security
The most common browsers available today are: Internet Explorer (AKA Internet EXPLODER), Microsoft Edge (included in Windows 10), Safari (Apple), Google’s Chrome and Firefox. There are others but they are obscure browsers or forks of Mozilla. Many of the attacks that affect machines are due to watering-hole attacks. These attacks are caused when users visit unsuspecting, otherwise benign sites that have either malicious content imbedded or served up from one of the advertisers. Although it does “break the experience”, it is important block content from automatically running. This can be Adobe Flash (one of, if not the most vulnerable code) & Javascript. I use an Apple MacBook Pro for my day-to-day and use Safari ‘ALMOST’ exclusively. I do not have Adobe Flash installed on my machine. When required, I use Chrome, which has its own flash integrated.
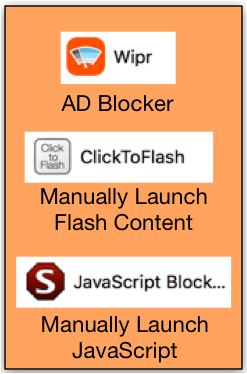
These are the extensions I am using on my Safari. There are counterparts on Microsoft and even Linux. Her is a link to a site that explains how to enable Javascript, Of course you should decide if this is what you want to do. I would also look at plugins that give you a little more flexibility because you can click on the tool bar icon and allow it to run from a site where you absolutely need it.
Social Engineering
I cannot tell you how many phone calls I have received claiming that “your computer is sending error messages to our SERVER”. Lets start with the basics, you computer is not using your telephone to connect to the internet (at least i hope it is not), there is no correlation between your computer and your phone number, more especially if they are calling you on your cell phone. This is a SCAM. NEVER give any information to ANYONE on an inbound call. ANYONE! Never give any information to anyone regarding information THEY should have if they are a reputable company that you have authorized to have your info (e.g. Banks, Insurance etc.) Microsoft is not going to call you about your machine connecting anywhere. Do not give these people any credit card information.
Pop Up Malvertisement
Sometimes when you are browsing, you will get a pop up saying that your machine is infected, or has been compromised etc. These are SCAMs. Do not click on them. Do NOT hit the ‘X’ or the ‘Cancel’. There are overlay attacks knows as ‘Clickjacking’ Check out this link if you want to dig deeper. These Malvertisements will not only charge your credit card, but will install malware and possibly even compromise your CC information. What can you do when you see this happen?
In Windows launch the ‘Task Manager’ by typing Ctrl+Alt+Del and choosing ‘Launch Task Manager’. Find the browser process and choose ‘End Process’ on the bottom right.
In macOS, type ⌘ ␣ (That is command and space bar) and type Activity Monitor, find the browser process and click the ‘X’ button on the top left.
In Linux, type Alt+F2 and then enter ‘xkill’ and hit enter. Find the process and click the ‘End Process’ on the bottom right.
Patches
Patches are software updates that fix vulnerable code previously released. This is the lifecycle: Company releases application —> users install it —> hackers and/or researchers find vulnerabilities in the code —> Company patches the code —> users install the update —> hackers and/or researchers find vulnerabilities in the code…. Rinse and repeat. Most of the exploited systems in breaches are caused by weak passwords and unpatched systems.
To enable automatic updates:
For Windows Computers, take a look at this link
For macOS / OS X take a look at this link
Encrypted Email
When you are asked to send any data over email that you do not feel comfortable in it being open to the world to see, you should consider using encryption. I use PGP for my secure email for the most part however it is mostly geared to techie/nerdy people because it does gave some complexities, not to mention that the recipient also need to have PGP. I also use a free solution that does a good job in a pinch. That solution is Hushmail.

Hushmail allows you to send email and attachments encrypted to a recipient without the need of exchanging keys. You DO need to provide a password. I recommend you taking a look at my blog on Self Destruct Messages. You can use that method to send a self destruct message containing the password.
There are other solutions you can use. Here is a link to a website that has some information on the different solutions. It is a little dated but you can take a look at it and make your oen decision.
Endpoint Protection
Today’s attacks are advanced. It is always a good idea to have good endpoint protection…. yes even on a Mac. There are many to choose from. If you are a Comcast Internet customer, you get access to Symantec Internet Security suite at no charge. There are other solutions available:
- McAfee / Intel Endpoint Protection
- Symantec
- ESET
Application Firewalling
Although some of the endpoint solution may come with Application firewalls, they may not be included in the license. On my Mac I use “Little Snitch” with ESET for basic AV and then for an Advanced Endpoint Protection, I use Cylance.

For similar fucntionality on the Windows side, I use GlassWire and McAfee (Corporate Standard)

OpenWiFi
Although it is extremely convenient to get to Dunkin Donuts or Starbucks (*$) and connect to the Internet without having to eat up your data bandwidth on your phone, it is EXTREMELY unsafe. It is not difficult for an attacker to lay in wait for unsuspected users to automatically connect to Open WiFi. There are cheap solutions such as WiFi Pineapple that can assist hackers in gaining access to your passwords and even your machine by impersonating the WiFi SSID. In order to protect yourself from such an attack, you should use a VPN. There are many of them on the market today. Some of these solutions are:
The idea behind the VPN is that it will tunnel all of your traffic through this VPN. Anyone locally connected will not be able to see you data. Obviously, if you connect through the VPN it will not secure traffic from your PC to that Website. It will however protect you from that Open WiFi.
Porn
OK, touchy subject but some people WILL watch porn. I do not judge that decision either way. If you are going to do so, you should use an iPad to do it. iPad uses advanced sandboxing that protects you from cross contamination such as in other operating systems.
Recent posts
-

-

Have you ever had an IPS signature that continues... Full Story
-

Use case: Customer has a Split Tunnel Enabled but... Full Story
