There are many options when troubleshooting in FortiGate firewalls. ... Full Story
By Manny Fernandez
January 28, 2019

Fortilink over TCP
If you are not familiar with FortiLink, you should get familiar with it. Fortilink allows you to manage FortiSwitches via the FortiGate GUI. This is great for remote offices and even access layers switches. Fortinet partners with the likes of Arista for larger “core” implementations. Please Note: Fortinet has partnerships with many of the switch manufactueres out there such as Cisco, Arista, and Brocade.
You can connect the switches directly to the Fortigate and manage them via a Layer2 connection, but sometime, this is impossible since Fortigates may be off site. We had a customer that had regional offices connected via MPLS to multiple remote regional offices within that region and the egress was a Fortigate. They managed the remote offices that connected to the regional office via Fortilink over TCP.
Lets get started.
NETWORK DIAGRAM
I labbed this up in my house and here is what I had:
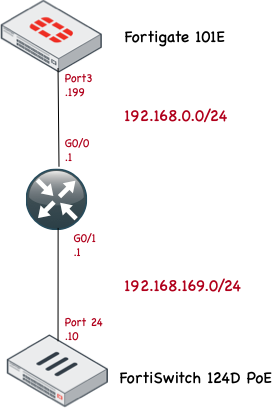
Nothing complicated for sure, just wanted to create a proof of concept.
Here is the configuration. This can be done either with DHCP or Static IPs. I only tested it with static, but I will update this post once I have validation that the DHCP works.
ON THE FORTIGATE
On the Fortigate, you will need to assign and IP address to the interface that will act as the Fortilink. In my PoC, I used port3 and 192.168.0.199/24 as the IP address and mask. Then you will need to ensure that ‘Dedicated to FortiSwitch’ is selected. It will disable most of the features you are acustomed to seeing.
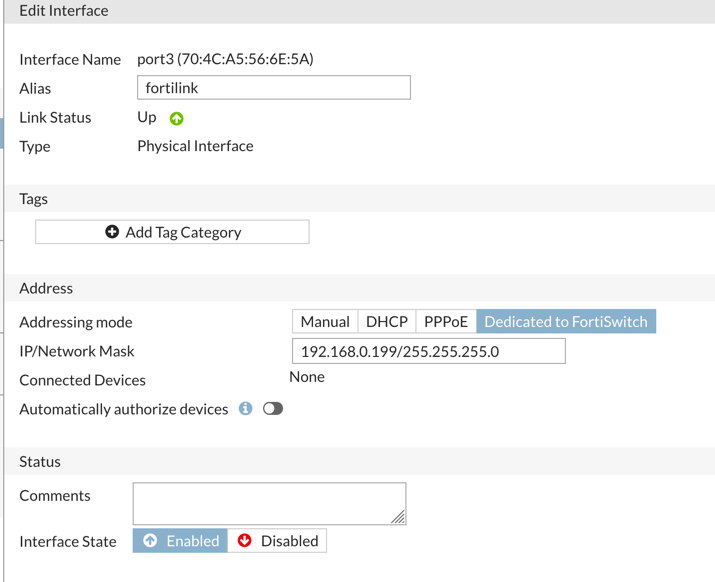
NOTE: Ensure that the Foritigate has routes (Either static or dynamic) to where the FortiSwitches are going to live.
Once this is configuredd on the Fortigate, you will not need to go back into it for a bit. Lets now move to the switch.
ON THE FORTISWITCH
On the FortiSwitch, you will need to either connect to the Management port (if applicable) or via the console. Either way, you will need to tell the switch that it is going to be in Foritilink mode.
NOTE: Remember that the FortiSwitches use 115200 as the baud rate
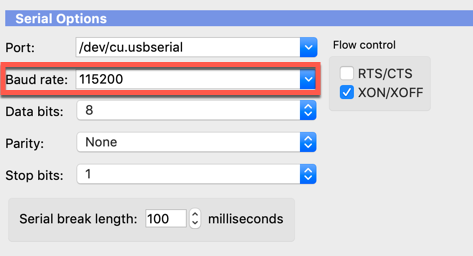
config system global set switch-mgmt-mode fortilink end
This will reboot the FortiSwitch
When the FortiSwitch reboots, log in again ‘admin’ no password, and then add the following:
config system interface edit "internal" set mode static set ip 192.168.169.10 255.255.255.0 set allowaccess ping https http ssh telnet next end
NOTE: Once this FortiSwitch is on the Fortigate, please set a password for the admin account on the switch
The ‘internal’ is the equivelent of VLAN 1 on a Cisco switch. All ports are part of ‘internal’ except for the ‘Management’ port, if your device has one.
Now you will need to make sure that the switch knows how to get back to the Fortigate
config router static edit 1 set device "internal" set dst 0.0.0.0 0.0.0.0 set gateway 192.168.169.1 next end
Next you will need set the NTP to point to the Fortigate
config system ntp set allow-unsync-source enable config ntpserver edit 1 set server "192.168.0.199" next end set ntpsync enable end
Now you are going to tell the switch, where the controller is located:
config switch-controller global set ac-discovery-type static config ac-list edit 1 set ipv4-address 192.168.0.199 next end end
Now finally, you are going to dedicate one of the ports to Fortilink
config switch interface edit "port24" set native-vlan 4094 set fortilink-l3-mode enable end
Now we are going to go back to the Fortigate
Once you are connected to the Fortigate GUI, go to ‘WiFI & Switch Controller’ and then ‘Managed FortiSwitch‘
You should see the ‘Authorize’ button and the switch in the background grayed out.
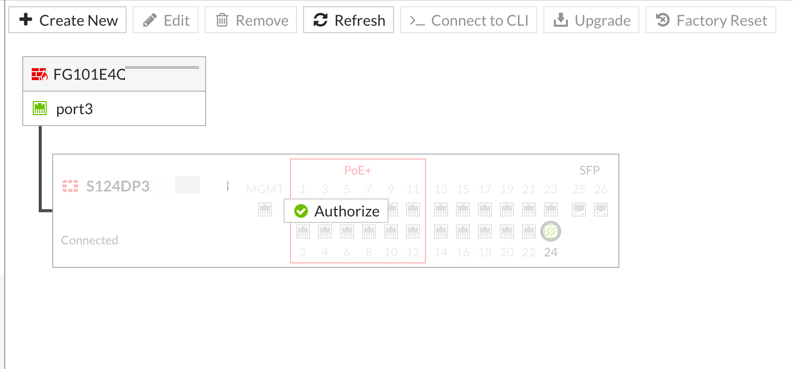
Once you click the ‘Authorize’, give it a little time and you should see the following:

For the DHCP configuration, you can use the following from a Cisco router that I played with:
ip dhcp excluded-address 192.168.169.1 192.168.169.10 ! ip dhcp pool FSwitch network 192.168.169.0 255.255.255.0 default-router 192.168.169.1 option 138 ip 192.168.0.199 option 42 ip 192.168.0.199 dns-server 4.2.2.2 8.8.8.8 option 43 ascii FortiSwitch !
Hope this helps.
Leave a comment
Recent posts
-

-

Have you ever had an IPS signature that continues... Full Story
-

Use case: Customer has a Split Tunnel Enabled but... Full Story

Hello, i read your blog from time to time and i own a similar one and i was just wondering if you get a lot of spam comments? If so how do you stop it, any plugin or anything you can suggest? I get so much lately it’s driving me crazy so any assistance is very much appreciated.
Funny Im responding now to this, but yes there is a plug in and acutally you can turn off comments on the posts